Posted
John Locke, a wise man, once said, “No man’s knowledge here can go beyond his experience.”
The same is true with the latest release of ThreatConnect that includes quite a few new features. The feature that has me excited the most is the AppBuilder functionality. The primary reason is that I can see the full potential, when in the right hands, for someone to develop an application to fully extend the Platform to meet their organizations needs at a lightning fast pace. The secondary — selfishly — is that learning Python is one of my goals for this year.
I can’t think of a better way to achieve both of these other than by combining them and achieving more goals within the same time. With that, here’s the AppBuilder project, “Generate Intelligence Report”:
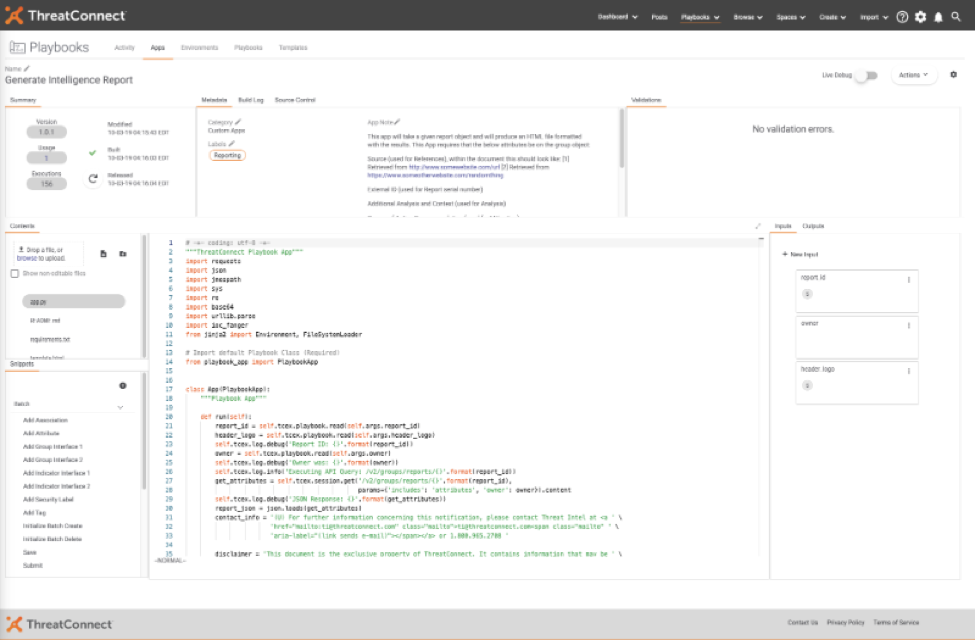
Along with the Playbook “Generate Report”:
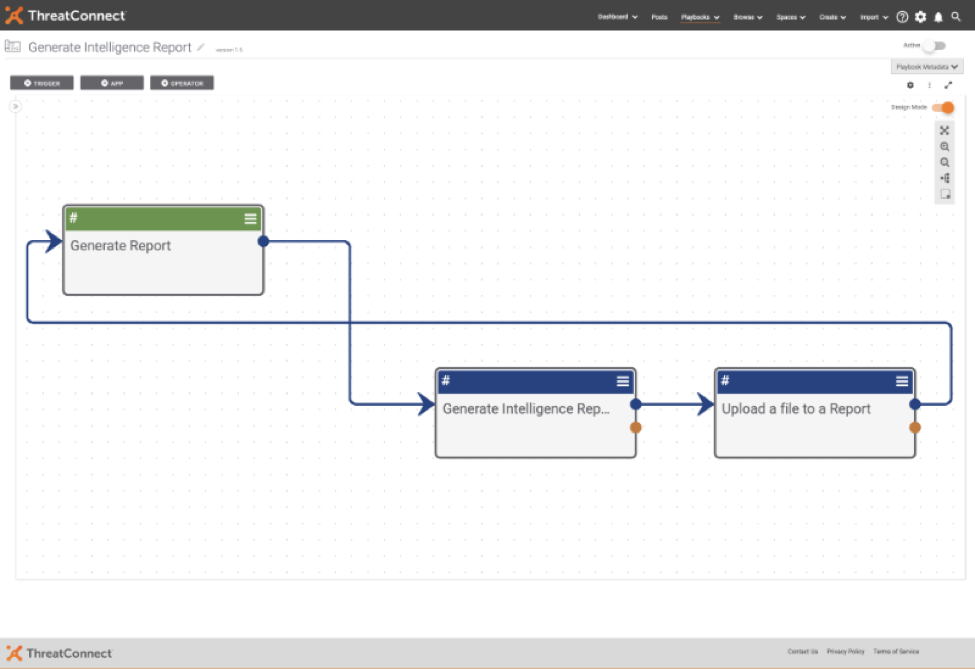
The custom app itself is very simple in regards to inputs as it takes in:
- A report ID (this can either be a String or TCEntity, if a TCEntity is used, Owner is ignored)
- Owner Name
- URL for your Company’s logo which this defaults to the ThreatConnect logo
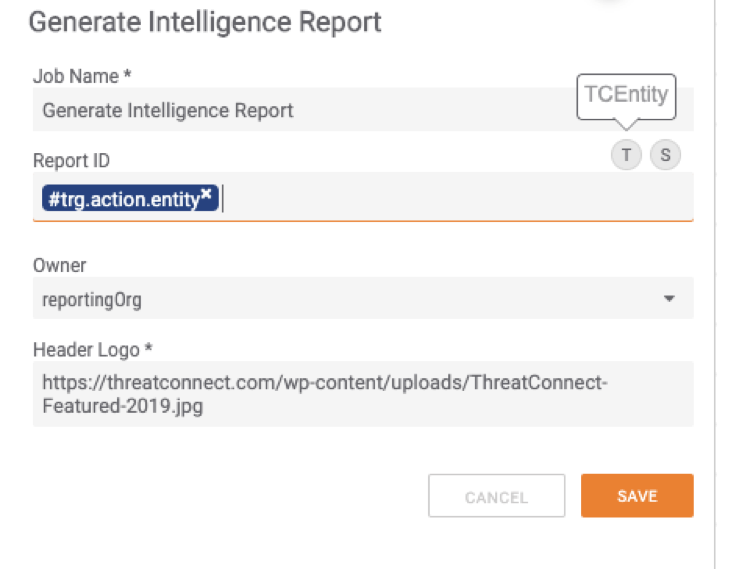
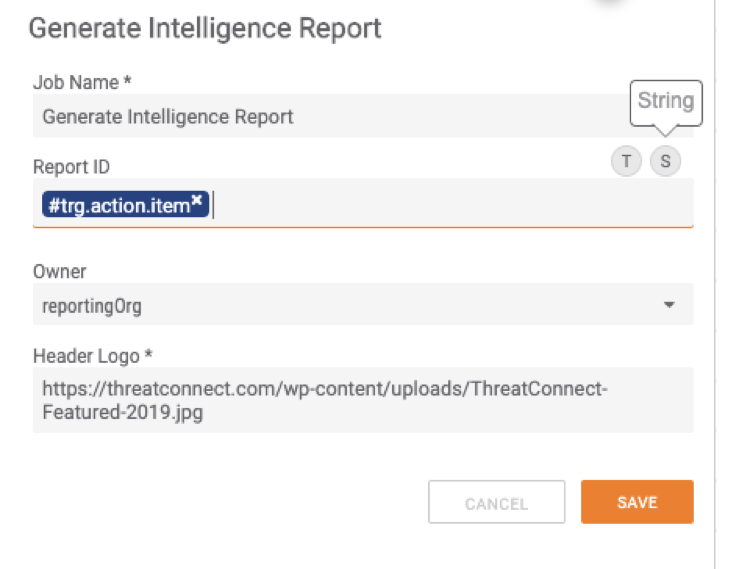
The outputs from the app are:
- An HTML Report (binary type)
- An HTML Report (string type)

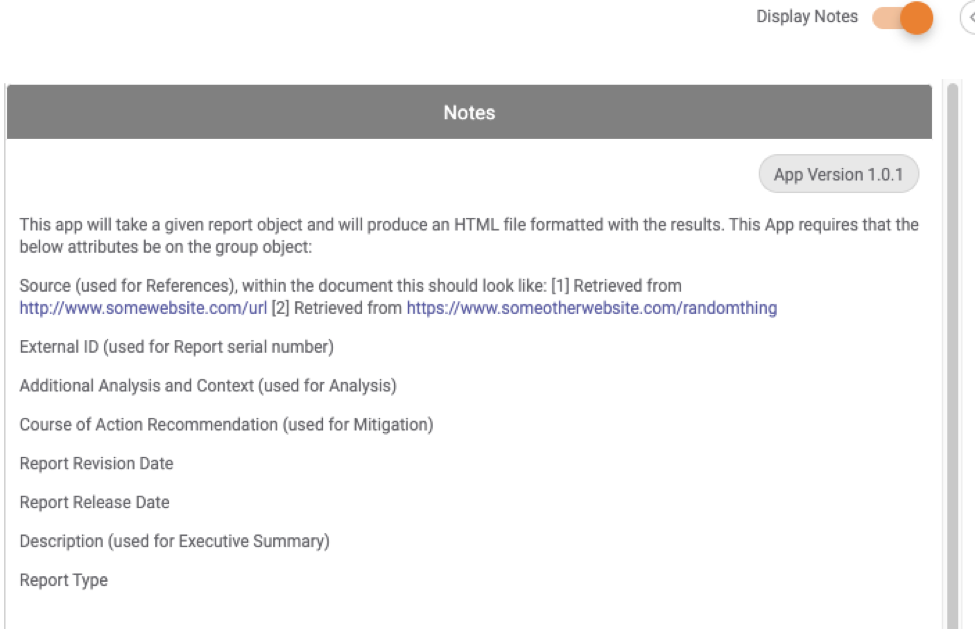
There are 8 required attributes for the report generation to be successful:
- Source (used for References), within the document this should look like:
[1] Retrieved from http://www.somewebsite.com/url
[2] Retrieved from https://www.someotherwebsite.com/randomthing - External ID (used for Report serial number)
- Additional Analysis and Context (used for Analysis)
- Course of Action Recommendation (used for Mitigation)
- Report Revision Date
- Report Release Date
- Description (used for Executive Summary)
- Report Type
These attributes can be uploaded to your instance of ThreatConnect (As a System Admin, ⚙️ > System Settings > Attribute Types > Upload) or (alternatively as an Org Admin: ⚙️ > Org Config > Attribute Types > Upload) and select the attributes.json
Note: If these are added at the Org level only, this app will only work properly at the Org level and not in any communities or sources. If this app is uploaded to the System Level, it will work across all Orgs, Communities and sources within your instance.
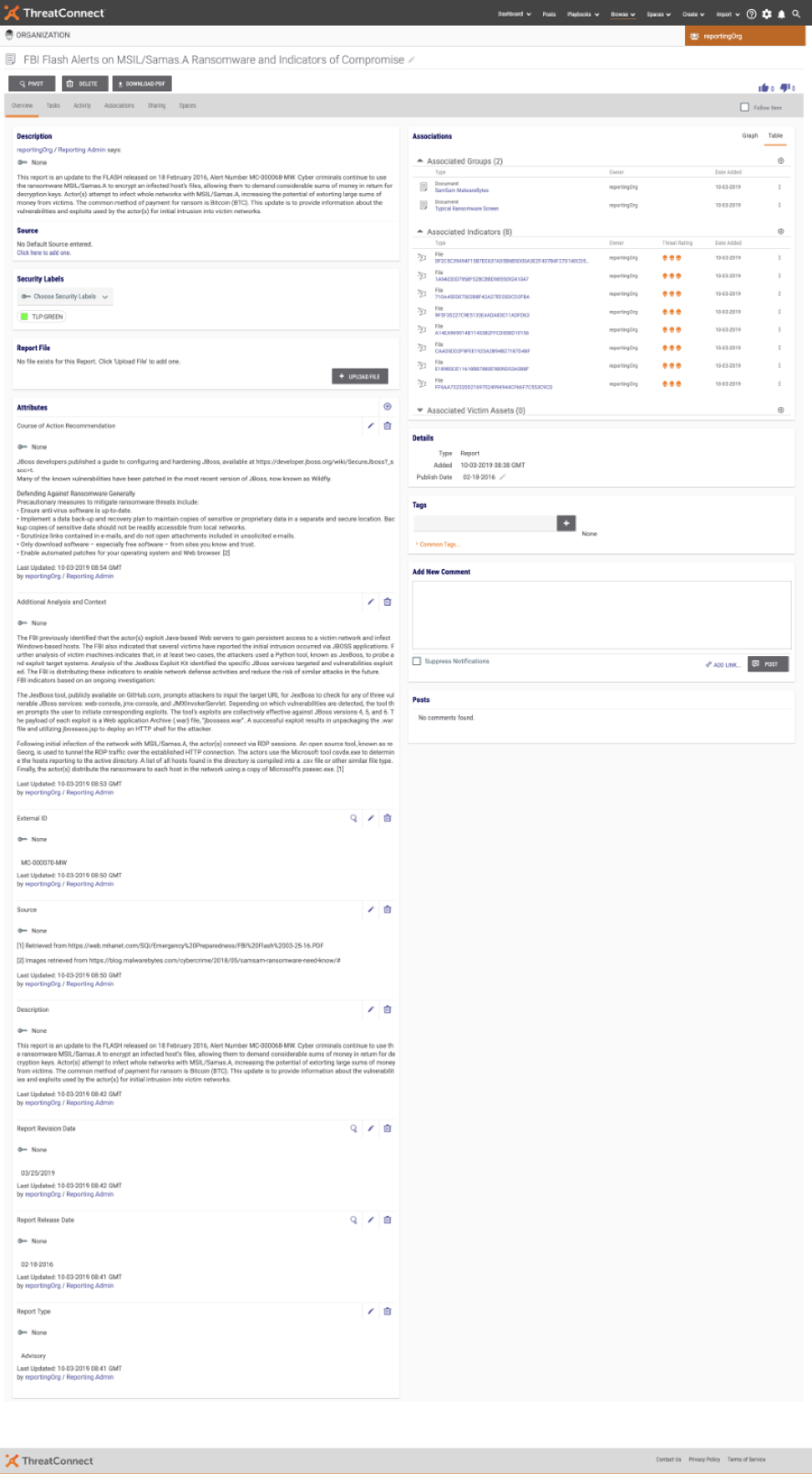
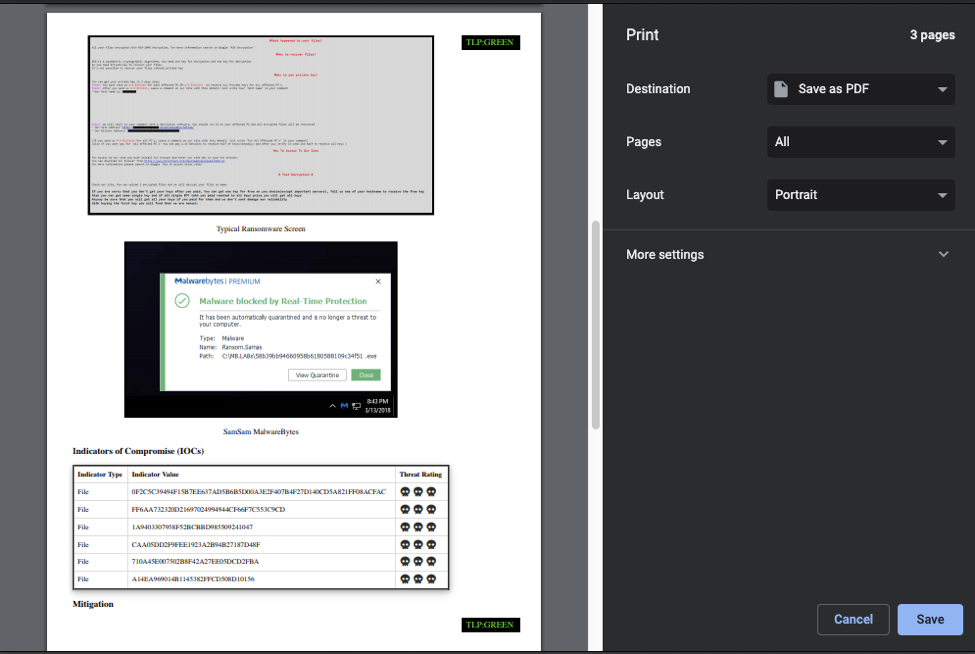
For demonstration purposes we will be generating an abbreviated example of this report: https://web.mhanet.com/SQI/Emergency%20Preparedness/FBI%20Flash%2003-25-16.PDF (FBI MC-000070-MW ).
Below is how this would appear in ThreatConnect prior to executing the UserAction Trigger.
(Note the “Report File” box showing that no file exists)
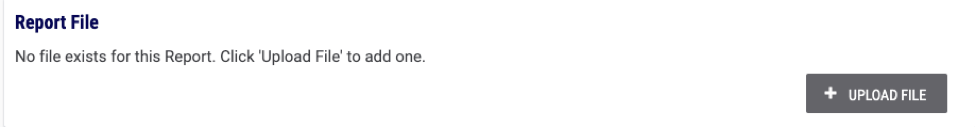
After importing the Playbook and activating on the same page you would click the User Action Trigger titled “Generate Report”:
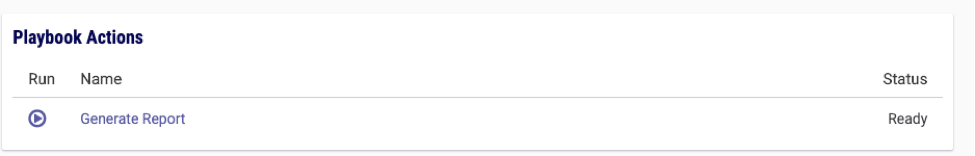
After clicking ▶️ the expected result looks like this:
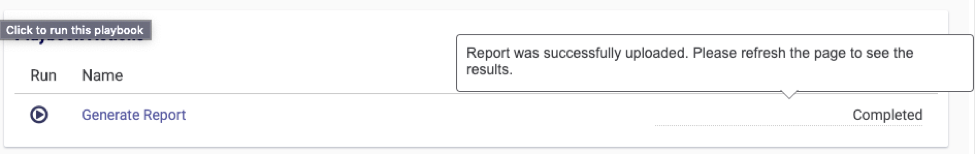
Then simply refreshing the page and you will now have a report available:
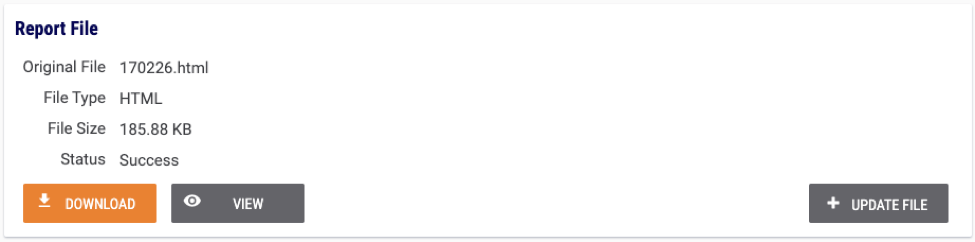
Clicking the ” View” button you can now see the generated report:
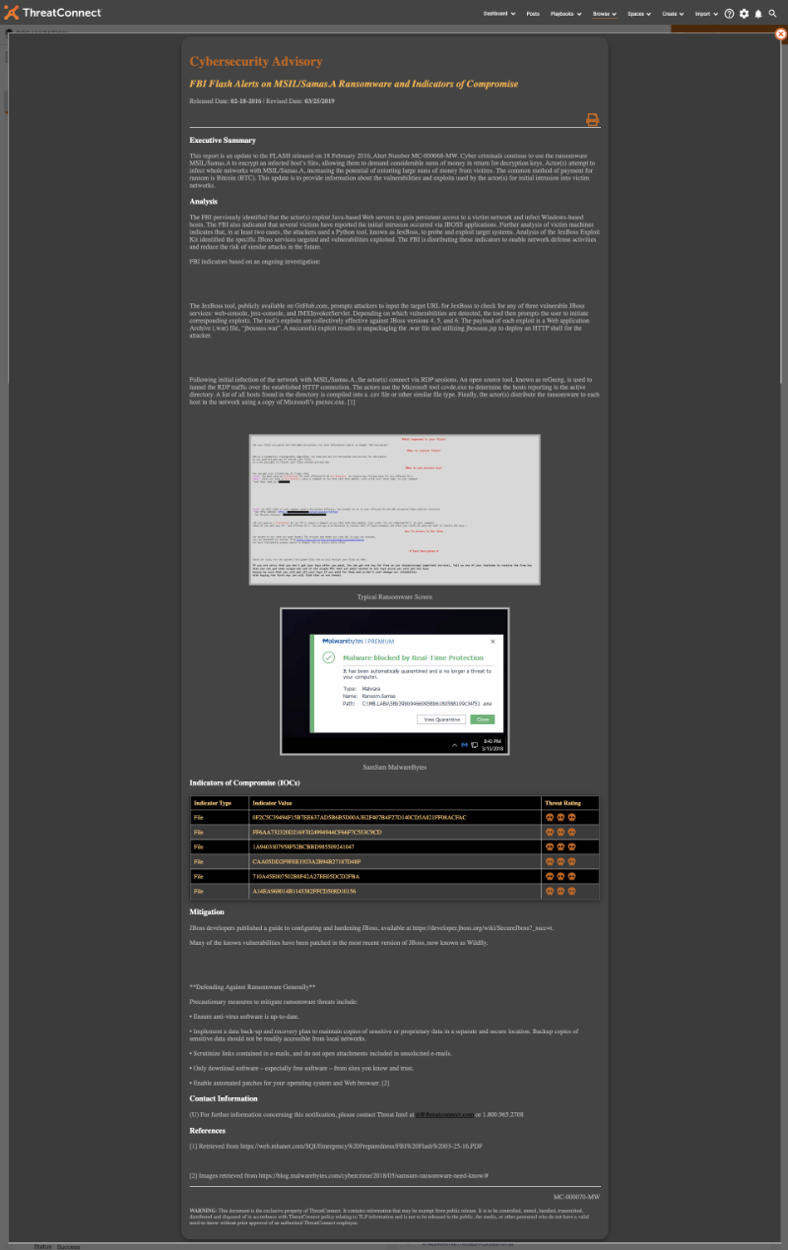
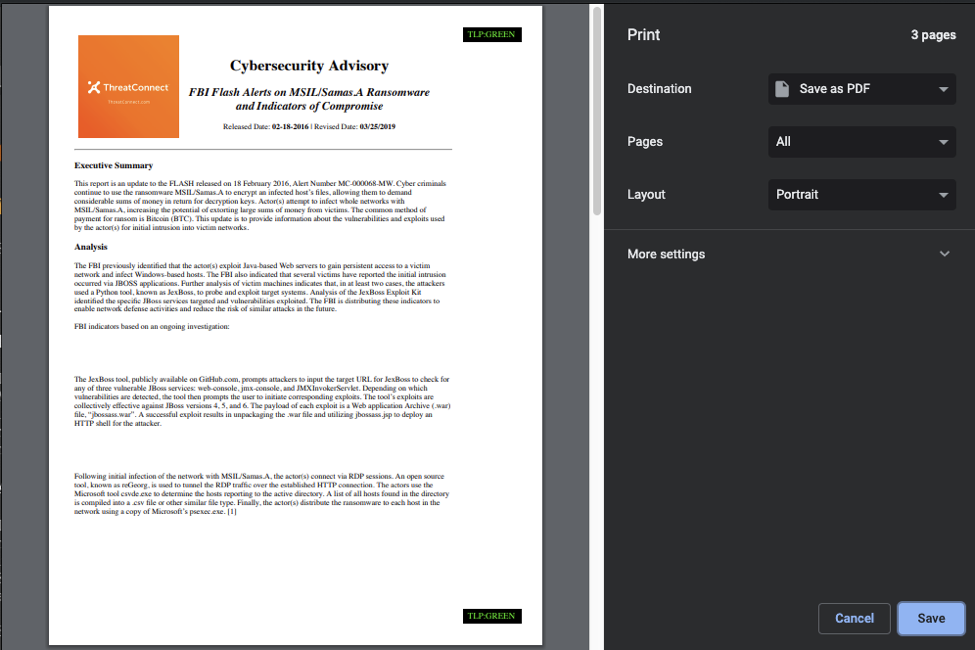
If you click the icon you will get a stripped down view of an Intelligence Report:
You can find this project here on GitHub: https://github.com/ThreatConnect-Inc/threatconnect-playbooks/tree/master/apps/TCPB_-_Generate_Intelligence_Report
The link to the Playbook App (.tcx): https://github.com/ThreatConnect-Inc/threatconnect-playbooks/blob/master/apps/TCPB_-_Generate_Intelligence_Report/Generate%20Intelligence%20Report.tcx
The link to the Playbook (.pbx): https://github.com/ThreatConnect-Inc/threatconnect-playbooks/blob/master/apps/TCPB_-_Generate_Intelligence_Report/Generate%20Intelligence%20Report.pbx
The link to the attributes.json: https://github.com/ThreatConnect-Inc/threatconnect-playbooks/blob/master/apps/TCPB_-_Generate_Intelligence_Report/attributes.json
Look out for the post next Friday for how to customize this app to change the disclaimer, and contact information.
