
Read insights, thought leadership, and platform updates.
No Blogs Match Your Results
Please try again or contact marketing@threatconnect.com for more information on our blogs.
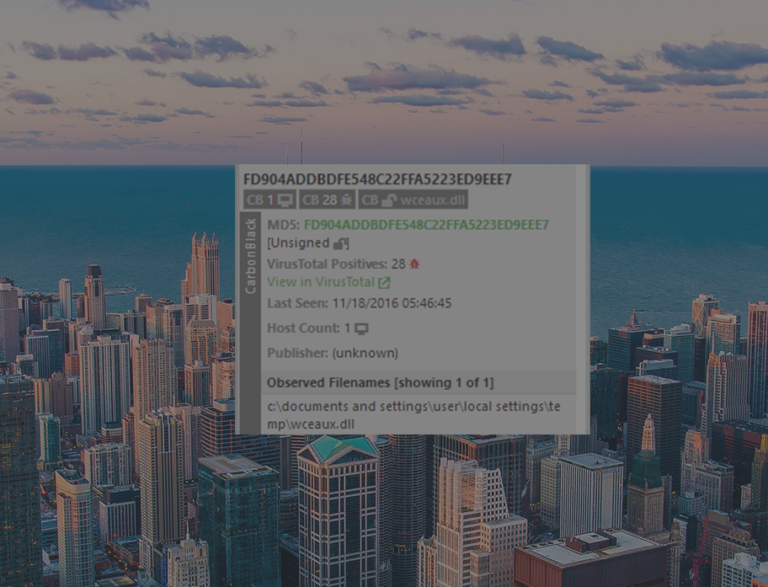
Know Every Binary That Has Ever Run in Your Environment
Binary file hashes are a common indicator used in information security. Unfortunately, files hashes are hard to read, let alone memorize. Here are some examples of what file hashes look like: 18f8e43b6de2dcf7c8e96af329ded882 0cc61d25f0e009e730e3a95d778325ed16ef26da 88237ec59eefc109f564e055216d8b7c6a4afd88ced7e3ef81a5801b083cecd2 I challenge you to memorize one of these, let alone the thousands that run in your environment every day. An information […]
Research One: A ThreatConnect Story
Research One: A ThreatConnect Story We’re excited to announce the availability of our newest product: TC Identify™, a threat-driven, context-enriched intelligence source provided through, and enabled by the ThreatConnect Platform. As we are wont to do with many of our notable announcements, we decided to draw a corollary to the Star Wars universe. Wait a […]
Towards Data-Driven Threat Analysis
Make Better Decisions Based on Your Indicators of Compromise A random person on the Internet once said, “Threat Intelligence is a lot more than Intel feeds.” This person was absolutely right. In fact, the very premise of a cybersecurity platform is that indicators of compromise (IoCs) alone are just one piece of your security puzzle, […]
Stepping to Fancy Bear
Stepping to FANCY BEAR (or how to efficiently validate and enrich a jumbled list of indicators) Over the last few weeks the U.S. government released two reports on Russian hacking and influence operations related to the U.S. election. Most notably, the unclassified version of the Intelligence Community Assessment (ICA) “Assessing Russian Activities and Intentions in […]
Do You Make Swords, or Do You Wield Them?
Classifying Analysts: Intelligence Producers and Intelligence Consumers The disciplines of swordsmith and swordsman have been intrinsically linked since the dawn of war. The swordsmith who crafted the sword is using a different skillset than the swordsman who wields the sword. In this same way, intelligence analysts come in two broad categories: intelligence producers and intelligence […]
How Companies Use ThreatConnect To Create a System of Record: A Use Case
This is the third in a series of blog posts about how organizations are utilizing the ThreatConnect platform. We’re going to share stories of how customers just like you have transformed their security programs using ThreatConnect, in particular, creating a cybersecurity system of record. In order to keep our customers secure, will be using pseudonyms […]
Hacktivists vs Faketivists: Fancy Bears in Disguise
What is a faketivist? One of the more surprising stories of 2016 was the Russian effort to shape the outcome of the U.S. presidential election. What surprised us most at ThreatConnect was not Russian APTs breaching the Democratic National Committee, but the efforts to “weaponize” that information through a campaign of strategic leaks. This stands […]
7 Threat Intelligence Tools Your Team Needs
In today’s world cyber criminals are working hard to constantly come up with new tools, techniques, and procedures to infiltrate networks, socially engineer users and employees, steal money or information, and assault various targets. As the bad guys’ methods expand, the security industry has responded to these evolving threats. There are hundreds of tools, services, […]
How Companies Use ThreatConnect to Make Their Cybersecurity Programs More Efficient: A Use Case
Make Your Cybersecurity Program More Efficient Using ThreatConnect This is the second in a series of blog posts about how organizations are utilizing the ThreatConnect platform. We’re sharing stories of how customers are transforming their security programs using ThreatConnect. How do I make my cybersecurity program more efficient? It’s a valid question that many organizations […]
How Companies Use ThreatConnect When Building Their Cybersecurity Program: A Use Case
Build Your Cybersecurity Program Using ThreatConnect This is the first in a series of blog posts about how organizations are utilizing the ThreatConnect platform. We’ll share stories of how customers just like you have transformed their security programs using ThreatConnect. Introducing Gringotts A Fortune 1000 Financial Services company, who we will call Gringotts, has a […]
Step 1: Collect and Correlate Relevant Threat Data
How to Aggregate Relevant Threat Data Is your cybersecurity team small? Or, are you looking to make your team more efficient? It can be difficult to know where to start when you have limited resources. Today we begin a six-blog series that will cover how to make the most of your cybersecurity program when you have […]
What is a Cyber Threat? How to Explain Cyber Threats to Your CEO
How to explain cyber threats to your CEO and others. Learn more about the potential for risk. What is a cyber threat? To explain what a cyber threat is to your CEO, you have to remember what your CEO cares about most: shareholders, revenue and profit, brand equity, company data – and speak in analogies […]
