Posted
As someone in Customer Success for ThreatConnect, we are constantly asked to push the limits of our creativity for a customer. The Playbook below is the result of such a request. So without ado, I present Get all available information from JIRA!
The prerequisites that you will need for this Playbook:
- URL to JIRA Instance
- Credentials for JIRA
- A custom attribute “JIRA Ticket ID” (case sensitive)
These can be configured in the following steps in the Playbook:
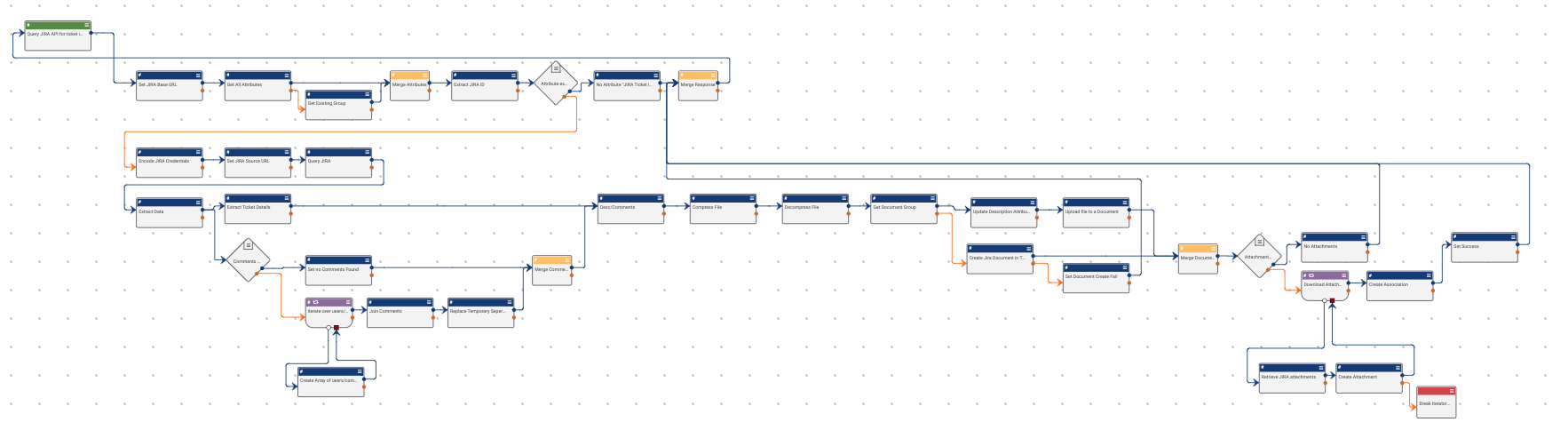
Set JIRA Base URL
With your Base url including protocol:port designation without a trailing / :
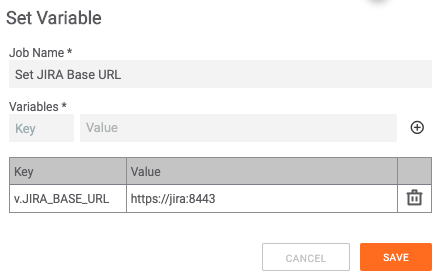
Encode JIRA Credentials
With the username/password keypair to authenticate to JIRA:
What makes it work?
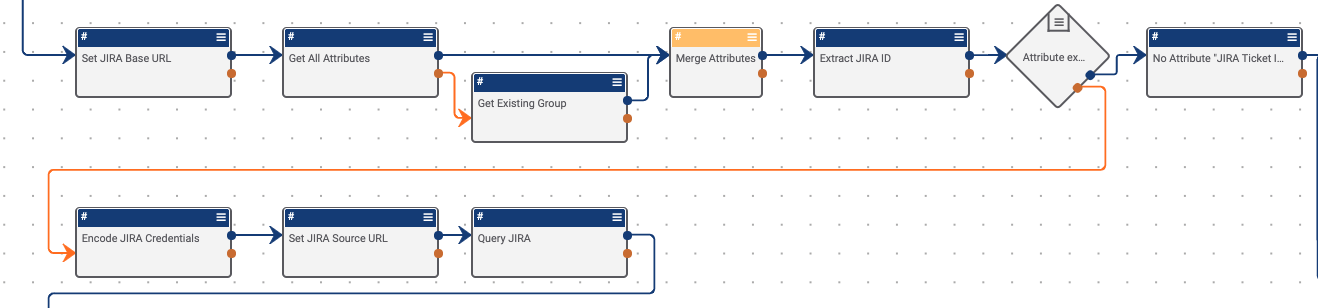
The Playbook at first will start by retrieving and then validating that the attribute exists on the group or indicator. If it does not, the Playbook will exit and will inform the user that the attribute is missing:
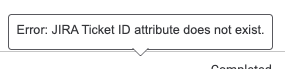
If it does exist then it flows down to the next step where in we query JIRA’s API for all available information that it can give for the provided ticket ID:
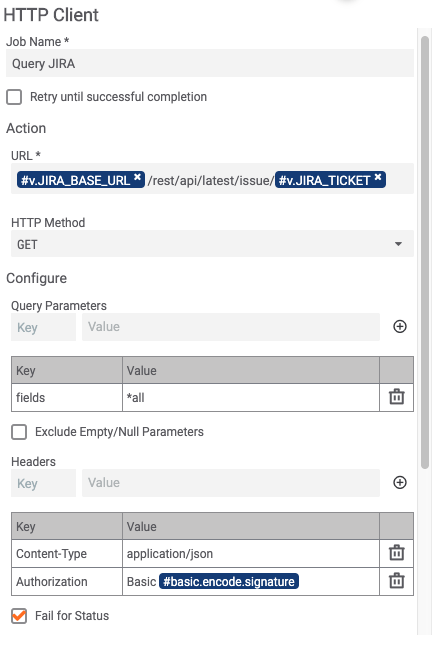
This JSON response is then passed over 2 JMESPath apps. The first one will filter out the description, any comments and attachment URLs, and attachment filenames. Note that we are extracting some of this as a String and a StringArray for condition handling in follow-on steps.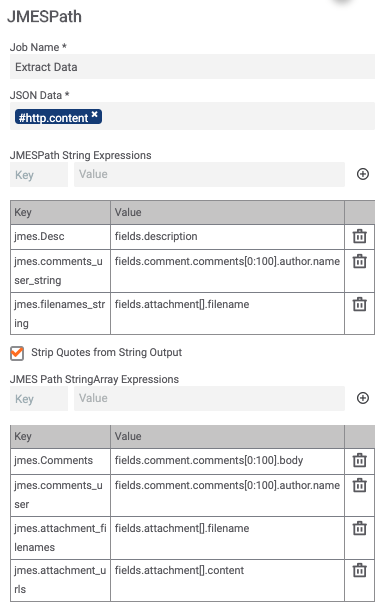
The second JMESPath filter we are extracting out is the Issue Type and Priority contained in the JSON response.
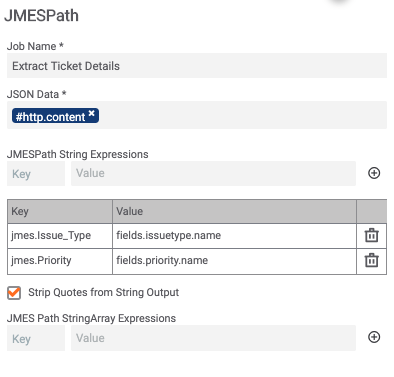
The next items that in the Playbook is formatting the extracted items from the JSON to a more human readable and displayable version.
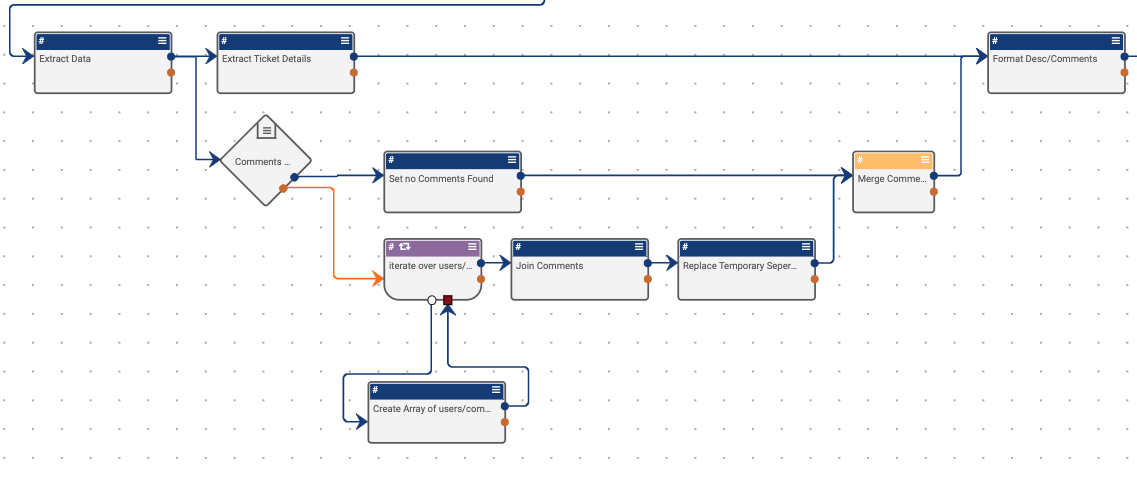
The next step in the Playbook is updating the document in ThreatConnect, if it exists. If it doesn’t exist, then we can create it, and upload the document contents which is created to hold the JIRA information that was extracted previously.
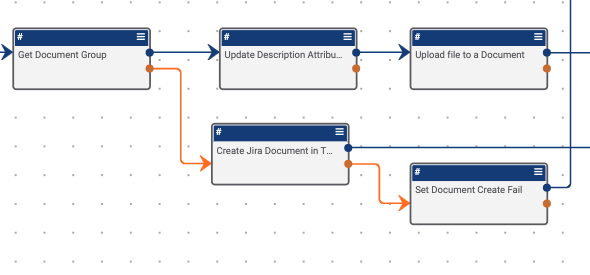
Then we check if there are any attachments to the ticket. If there are attachments we iterate over them, then save and associate them accordingly. If there are no attachments, we create and send the response back to the user initiating the User Action Trigger.
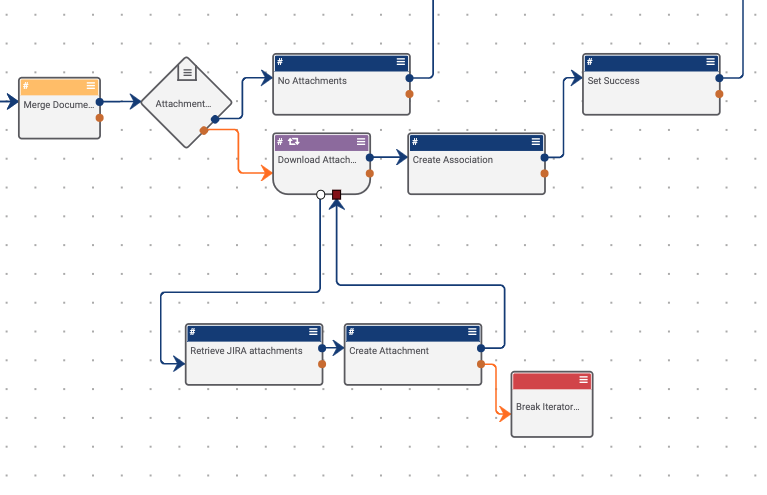
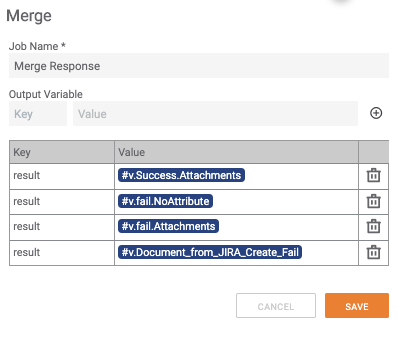
Within the merge that connects back to the trigger, we gather the different messages that can be returned back to the user as we’ve handled any errors that could occur.
How do I use this?
After performing the configuring steps above and enabling the Playbook, you will need to ensure the required attribute is on a group or indicator.
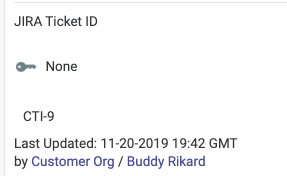
The Attribute JIRA Ticket ID
Added to any indicator or group object with a JIRA ticket ID:
After those items are in place and activating the Playbook in the User Action card on any indicator or group object, you will see this:

If there are any errors when executing the Playbook, they are returned to you. On a successful execution you will receive a message like the below:
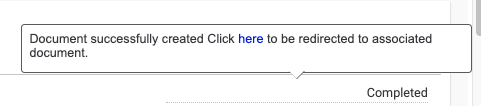
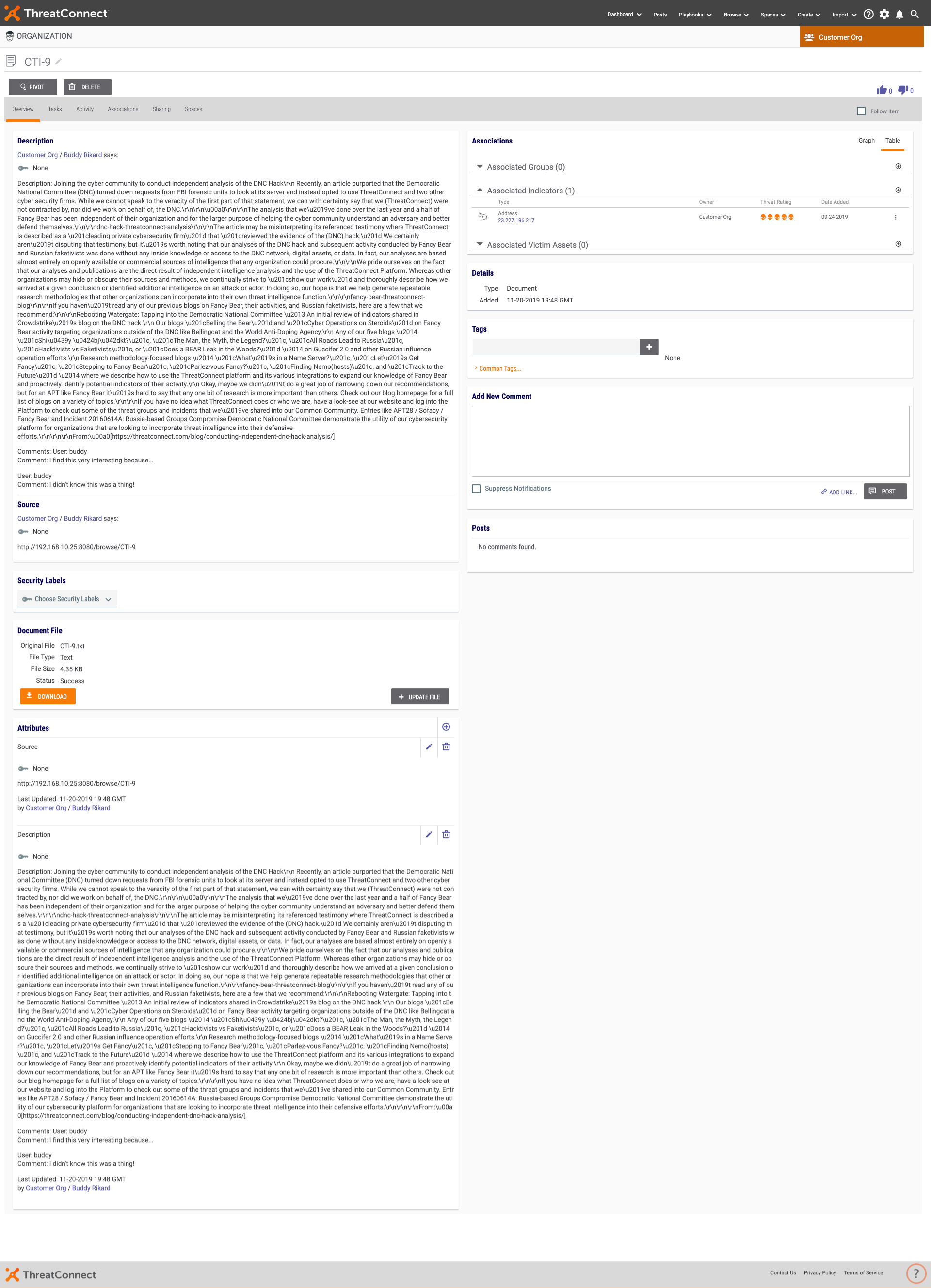
Clicking the blue link “here” you will see the newly created group object:
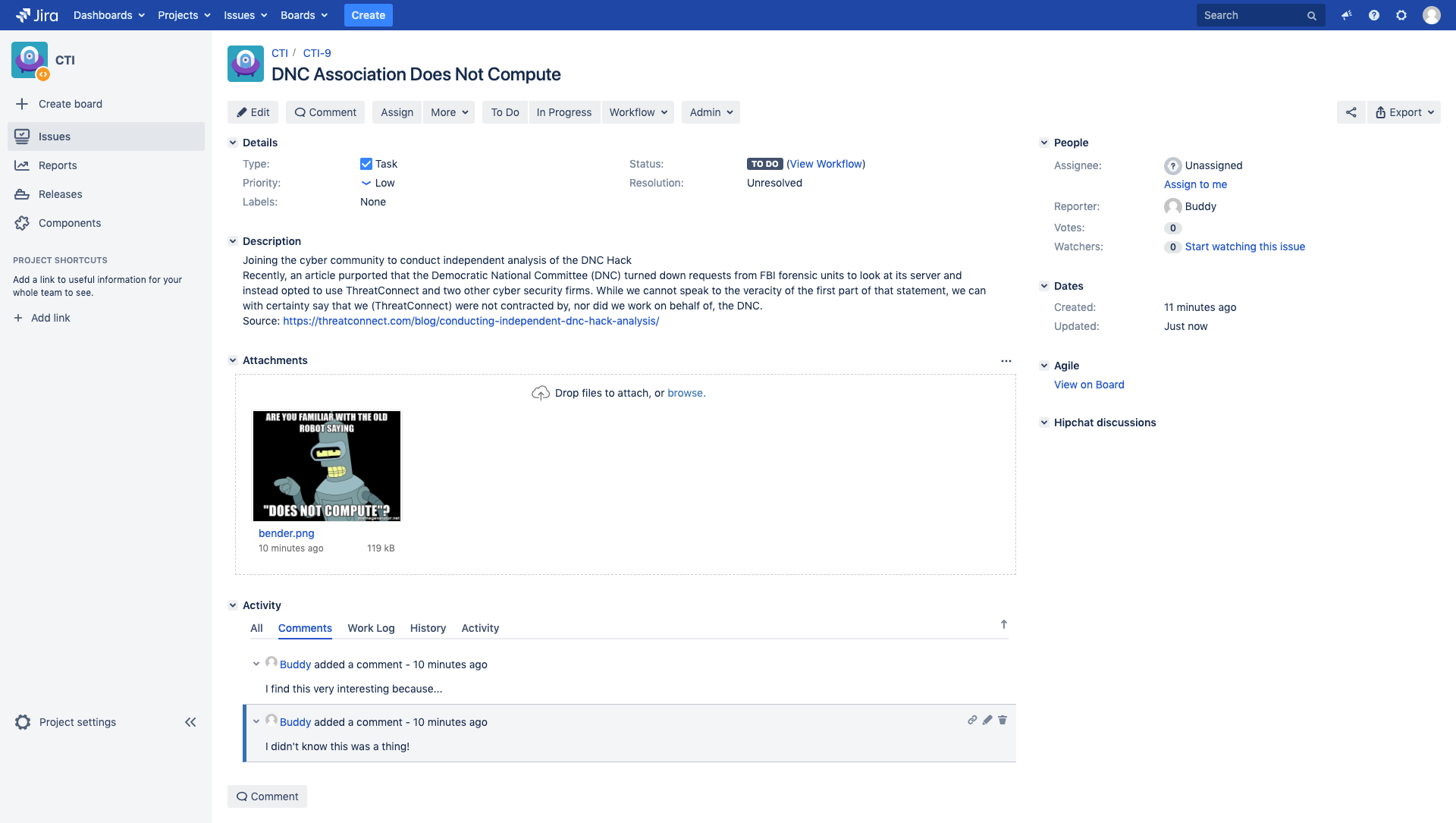
For a comparative view, this is how this looks in JIRA:
See this Playbook in Github, here.