
Read insights, thought leadership, and platform updates.
No Blogs Match Your Results
Please try again or contact marketing@threatconnect.com for more information on our blogs.

How ThreatConnect and Polarity Empower Teams to Combat Phishing Threats
Phishing remains one of the most effective and pervasive attack methods for cybercriminals, with threats evolving in sophistication and becoming increasingly difficult to detect. To stay ahead, security teams need tools that deliver contextualized intelligence and seamless workflows to tackle these challenges. ThreatConnect and Polarity provide an integrated solution to address phishing threats effectively, empowering […]

ThreatConnect’s 2024 Year in Review: Let’s Celebrate What We’ve Accomplished Together
With 2024 in our rearview mirror, let’s take a moment to reflect. Like always, threats are evolving, and security challenges are becoming… more challenging: escalations in targeted ransomware attacks, emerging techniques like adversary-in-the-middle phishing, and a stream of vendors throw all of their offerings into the mix that now need to be integrated into your […]
Navigate ISO 27001:2022 Compliance with ThreatConnect
ISO 27001 has long set the standard for managing information security. Still, the 2022 updates bring a critical shift: organizations must now effectively process and analyze threat intelligence to stay ahead of increasingly sophisticated threats. These updates go beyond compliance, challenging organizations to integrate actionable intelligence and streamline security operations. For many, this introduces new […]

Unlocking the Potential of Cyber Threat Intelligence: A Guide to the Threat Intelligence Maturity Model
A rapidly evolving cyber threat landscape demands that organizations adopt more than reactive defenses—they need proactive, intelligence-driven strategies. The Threat Intelligence Maturity Model (TIMM) serves as a roadmap for organizations to assess, plan, and advance their cyber threat intelligence (CTI) capabilities, regardless of their journey. The Five Levels of Threat Intelligence Maturity The TIMM provides […]

Solving Complex Threats with Microsoft Copilot Integration for ThreatConnect
Security teams face constant pressure to sift through vast data to identify threats, assess risks, and respond promptly. Imagine a scenario where a Cyber Threat Intelligence (CTI) team is investigating a sophisticated phishing campaign targeting their organization. Clues are minimal, and time is critical. This is where the Microsoft Copilot for Security integration with ThreatConnect […]

Five Quick Tips to Enhance Your Threat Hunting Program
As a CTI analyst, you know that advanced threats often evade traditional security tools, leaving gaps that can put your organization at risk. Whether starting from scratch or seeking to elevate your current threat-hunting program, the challenge is real: you need to hunt for these hidden threats proactively, but building a structured, effective program takes […]

Unlock Enhanced Threat Detection with ThreatConnect and CrowdStrike
Unlock Enhanced Threat Detection with ThreatConnect and CrowdStrike In today’s fast-paced cybersecurity landscape, security teams face many alerts and struggle to filter through false positives to prioritize critical incidents. The integration of ThreatConnect and CrowdStrike Falcon Insight XDR offers a powerful solution to this challenge, empowering security operations teams with high-fidelity threat intelligence and seamless […]

ThreatConnect CAL™: New, Unique Intelligence for Polarity
In the current cybersecurity environment, organizations face a barrage of alerts concerning suspicious activities that can quickly overwhelm their security teams. CTI Analysts must navigate this complexity while ensuring they can accurately identify genuine threats amidst false positives. This challenge is especially pronounced in industries where the stakes are high and the need for precision […]

ThreatConnect TI Ops Platform 7.7: Boost Your Security Team’s Efficiency
Security teams face constant challenges in managing vast amounts of threat data and quickly identifying what matters most. ThreatConnect’s TI Ops 7.7 release addresses these needs with new features like Enhanced Search and Clear Context, designed to streamline threat detection and analysis. By enhancing search precision and consolidating critical information, these updates help teams work […]
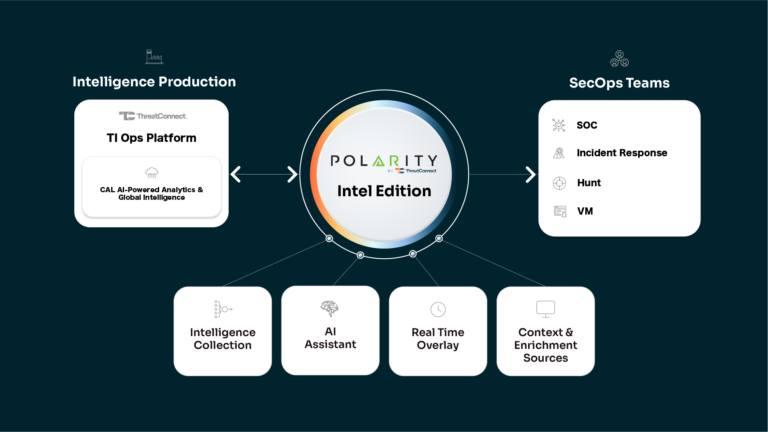
ThreatConnect Launches Polarity Intel Edition to Streamline Intelligence for SecOps Teams
The Power of Force Multiplication “Threat intelligence is like the Force: it should flow through everything.” -Andy Pendergast, Co-Creator of the Diamond Model of Intrusion Analysis and Co-Founder of ThreatConnect “Remember, a Jedi can feel the threat intelligence flowing through them.” -Obi-Wan Kenobi (probably) ThreatConnect is launching a new product to complement our Threat Intelligence […]

Top 5 Best Practices to Continuously Improve Your Intelligence Requirements
Organizations must adopt a practice of continuous improvement to maintain relevant and agile intelligence requirements, which are crucial in today’s rapidly evolving cyber threat landscape. Here are the top five best practices for refining and updating your intelligence requirements to stay ahead of evolving threats. 1. Regularly Monitor and Assess the Threat Landscape and Adjust […]

Achieve Faster, More Precise Vulnerability Prioritization with ThreatConnect and VulnCheck
In the rapidly evolving threat landscape, vulnerability management is a daunting task. Every month thousands of new vulnerabilities emerge, creating a significant challenge for threat intelligence and vulnerability management analysts. The new integration between ThreatConnect and VulnCheck promises to address these challenges by offering a unified, intelligent approach to accelerating identification and analysis, and improving […]
