Posted
Analysts are overwhelmed by a number of things: the thousands of alerts they receive in a day, the intricacies of hidden details in email messages, embedded links, and attachments, or the inability to control users clicking on malicious materials. Managing the volume of emails and understanding trends in attacks is unwieldy as security teams grapple with knowing how to prioritize them.
Without the helpful context and insight of threat intelligence and orchestrated automated processes to guide workflows, analysts can prolong their response time while trying to prioritize, and harmful attacks can spread through their organization without timely action.
The solution may be easier than it seems, by combining a Threat Intelligence Platform (TIP) and Security Orchestration and Automation Response (SOAR) platform. An Intelligence-Driven Operations Platform (SOAR + TIP)
Where Do You Start?
Collecting intelligence to understand an attack from all angles is vital to any security response plan. However, prioritizing attacks by their severity can be difficult without all the necessary context. A central platform that allows prioritization by risk level is critical, as is the capability of having a place to store previously known intel or newly acquired intel. The real game-changer is Workflow. Workflow allows security teams to investigate, track, and collaborate on information related to threats and incidents with automated and manual tasks and standardized consistent processes. In high-risk phishing scenarios like spear-phishing, emails should be escalated to coordinate defensive measures required to respond appropriately and in a timely manner.
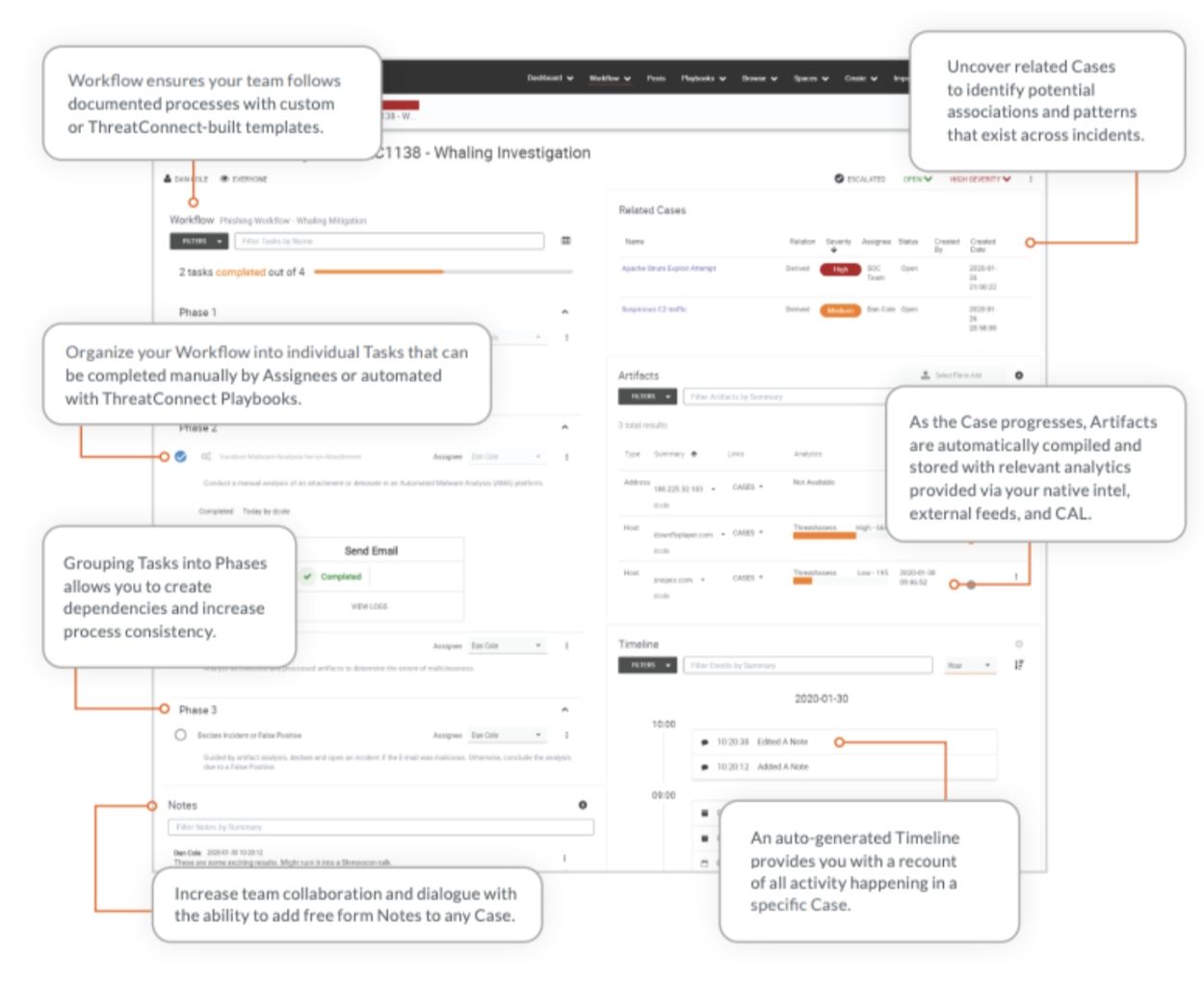
By utilizing this solution, Cyber Threat Intelligence (CTI) Teams and Security Operations (SecOps) Teams are able to prioritize their time and efforts which helps reduce the time it takes to work through a large number of phishing emails. CTI teams have the strategic position to discover if the organization has been penetrated by an attacker and attempt to collect information about the attack to share with the SecOps team for further action. The SecOps team can then take any corrective actions based upon what was learned about the attack in order to reduce the risk of further similar exploits. This helps both teams reduce the time it takes to work through a large number of phishing emails and get accurate and up-to-date information pertinent to the phish.
To fully unleash the power of your security team, you need an all-encompassing platform that can automate analysis, triage, and collect intelligence from phishing emails to process, categorize, and respond to suspicious emails.
How Can ThreatConnect Help?
ThreatConnect’s SOAR platform has a revolutionary intelligence-driven approach to SOAR which means our Threat Intelligence Platform (TIP) is baked right in. By combining these into one platform, we create a symbiotic relationship between Intelligence and Operations, enabling more accurate, efficient, and faster decision-making with Intelligence-Driven Operations (IDO).
ThreatConnect provides knowledge of current and emerging threats, which enables analysts to examine strategic and operational intelligence from sources outside of their organization and match it with existing log sources. Combining this intelligence with an orchestration and security platform delivers clear benefits:
- Reduces Time to Complete Analysis
- Immediate Access to Additional Context
- Automates Necessary Corrective Actions
The combination of automated and manual tasks in one single platform ensures efficiencies are introduced where possible while allowing human intervention when necessary. This helps reduce the time it takes to work through a large number of phishing emails with templatized workflows. Furthermore, with the capability and power of collective threat intelligence and analytics within ThreatConnect, your TI team gets immediate access to additional context and accurate, up-to-date information pertaining to the details of the phish. Coming full circle, after learning about the phishing attack, your SecOps team is able to take corrective actions (such as implementing a new control or suggesting policy modifications) to reduce the risk of further similar exploits.
With ThreatConnect, increase efficiency and bolster staff productivity by automating analysis and quickly escalating high-risk emails to better coordinate defensive measures required to respond appropriately.

