Posted
This blog post is a continuation of our blog post Putting Cyber Risk Quantification Into Action: Moving Beyond Theory.
In part one, we explored how Cyber Risk Quantification (CRQ) has evolved from theory to practice, focusing on the key choice between manual estimates and automated, data-driven approaches. We discussed how CRQ’s real value lies in continuous prioritization – helping you determine what matters most with limited resources. Through examples like MFA rollouts, we saw how use cases interconnect to transform security from the team that says “no” into a strategic business partner. We also covered the cultural shift CRQ creates, with nearly all users wishing they’d started sooner due to benefits like speaking the language of business, double-digit drops in breach rates, and better collaboration across teams. Now, let’s delve into the real-world challenges that hinder organizations from achieving full CRQ operationalization, and explore the practical solutions that can help you move faster.
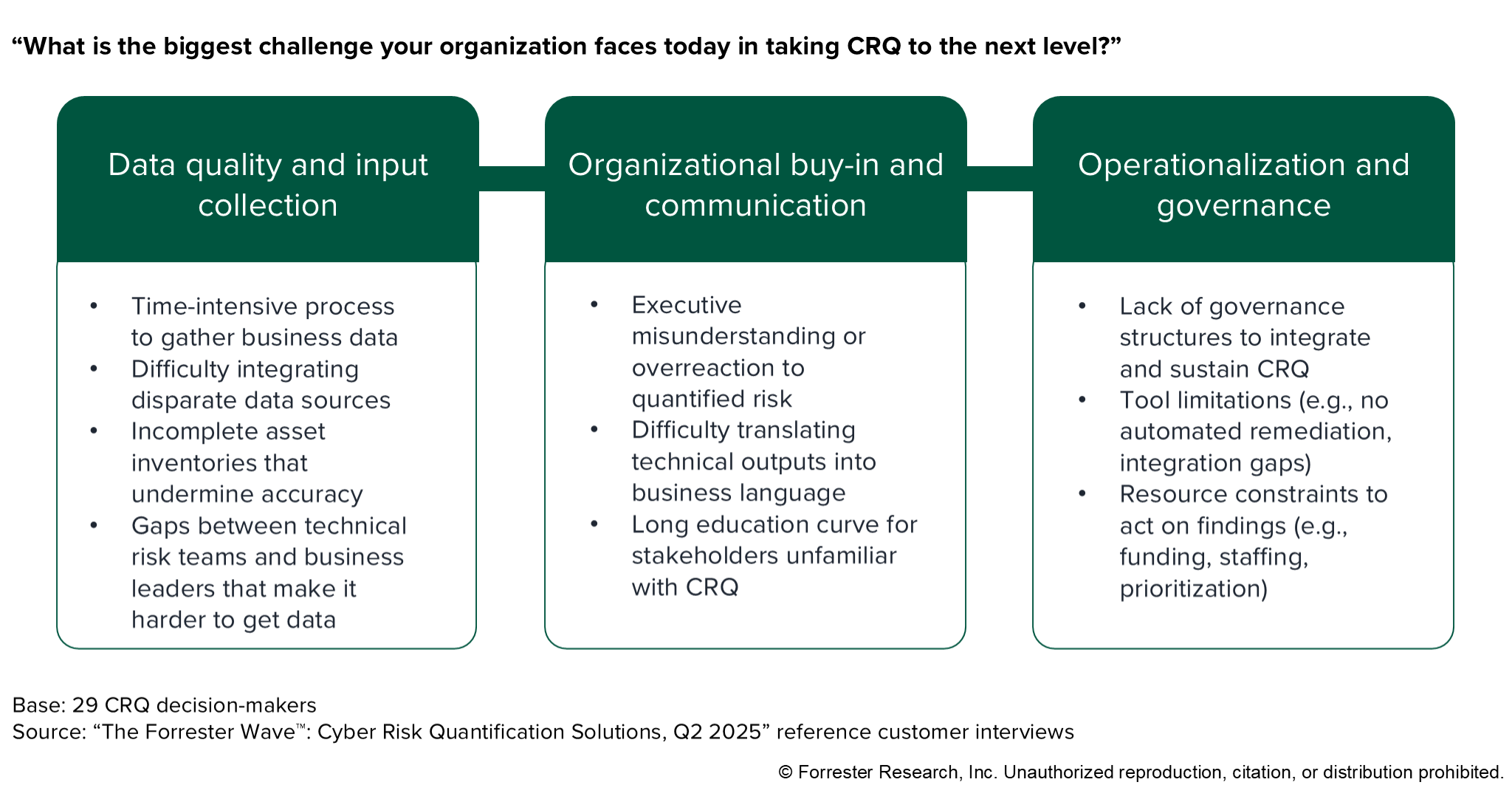
Addressing Maturity Challenges
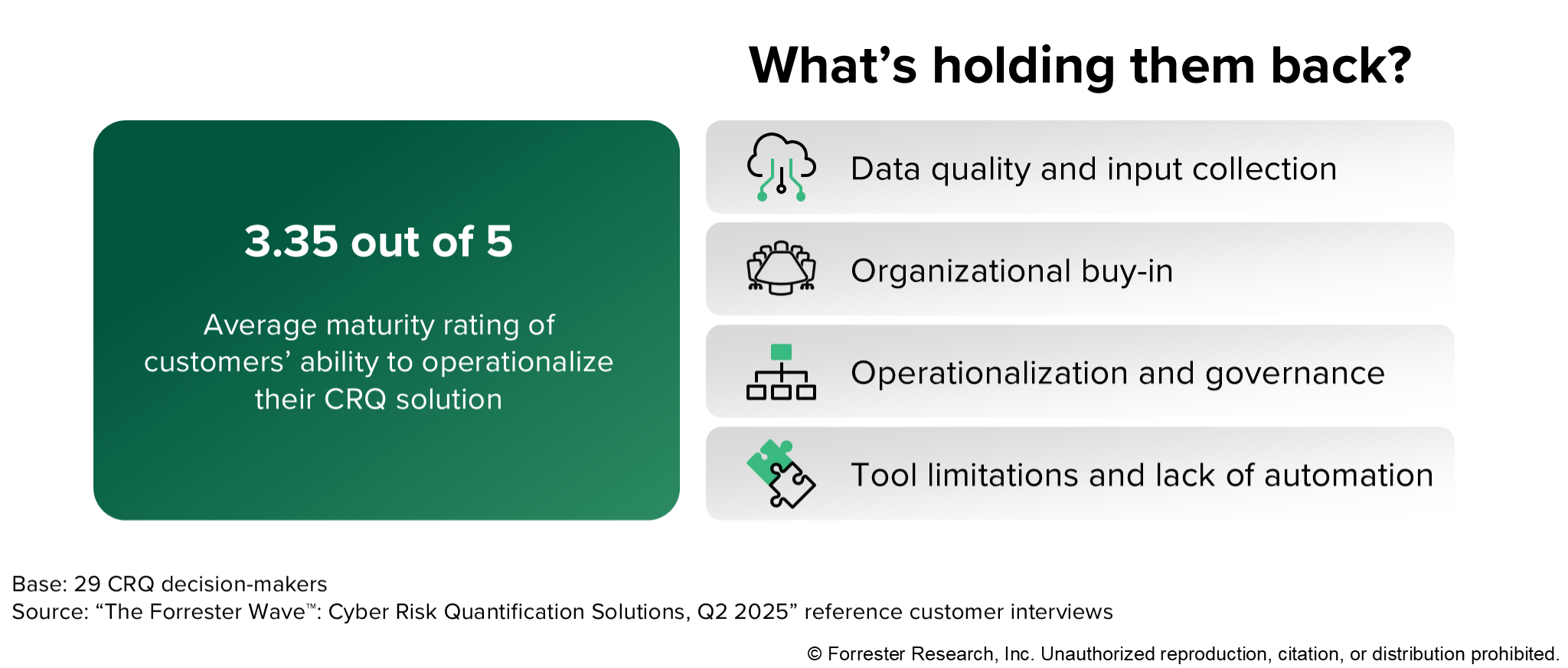
The Buyer’s Guide identifies that organizational issues hold back CRQ maturity. Despite CRQ accelerating risk management improvements, customers rated their operationalization maturity at just 3.3 out of 5. Top challenges include:
- Resource constraints
- Education gaps
- Data quality and input collection issues
These challenges describe manual approaches. The solution? Bring data and automation to the problem space, letting organizations critique models rather than create them from scratch.
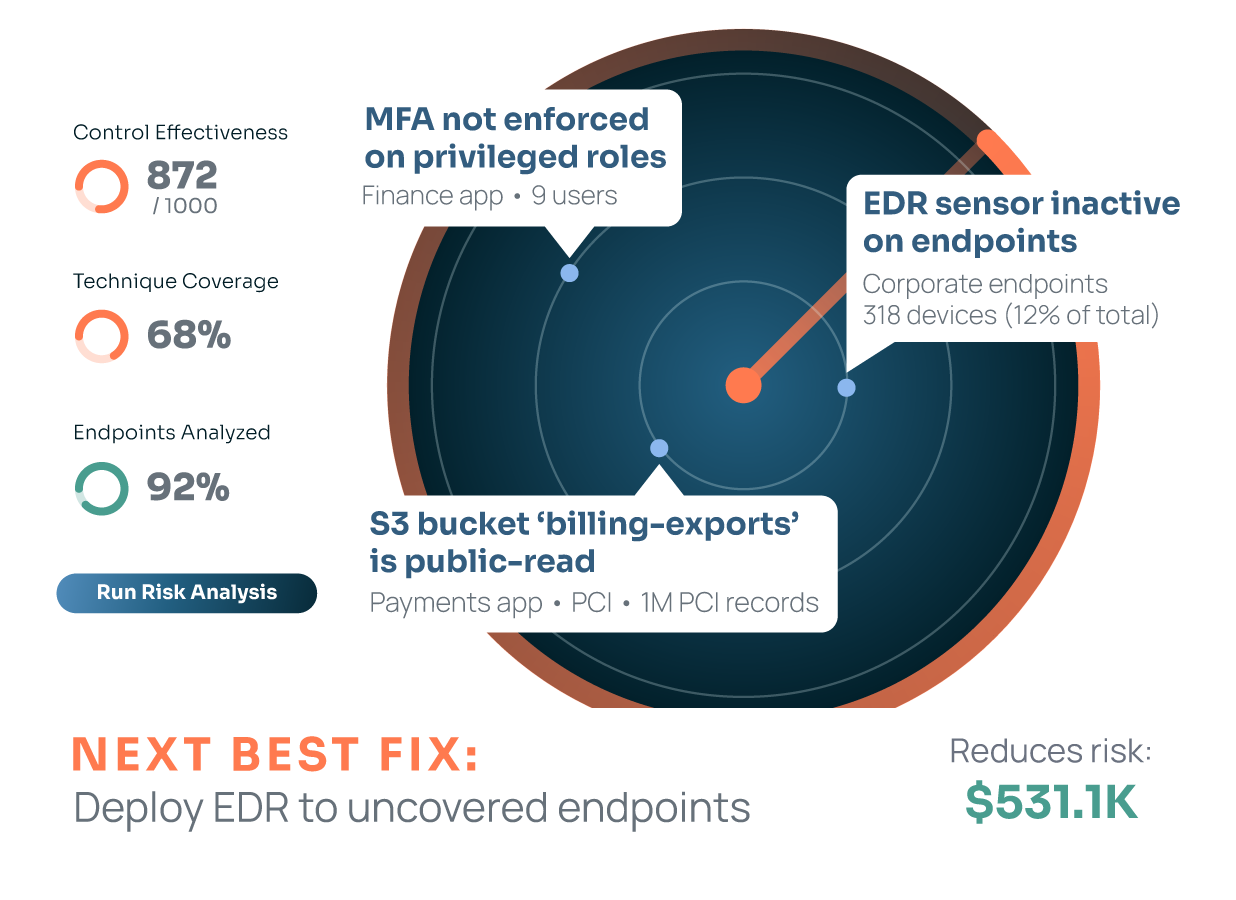
This means starting with 20+ years of historical loss data, insurance claims data, and industry benchmarks. That’s the really easy, defensible way to get started. At ThreatConnect, we collect more technical data through our continuous controls monitoring to identify risks, such as having PowerShell enabled on endpoints without proper restrictions. Then layer in external threat intelligence to complete the picture.
Here’s the interesting part: while many solutions offer hundreds of tunable variables, most organizations tune them only a handful of times over several years. Once people see data-backed models, they realize they don’t actually need to change much. The data speaks for itself.
Integration Quality and Peer Benchmarking
The Buyer’s Guide research shows overall vendor satisfaction remains high (4.7 out of 5 for likelihood to buy again), but two areas score lower: integration quality (3.2 out of 5) and utility of peer benchmark data (3.5 out of 5).
On Integrations: The question isn’t “How many integrations do you have?” but rather “What do those integrations accomplish?” Organizations should focus on coverage across the MITRE ATT&CK framework – covering the techniques attackers actually use from initial access through data exfiltration. If your existing integrations cover 80-90% of these techniques with appropriate defenses, adding more just creates maintenance overhead without solving additional business problems.
On Benchmarking: Most companies don’t publicly report why they were breached or what controls failed. This makes traditional benchmarking difficult. The more valuable approach? Point to actual breach data from similar organizations, creating trust through real-world examples rather than theoretical comparisons.
The Bottom Line: No Reason to Wait
CRQ has proven itself as more than a risk measurement tool. It’s a complete shift in how security teams operate and communicate value. From choosing between manual and automated approaches to linking threat intelligence with risk data, organizations that implement CRQ gain the ability to prioritize effectively, speak the language of business, and make security an enabling function rather than a roadblock. Security should never say “no”. Security should say “yes, if…” and then explain the risks and trade-offs in business terms. That requires CRQ.
The benefits are measurable: double-digit reductions in breach likelihood and impact, better collaboration across teams, and strategic participation in executive decisions. Yet success requires navigating real challenges like resource constraints, data quality issues, and integration complexity.
The good news? Organizations don’t need to start with perfect data or complete automation. They can begin with data-driven models, critique and refine them, and expand over time. The key is starting the journey from theoretical risk discussions to actionable, continuous risk management that connects the boardroom to day-to-day security operations.
The question isn’t whether to implement CRQ. The question is, why wait another day when the tools, data, and methodologies are ready today?
Request a personalized CRQ demo today!