Posted
Welcome to ThreatConnect’s Playbook Fridays! We will continually publish posts featuring Playbooks (and sometimes Dashboards!) that can be built in the Platform.
ThreatConnect developed the Playbooks capability to help analysts automate time consuming and repetitive tasks so they can focus on what is most important. And in many cases, to ensure the analysis process can occur consistently and in real time, without human intervention. See below for our latest post:
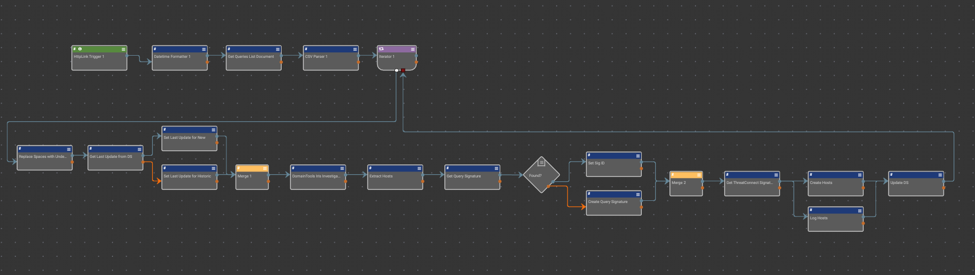
DomainTools offers a powerful tool, Iris Investigate, that allows analysts and threat hunters to monitor changes in adversary infrastructure during the course of their investigation.With the power of Playbooks, we’ll show you how to leverage it for yourself in the ThreatConnect Platform.
In short, this Playbook iterates through a list of user defined Iris queries of which all newly resulting domains from the query are imported and associated with the corresponding query’s signature.
To begin using this Playbook please follow these steps:
- Export your queries of interest from DomainTools Iris and compile them into a csv where the first column is the name of the query (which will also be the name of the signature) and the second column is the query hash.
- Upload the csv as a document named “Iris Queries” under the desired owner.
- Have your sys admin add a new signature type called “Iris Search Hash” under System Settings -> Settings -> Data -> Import -> importSignatureTypes.
- Import the playbook
- Configure the DomainTools Iris app with your API username and password (set these as keychain variables in your org if you haven’t already)
- Set the owner in all the apps that are marked with a warning indicator.
- Feel free to update the time in the timer trigger for when the Playbook is set to run on the daily.
Now stand back and watch as the Playbook automatically brings in any updated domains that pertain to your infrastructure research!
You can obtain the Playbook from Github, here.
NOTE: Some query hashes can get too long for DomainTools to handle via their API and in this case it is recommended that the query be broken down into smaller chunks if possible.
Disclaimer: ThreatConnect has been updated to include DomainTools Iris Search Hash as a default signature type. Users should consult their Customer Success rep to see if this affects existing playbooks.
