
Read insights, thought leadership, and platform updates.
No Blogs Match Your Results
Please try again or contact marketing@threatconnect.com for more information on our blogs.
Kinetic and Potential Energy Framework: Applying Thermodynamics to Threat Intelligence
ThreatConnect proposes a framework for evaluating and triaging indicators based on physical energy properties All variety of scientists, from chemists to physicists and engineers, measure kinetic and potential energies to better understand how objects are acting or will act within a given situation or system. We posit that these energy concepts can be applied to […]

Polarity – Confluence Integration
Interoperability by Design is the foundation for our dynamic Integration Framework, allowing you to integrate with almost any database or API. The more you integrate the internal or 3rd party, commercial or open source, data you already use to Polarity, the more powerful Polarity becomes. Integrations make you, your teams, and your tools, exponentially more […]

Save Time By Recognizing Machine Time
Occasionally our users come across UNIX Epoch time, the representation of time as the number of seconds elapsed since January 1st, 1970. The representation was not meant to be human-readable and often users must convert the time to something more human consumable. For example, the UNIX Epoch timestamp 1445400000 will be converted into a representation […]
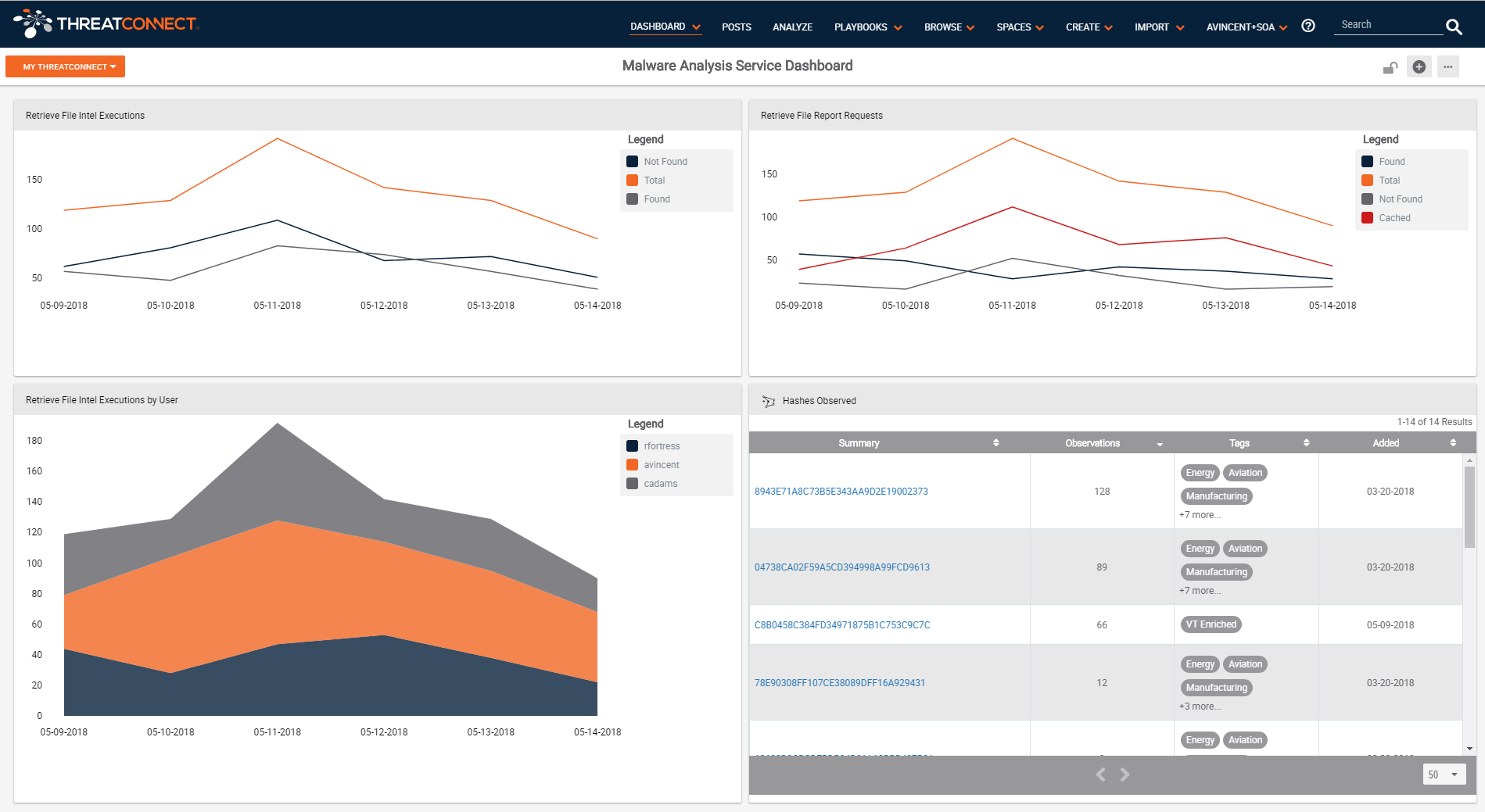
Playbook Fridays: How to Use ThreatConnect Playbooks to Manage Security APIs
Planning for APIs as part of your security architecture This is my first Playbook Friday blog post. I love the ones that the team creates and thought I would try my hand at one. That said, because I am not in the Platform as much as I’d like to be, I enlisted the help of […]
ThreatConnect and the Rise of the Security Developer
Taking Your Team & Career to the Next Level with ThreatConnect’s GitHub Repositories Going to the Next Level with ThreatConnect’s GitHub Repositories When I walk the show floors at RSA or Black Hat, I’m always struck by the number of new products that pop up every year. The “hot topic” varies – this year it […]
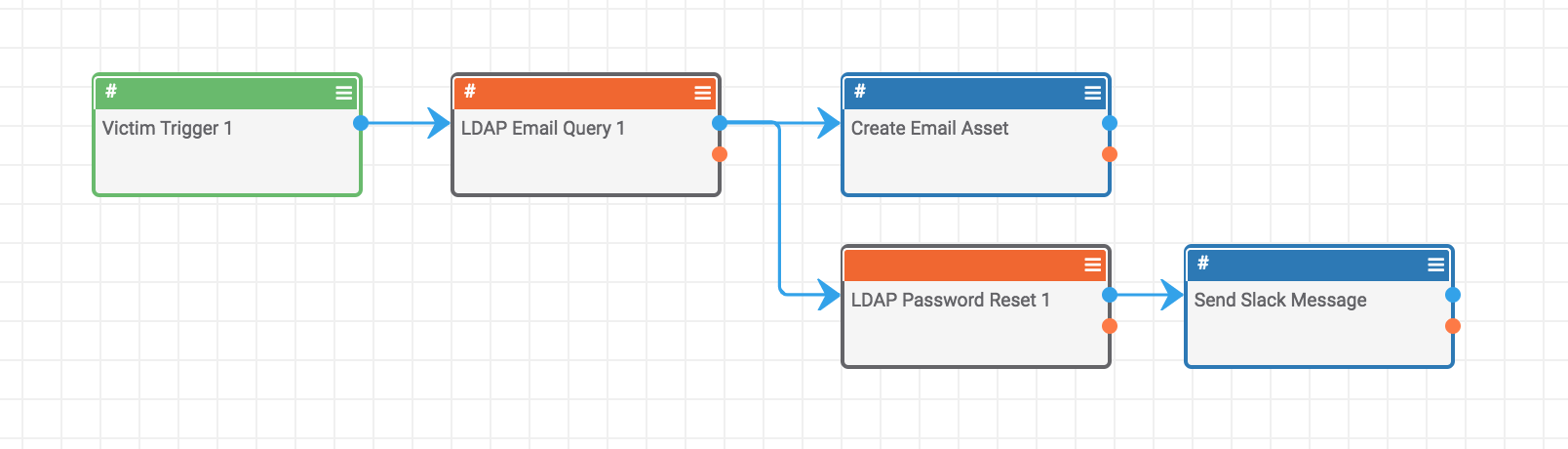
Playbook Fridays: Forcing Active Directory (AD) Password Resets via ThreatConnect Victims
Leveraging the Active Directory and ThreatConnect integration to help automate security processes ThreatConnect developed the Playbooks capability to help analysts automate time consuming and repetitive tasks so they can focus on what is most important. And in many cases, to ensure the analysis process can occur consistently and in real time, without human intervention. This […]
Introducing ThreatConnect’s Intel Report Cards
Providing insight into how certain feeds are performing within ThreatConnect As part of our latest release, we’ve introduced a new feature to help users better understand the intelligence they’re pumping into their systems. Intelligence can be a fickle thing; indicators are by their very nature ephemeral and part of our job is to better curate […]
Introducing ThreatConnect’s Intel Report Cards
Providing insight into how certain feeds are performing within ThreatConnect As part of our latest release, we’ve introduced a new feature to help users better understand the intelligence they’re pumping into their systems. Intelligence can be a fickle thing; indicators are by their very nature ephemeral and part of our job is to better curate […]

Introducing the Polarity Heads-Up-Display
What is a Heads-Up-Display (HUD)? A Heads-Up-Display, HUD for short, is a visual indicator that presents data to a person without having them look away from their usual viewpoints. A HUD was originally associated with a fighter pilot being able to see information in a heads-up position while looking forward, flying an aircraft. Different HUDs […]
The Power and Responsibility of Customer Data and Analytics
How ThreatConnect stores, uses, and protects customer data There has been a lot of recent news surrounding compromises in trust where companies purposefully or unintentionally misuse or allow others to misuse customer data. After my last post, in which I talked about the power of data and analytics, I thought it would a good time […]
Don’t Get Caught Up in the Hype of AI for Security
Don’t get caught up in the hype of artificial intelligence or machine learning. Does the product correlate and analyze alerts? When Nails are Exciting, Everyone Wants to Talk about Hammers… Sticking with the tool theme from my last post, data is ushering in “better” products in every industry, but why are we so enamored with […]

Annotating & Building a Collective Memory
What if you could build a collective memory across your team and teams that all your analysts could seamlessly benefit from? At Polarity, we post a lot about integrations and the extensibility of our Memory Augmentation Platform, but most customers have observed that building the collective memory across the team is even more valuable. One […]
