Posted
We’ve got options for how you can track activity related to Coronavirus / COVID-19 in the ThreatConnect Platform:
1. New System Dashboard – COVID-19 Related Activity
The ThreatConnect Research Team has created the ‘COVID-19-Related Activity Dashboard’, which provides a single location to view consolidated, relevant intelligence from across various sources where threat actors are leveraging the virus as a theme. To view this dashboard, place the cursor over Dashboard on the top navigation bar and select it from the System Dashboards list.
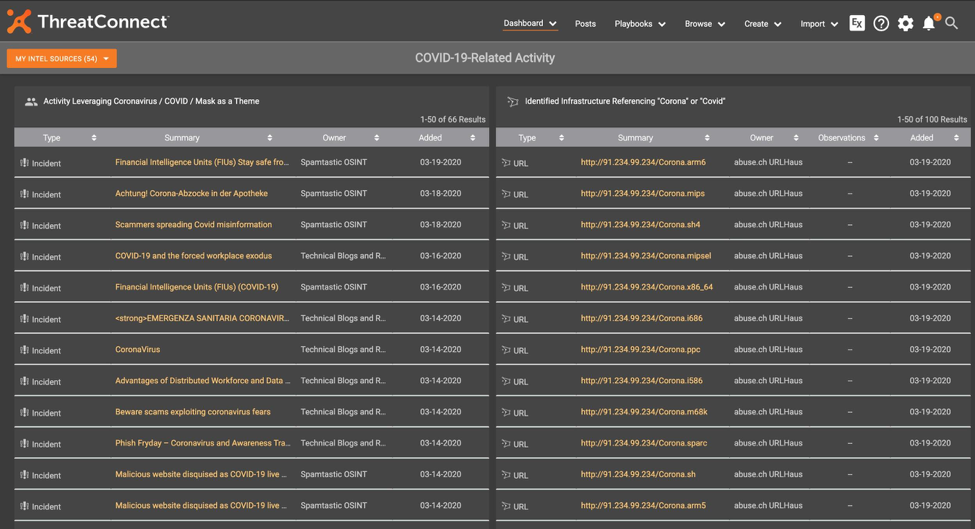
The first Dashboard Card lists high-level groups (campaigns, incidents, etc.) that mention “covid”, “corona”, or “mask” in the name. Additionally, there’s a second Dashboard Card showing infrastructure (domains and URLs) where the “covid” or “corona” strings are present, and provides indicators that you can block or further scrutinize if you’re concerned about COVID-19-themed activity. Generally, the Dashboard can help triage and consolidate a lot of intelligence that would otherwise take a significant amount of time to identify in the separate sources.
The COVID-19-Related Activity Dashboard uses the ThreatConnect Query Language (TQL) queries below, which can be used to recreate this Dashboard on any ThreatConnect instance:
Card 1: Activity Leveraging Coronavirus / COVID / Mask as a Theme
typeName in ("Adversary", "Campaign", "Document", "Email", "Event", "Incident", "Intrusion Set", "Report", "Signature", "Task", "Threat") and (summary contains "corona" or summary contains "covid" or summary contains "mask")
Card 2: Identified Infrastructure Referencing “Corona” or “Covid”
typeName in ("Host", "URL") and dateAdded > "12-01-2019" and (summary contains "corona" or summary contains "covid")
2. Build Your Own COVID-19 Dashboard
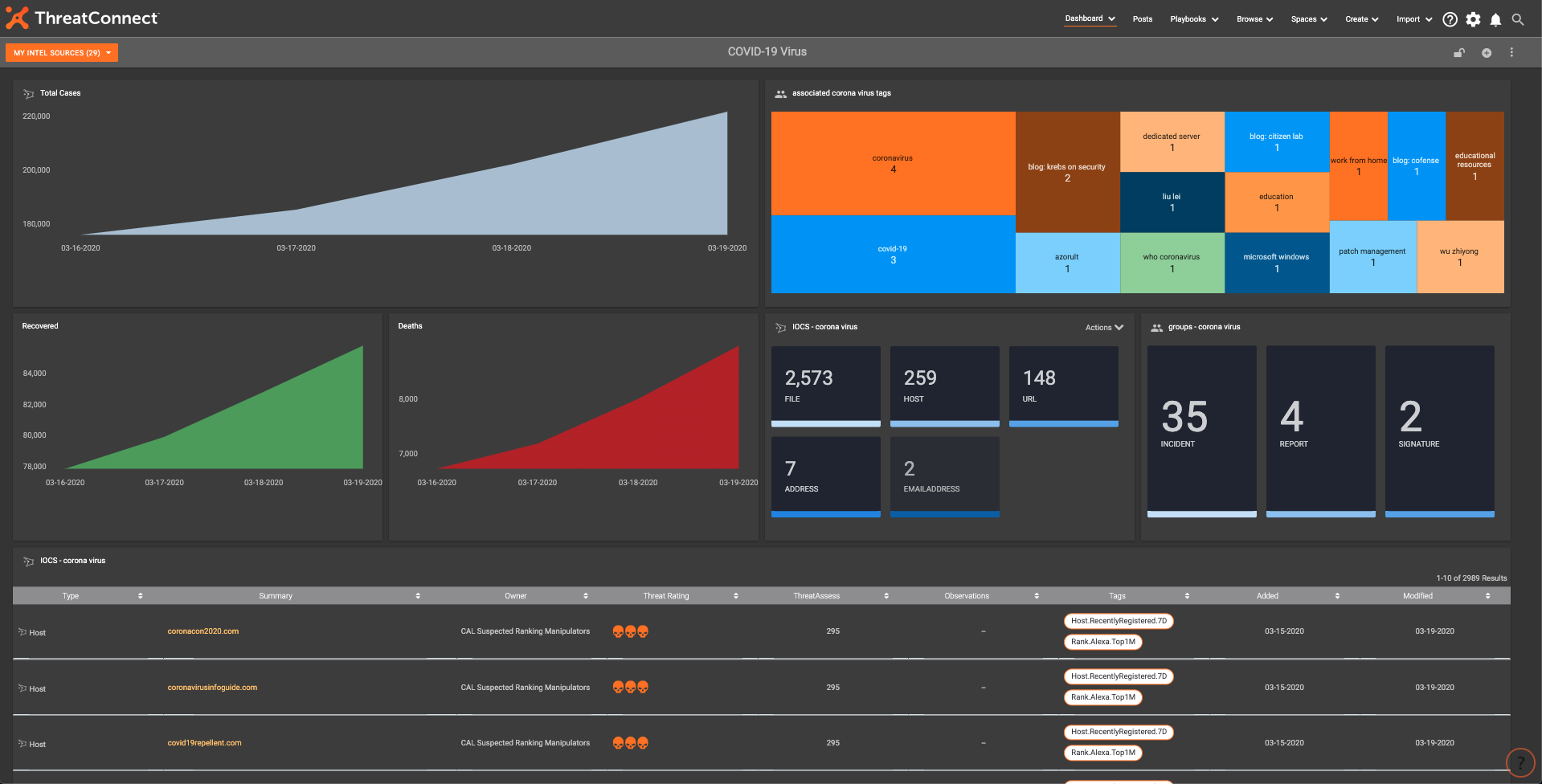
We have been noticing an increasing trend of Covid-19 themed phishing attempts, as well as online maps that were malicious. Creating this Dashboard made a single focal point to use as an analyst to track potential threats.
This Dashboard offers:
- Single pane of glass view into Covid-19 IOCs and attacks
- Daily Metrics to track actual Covid-19 cases worldwide
This Dashboard aggregates all Covid activity and IOCs into one easy to view/understand place within ThreatConnect:
IOC and group cards
hasGroup( typename = ("Adversary", "Campaign", "Document", "Email", "Event", "Incident", "Intrusion Set", "Report", "Signature", "Task", "Threat") and tag in ("coronavirus", "wuhan coronavirus", "coronavirus malware", "coronavirus map", "who coronavirus", "covid-19", "covid-19 malware")) or tag in ("coronavirus", "wuhan coronavirus", "coronavirus malware", "coronavirus map", "who coronavirus", "covid-19", "covid-19 malware") or summary contains "covid" or summary contains "corona"
Tag card
tag in ("coronavirus", "wuhan coronavirus", "coronavirus malware", "coronavirus map", "who coronavirus", "covid-19", "covid-19 malware")
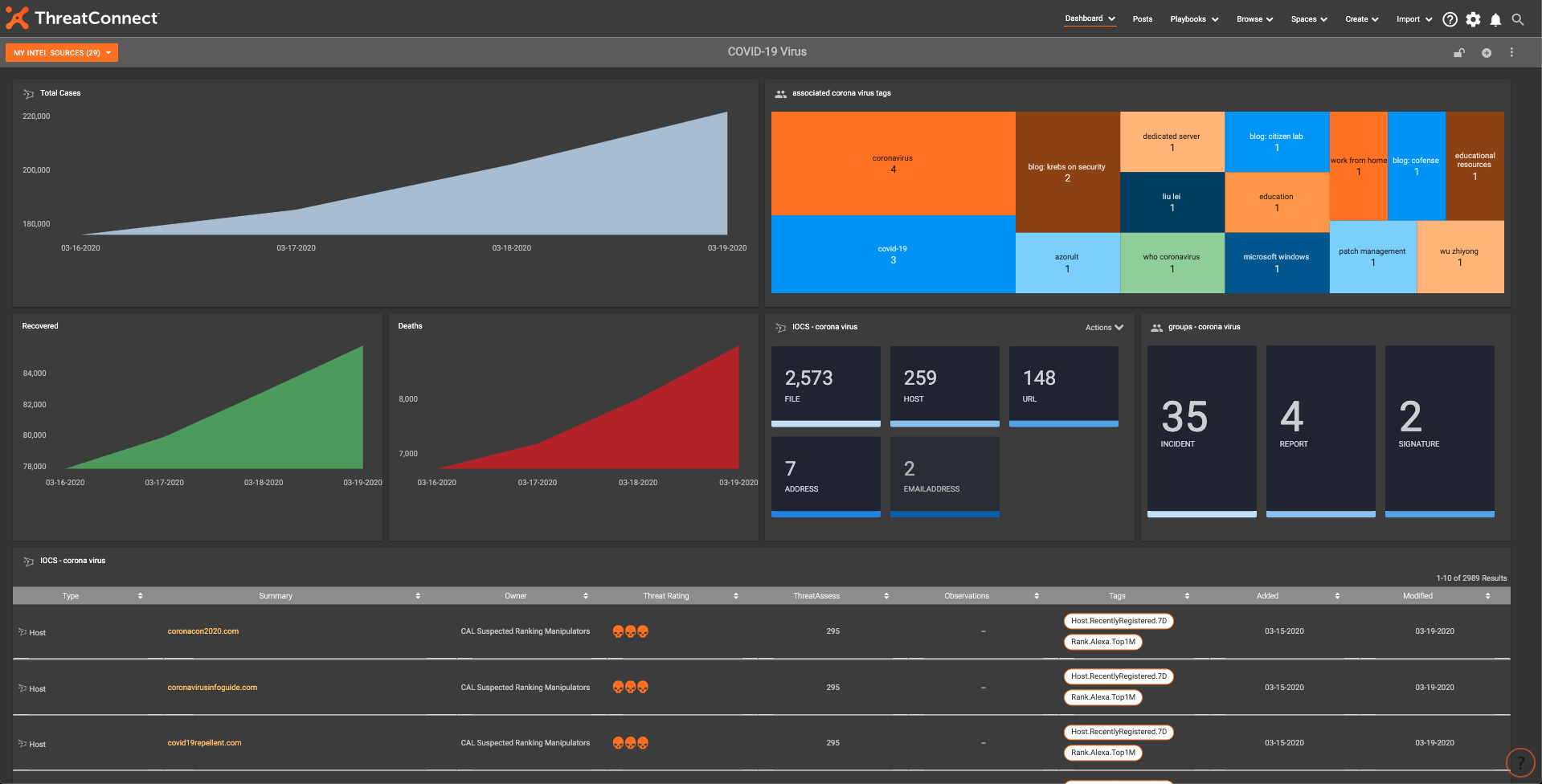
Final COVID-19 Dashboard
3. Covid-19 Metrics Playbook
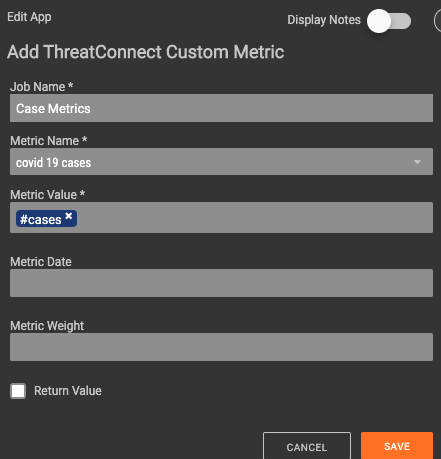
Drive the metrics that show day-to-day trends for Covid-19. This Playbook is populating the 3 custom metrics the Dashboard is using to show the to Covid-19 cases, deaths, and recoveries.
This Playbook is triggered by a Timer trigger that pulls new metric data in once per day at 7AM. It performs a GET request to https://coronavirus-19-api.herokuapp.com/all to retrieve daily case metrics.
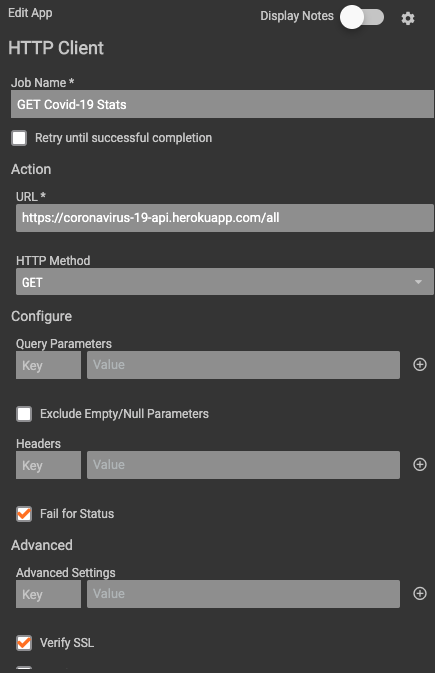
Once obtained, the data is parsed and submitted as new data points within the custom metrics.
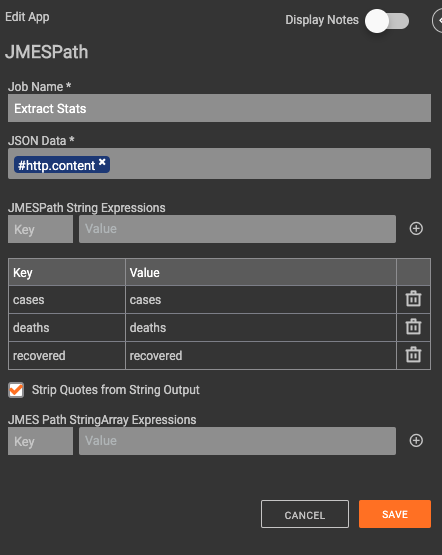
The only configuration needed for this Playbook is to set the timer trigger and populate the correct custom metrics. Note: The custom metrics need to be created in ThreatConnect prior to setting up the Playbook.
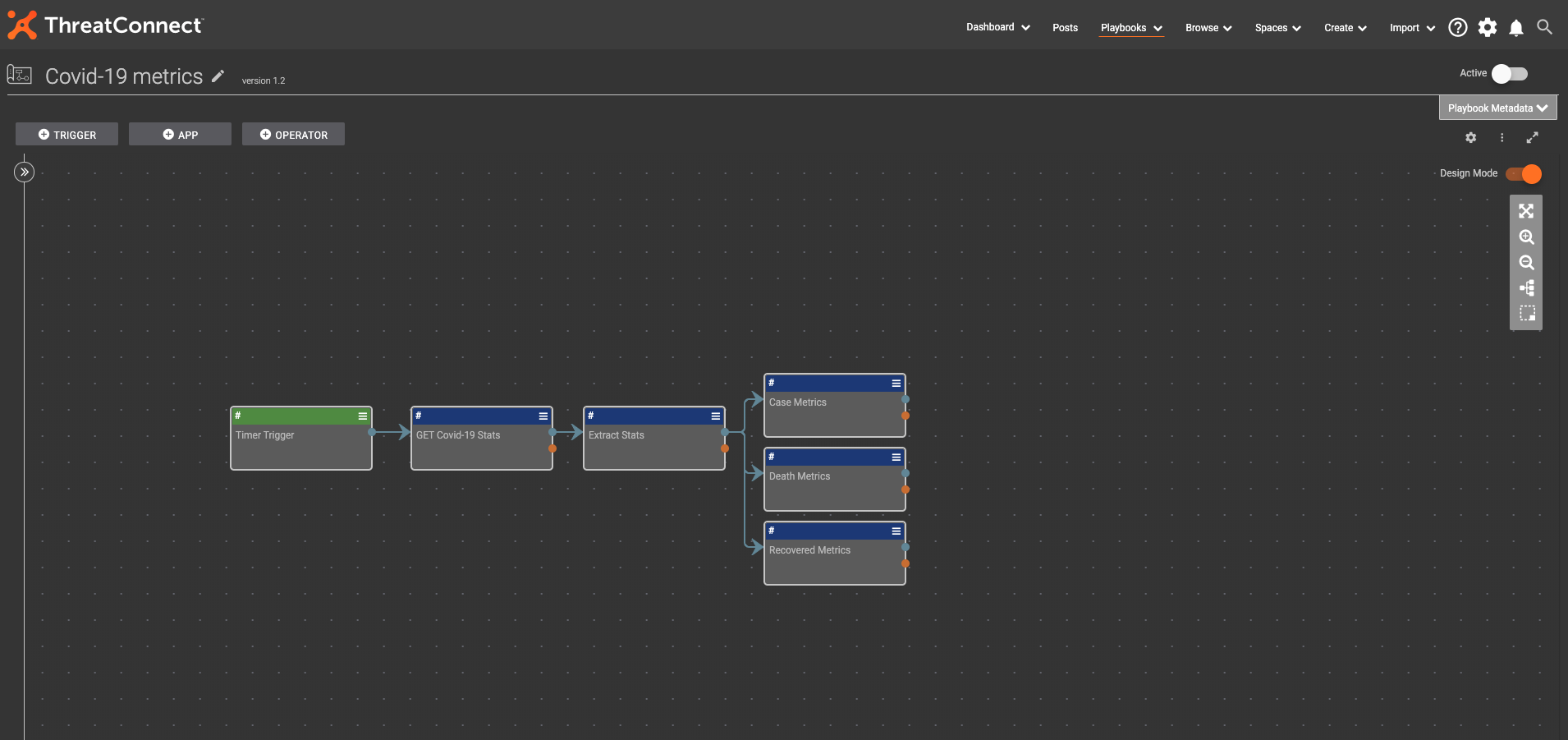
Full COVID-19 Metrics Playbook
To see this Playbook in Github: https://github.com/ThreatConnect-Inc/threatconnect-playbooks/tree/master/playbooks/TCPB-Covid-19%20Metrics
4. VirusTotal – Search Terms Playbook
This Playbook bridges the gap between what VirusTotal knows and what can be turned into actionable intel inside ThreatConnect. It was designed for making a ‘search term’ like effect for querying VirusTotal for file hashes that might be used in relation to popular topics of the day. The COVID-19 outbreak was the original idea for this.
This Playbook simplifies the process of hunting for new threat intelligence and memorializing it in the Platform. It offers:
- A simple variable needs to be configured for whatever term you want to search VirusTotal for.
- Stay up to date with potential threats taking advantage of the news cycle
A manual trigger from the user will generate the API call to VirusTotal. The response is then parsed, and iterated over to create file hash indicators with the relevant tags in ThreatConnect. This manual HTTP link trigger was designed to execute whenever the user wanted to ‘ask the question’ to VirusTotal about what it knows on the topic.
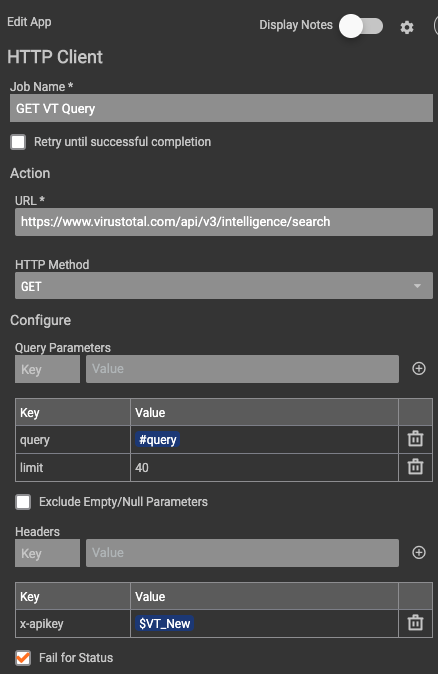
Users will have to have the Premium VirusTotal API key to access the /search endpoint in their V3 API.
Once the Playbook is imported, one thing that needs to be set up is the x-apikey KV pair in the header section of the HTTP client. The next is to verify the owner the file hash IOCs are saved to in the Create ThreatConnect File app.
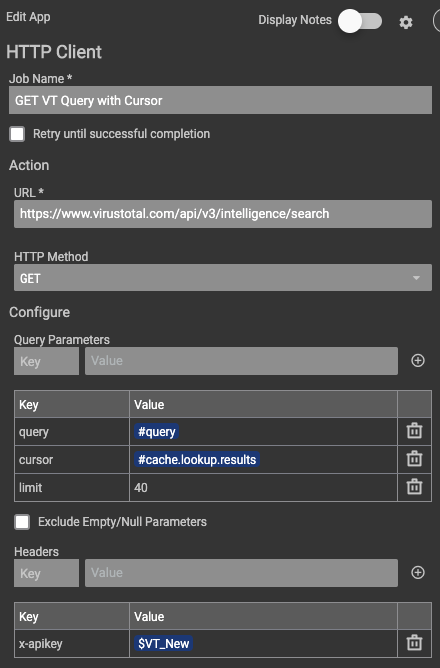
Full Playbook below:
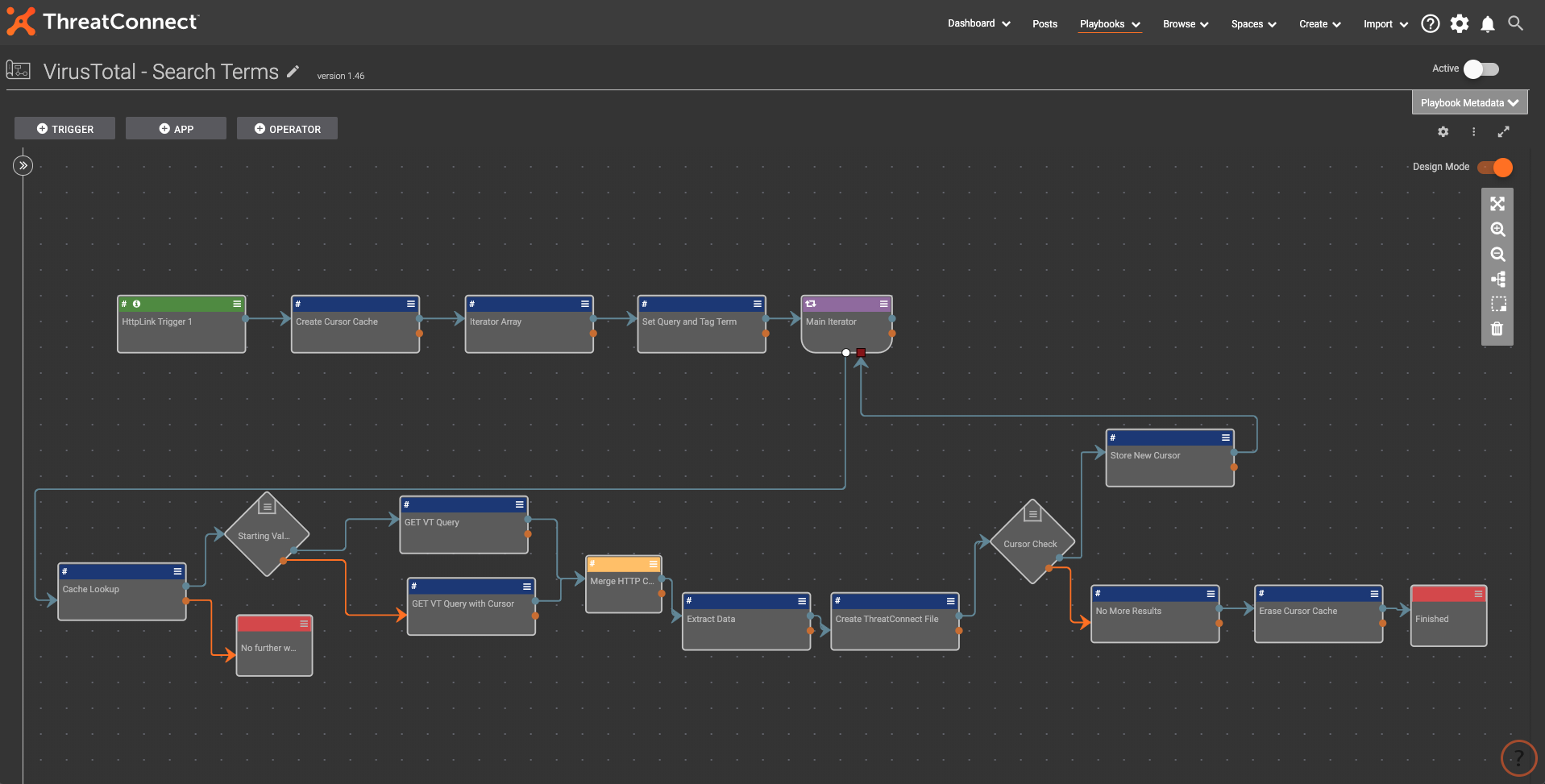
To see this VirusTotal search in Github: https://github.com/ThreatConnect-Inc/threatconnect-playbooks/tree/master/playbooks/TCPB-VirusTotal%20Search