Posted
This Playbook gets the listing of TOR nodes from dan.me website and parses all of the information into ThreatConnect for consumption.
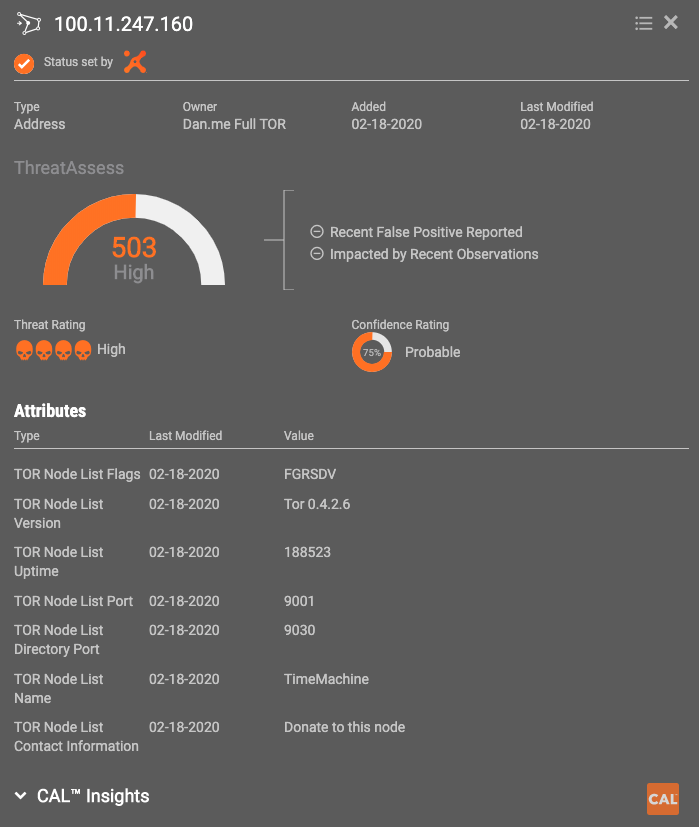
TOR is often used by malicious actors to conceal their identity and operate anonymously. Tracking these along with their respective ThreatAssess scores and organization specific observations will help analysts spot potential threats.
https://github.com/torproject/torspec/blob/main/dir-spec.txt
- Details of each Node
- Flags annotate interesting criteria – flag breakdown below
- Easily dashboard-able to highlight relevant items
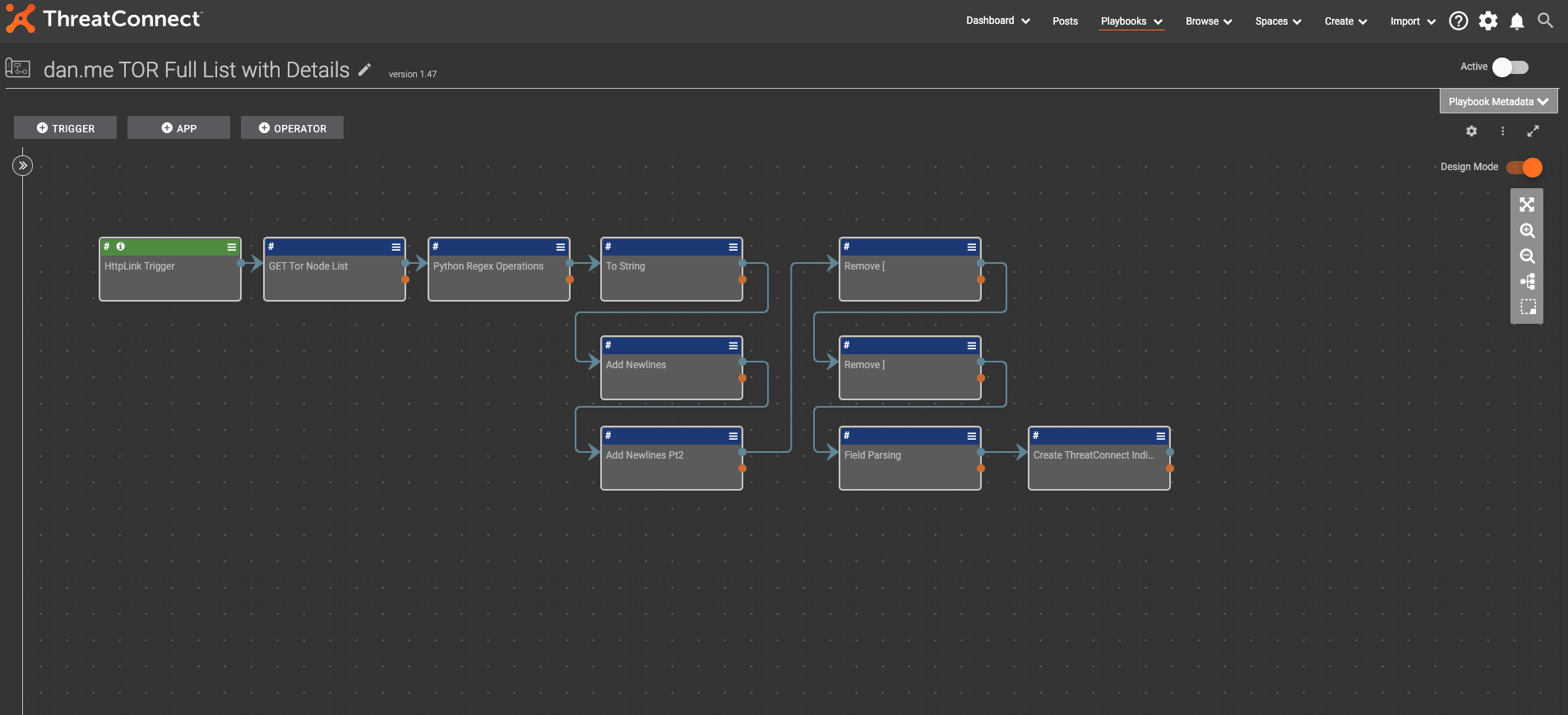
This Playbook brings in all data surrounding the TOR node list. The list includes an array of different data points, including flags that define criteria around the node, system uptime, port numbers, etc… that the current OSINT feed does not ingest. It is triggered by either a timer or manually executed HTTP link trigger. Timer shouldn’t be too often, as the site states it will ban IP addresses that request too often.
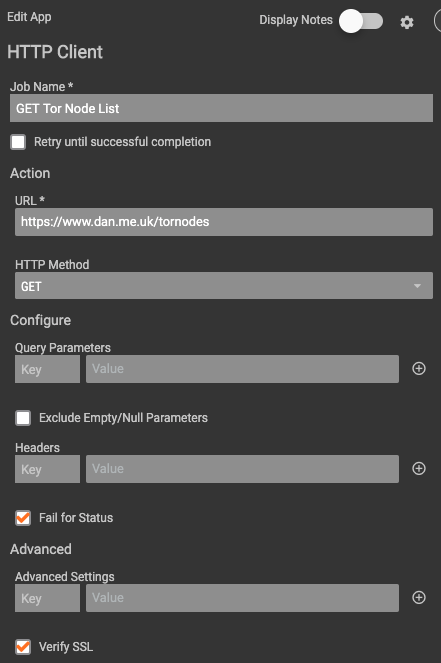
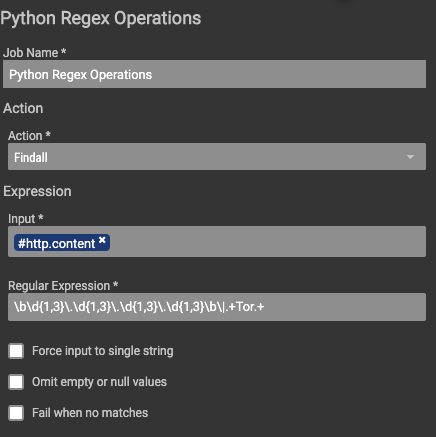
Once triggered, an HTTP client makes a call to the dan.me.uk site to get the full list of TOR nodes (https://www.dan.me.uk/tornodes). The content of that page is then passed into a Python Regex Operations app that pulls out each node listing via a regular expression.
This listing is then passed through a handful of steps to clean it up and format it into a pipe-delimited format. The next ‘Field parser’ step is simply the CSV parser app setup to use the pipe as a delimiter instead of a comma.
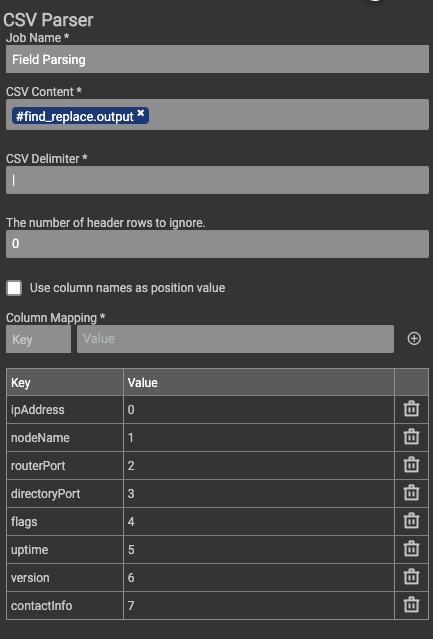
Once the information is parsed into its own array, the Create ThreatConnect Indicator app utilizes all of the arrays as either the IP address IOC, or the relevant attributes for each IOC.
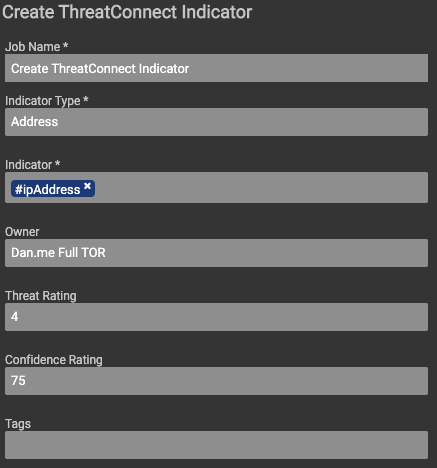
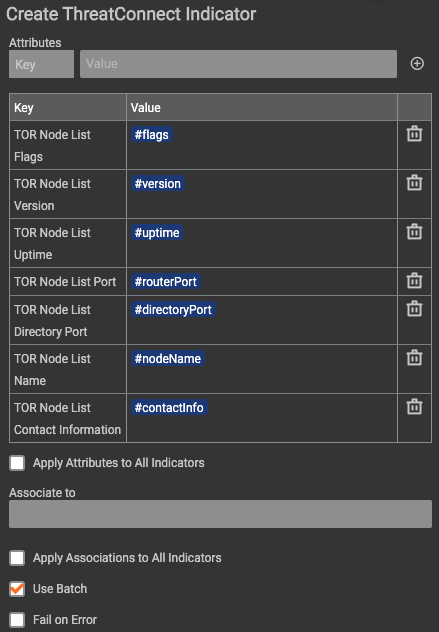
Here is the complete Playbook: