Posted
Querying GreyNoise’s both free and paid APIs to retrieve insights on IOCs for alert triaging and filtering purposes
Analysts get inundated with alerts from all sorts of activity; both targeted and also part of widespread activity such as mass port scanning, crawlers, search engines, etc. Our customers wanted a way to use GreyNoise data from within the ThreatConnect Platform to filter out Address IOCs and alerts that are not specifically targeting them.
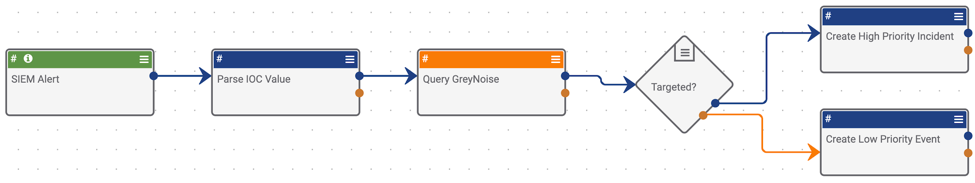
We tend to see users validate and filter alerts through GreyNoise before performing any subsequent investigation as a way to lower the amount of alerts they need to respond to. So we built a Component that can be triggered any way a user wishes. Components are independent pieces that can fit into any larger Playbook workflow. The GreyNoise Components were designed to help analysts leverage GreyNoise data in their workflow so that they can filter out low priority alerts and not waste time, money, and effort pursuing activity that doesn’t have high impact to their organization.
The enrichment Components will take an address IOC and query GreyNoise’s API to retrieve any available information they may have on the given indicator. These Components were designed to allow a user to query for relative IP address IOCs as well as retrieve enrichment information that can then be turned into insights to help “filter out the noise”. The GNQL Component allows the user to craft a query using GreyNoise’s built-in query language to retrieve matching addresses.
Some really useful examples of utilizing GreyNoise data in Playbooks:
- If benign: decrease the severity of the alert or completely disregard it
- If the IOC has not been seen in GreyNoise, increase severity and enrich with other sources
- If seen in GreyNoise AND unknown or malicious AND hitting the perimeter: reduce severity (or, just do not alert)
- If seen in GreyNoise AND there is egress communication (your network is talking TO an IP in GreyNoise) this is very bad
- If successful login from GreyNoise malicious IP: this is VERY bad
Below is a screenshot of a sample workflow using the GreyNoise Enterprise Enrichment Component: