Posted
Rapidly deploy Yara rules that are associated to intel products within ThreatConnect out to CarbonBlack’s CB Response via their Yara Connector
This Playbook allows analysts that are performing an investigation or doing proactive threat hunting to quickly deploy signatures to Carbon Black’s CB Response. Normally this process is very manual as it requires the user to manually export the Yara rule out of ThreatConnect and then manually upload the Yara rule to CB Response’s Yara Connector.
Now, the process can be drastically simplified. Instead of having to manually export the Yara rule, locate it on your local hard disk, and then manually upload it into CB Response’s Yara Connector via the GUI. Now, users just have to click a button and all of the rest of the process is automated and completely transparent to the user.
This Playbook will instantiate the contents of the Yara rule, and then copy them over to a specific folder on the CB Response box via SCP (secure copy) over a SSH (secure shell) connection. Unfortunately there is no API endpoint for CB Response for uploading Yara rules, so SCP’ing the contents over is the only way to get them into CB Response.
Triggered via a UserAction, this Playbook allows the user to simply click a button, and the Yara rule will automatically be deployed.
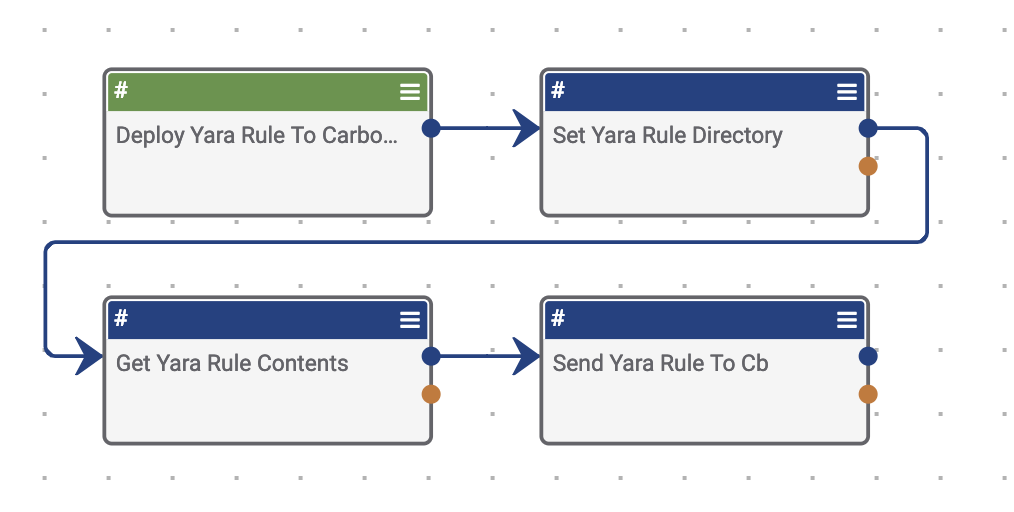
Here’s how to create the Playbook:
- Create a UserAction trigger that appears on Signature groups
- Use the Set Variable app so that the user can easily define the remote directory on the Cb Response box that is used for storing Yara rules. This directory will be used in the SSH app.
- Use the Get ThreatConnect Signature By ID app to retrieve the contents of the Yara rule. In the Group ID field, reference the TCEntity (#trg.action.entity) output variable from the Trigger.
- Use the SSH app to SCP the contents of the Yara rule to the destination Cb Response system.