Posted
The cybersecurity industry has reached an inflection point. According to the Forrester Buyer’s Guide: Cyber Risk Quantification Solutions, 2025, organizations are moving beyond theoretical discussions about cyber risk quantification (CRQ) and focusing on operationalization. But what does it really mean to put CRQ into action, and why are so many companies wishing they’d started sooner?
From Theory to Action: The Operationalization Challenge
One of the most significant findings from recent CRQ research is that customers are actively working to operationalize their risk quantification efforts better. The question isn’t whether CRQ has value; it’s how to make it work in the real world, day after day.
When organizations consider implementing a CRQ solution, they face a fundamental choice: How much do they want to rely on manual, subject matter expert-driven approaches versus automated, data-driven methods? This decision directly impacts how effectively they can operationalize risk quantification.
The distinction matters. Walking into a board meeting and saying, “These loss estimates come from actual insurance industry data – here are the peers, here’s the methodology,” creates instant credibility. Compare that to saying, “Well, someone on our team told us this number feels right.” Operationalization is fundamentally about trust and data.
What CRQ Really Means: Prioritization, Not Just Numbers
At its core, CRQ addresses a critical problem: assigning a dollar value to every security improvement an organization makes. This enables something every security leader desperately needs, and that is the ability to prioritize what matters most in a world of limited people, limited time, and limited budgets.
CRQ isn’t about producing theoretical reports about once-in-a-million black swan events. It’s about continuous, actionable insights. Today’s top 10 priorities. Tomorrow’s top 10 priorities. This creates the ability to manage risk at executive, strategic, and operational levels simultaneously, linking risk management from the boardroom to the technical implementation.
The Evolution of CRQ Use Cases
The research reveals how CRQ applications have evolved significantly. Initially, organizations used CRQ primarily for basic risk quantification and budget justification. Today, the focus has shifted to dynamic, operational, enterprise-focused use cases, including:
- Executive reporting
- Cyber insurance optimization
- Continuous risk monitoring
These seem like independent use cases, but they’re completely intertwined. Consider this scenario:
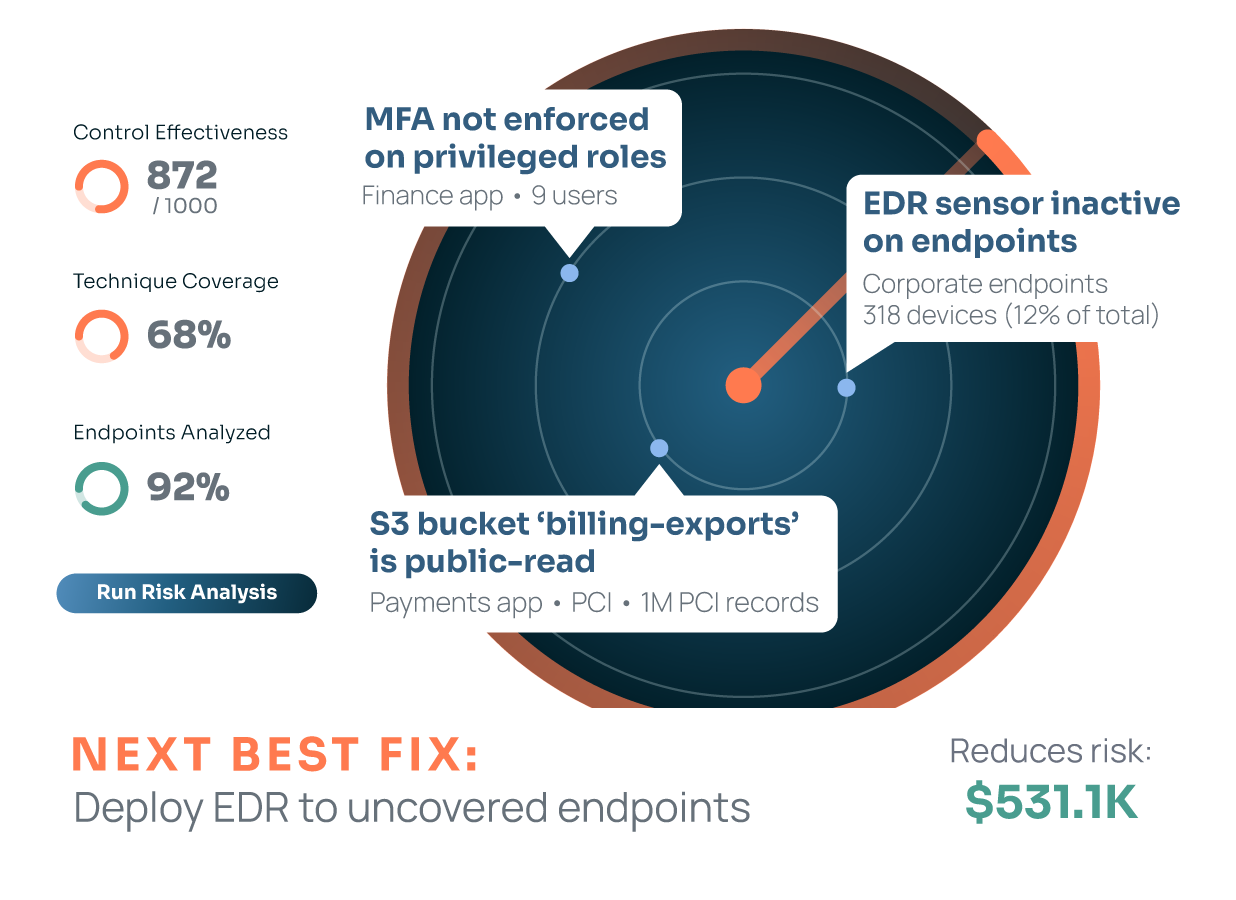
A security team discovers that not all business owners have implemented multi-factor authentication (MFA), which increases breach likelihood from 25% to 50%, creating a potential $50 million exposure. Rolling out MFA would cost $500,000 and reduce risk by $25 million. That’s a very strong ROI. But the business declines due to user friction concerns.
The security team can now present the board with clear options: invest $500,000 in MFA, or increase cyber insurance coverage by $5 million to cover the delta. This transforms the conversation from technical controls to business trade-offs, making security an enabling function rather than a blocker. The insurance optimization use case and continuous risk monitoring use cases are intertwined, and quantifiable risk makes these decisions at the operational, strategic, and executive levels informable.
The Cultural Transformation: From Guesswork to Data-Driven Decisions
Perhaps the most exciting finding is that CRQ drives cultural transformation, shifting organizations from qualitative guesswork to data-driven financial insights. This enables genuine cross-team collaboration and proactive decision-making.
Nearly all surveyed CRQ users reported that they wished they had started sooner. What are non-users missing?
Strategic Participation: Traditionally, security does not participate in the same strategic conversations as marketing, sales, or R&D, because security is not what the business does. It is an enabling function. Without CRQ, security reports metrics that don’t matter to the rest of the business. CRQ changes that by enabling security to speak the universal language of business impact, making it a strategic part of helping the organization accomplish its mission.
Better Outcomes: The IBM Cost of a Data Breach report shows that organizations using CRQ experience both lower likelihood and lower impact of breaches by double-digit percentages. They’re tackling the right problems at the right time.
Breaking Down Silos: CRQ forces collaboration between traditionally separate teams. Risk teams often don’t talk to threat teams, despite the fact that threat and risk go together like peanut butter and jelly. You can’t measure threat effectively without understanding the impact and whether compensating controls exist.
Consider this analogy: If you live on a hill and someone tells you to buy flood insurance, the answer is probably no. Your natural defenses against flooding are strong. Similarly, if a vulnerability exists in the wild but you don’t have the affected system, it doesn’t matter to you. If you have the vulnerability but also have appropriate compensating controls, it doesn’t matter. And if two threats exist, but one targets a low-revenue system while the other targets a critical one, you know which demands attention.
Linking risk quantification and threat intelligence at the operational level gives you the data to either say “I have a compensating control and I can ignore this” or “I don’t have a compensating control and it’s high impact.”
The 360-Degree View: Internal Meets External
True security requires understanding both internal and external perspectives. Organizations need to know:
- Internal threats they’re facing
- Controls they have in place
- External threats in the wild
- Whether those external threats have escaped internal detection
With the recent acquisition of ThreatConnect by Dataminr, we will be combining internal monitoring with external data sources – including deep and dark web intelligence, vulnerability databases, and threat intelligence – to enable organizations to achieve a complete 360-degree holistic view of risk and threat with compensating controls factored in. This comprehensive picture enables truly informed decision-making.
The CRQ Advantage: Why Organizations Wish They’d Started Sooner
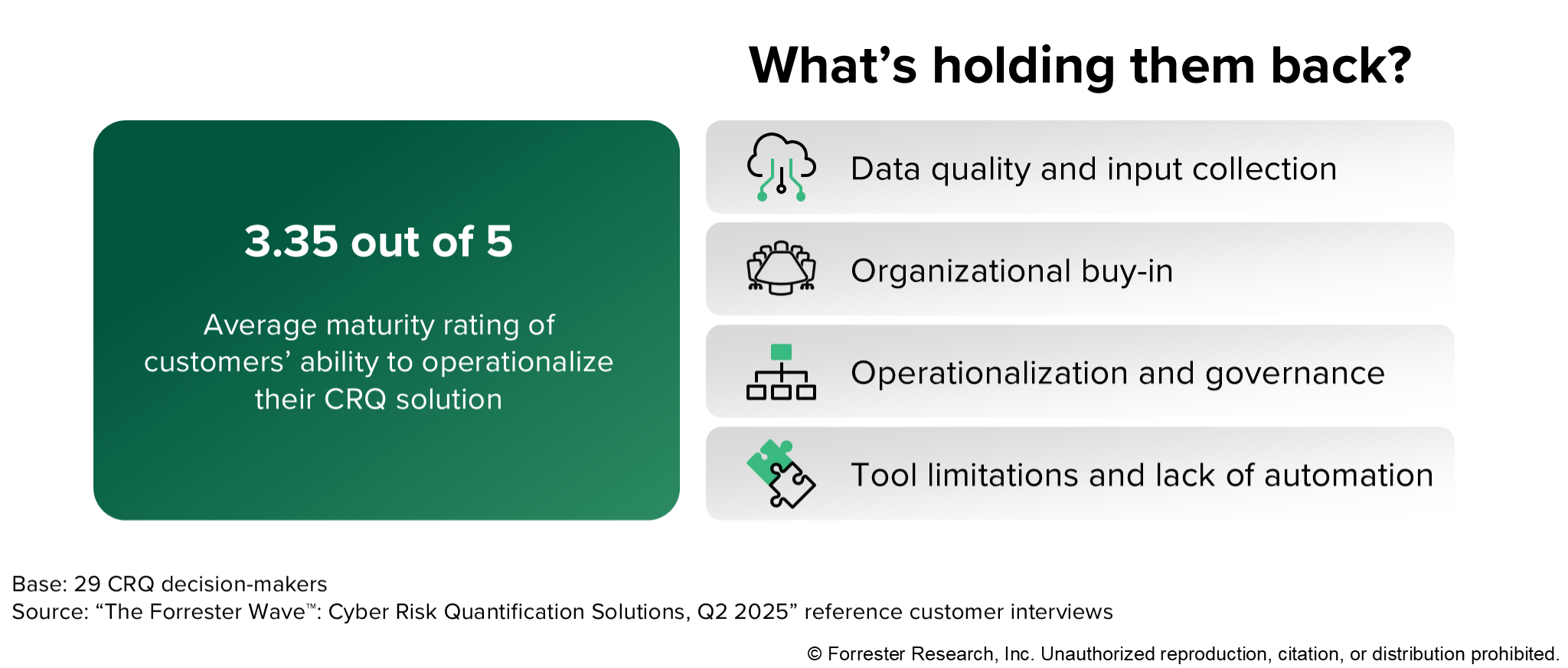
CRQ represents more than a technical solution. It serves as a catalyst for cultural transformation toward data-driven decision-making. Organizations gain strategic participation in business conversations, achieve double-digit reductions in breach likelihood and impact, and break down silos by combining internal and external threat perspectives. Yet despite these benefits – and nearly all users wishing they’d started sooner – many organizations struggle to operationalize CRQ effectively. In our next post, we’ll tackle the practical challenges holding back CRQ maturity, from resource constraints and education gaps to data quality issues, and explore how automation, pre-built models, and smart integration strategies can help organizations overcome these obstacles and accelerate their journey from theory to measurable results.