
Read insights, thought leadership, and platform updates.
No Blogs Match Your Results
Please try again or contact marketing@threatconnect.com for more information on our blogs.

ThreatConnect’s FedRAMP Authorization: A Landmark Achievement in Security and Collaboration
The road to achieving FedRAMP Authorization is not an easy one. It’s a rigorous process that requires time, effort, and unwavering dedication to security and compliance. At ThreatConnect, we have recently announced that we have reached this milestone, a testament to our commitment to providing robust cybersecurity solutions that meet the highest government standards. The […]

One Detection to Rule Them All: Lessons from Sauron’s Security Failure
Great Alerts, Terrible Prioritization “He is gathering all evil to him. Very soon, he will summon an army great enough to launch an assault upon Middle-earth.” Sauron had a detection program. But like many security teams, it was overly focused on indicator-based detection. His Eye swept across Middle-earth with constant surveillance. His Ringwraiths were real-time […]

From Intelligence to Business Impact: 2025 SANS CTI Survey + How ThreatConnect Helps
The 2025 SANS Cyber Threat Intelligence (CTI) Survey reveals a maturing discipline facing persistent challenges: lack of process formalization, difficulty proving ROI, and an urgent need to communicate value to business stakeholders. This article summarizes the survey’s key findings and explains how ThreatConnect’s Intel Hub Platform – which combines our TI Ops, Risk Quantifier, and […]
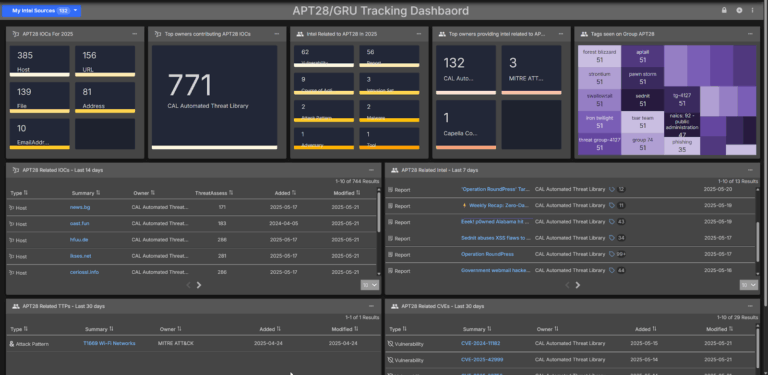
APT28 Intelligence Dashboard Immediately Available for ThreatConnect
APT28 is a Russian state-sponsored threat actor with a long history of sophisticated cyber operations targeting governments, defense contractors, and critical infrastructure sectors across the globe. According to a CISA advisory released on May 21, 2025 this group has been exploiting known vulnerabilities in routers and other network devices to gain persistent access to sensitive […]
Why Measuring Risk Quantitatively with MITRE ATT&CK is Critical for Decision-Making
In today’s dynamic cyber landscape, organizations face an evolving array of threats and vulnerabilities that challenge their resilience. Whether it’s defending against ransomware attacks, identifying critical vulnerabilities (e.g. CVE-2023-23397), or responding to adversaries’ rapidly changing tactics, being able to measure and understand risk is integral to staying ahead of potential threats. And when it comes […]

ThreatConnect’s Resident Disney Princess: Be like Alice, Don’t Fear the Rabbit Holes
The Advanced Persistent Talent series profiles ThreatConnect employees and explores how their work impacts products and offerings, how they got here, and their views on the industry at large. Want to know more about a particular team? Let us know! Good threat intelligence analysts have one trait in common: A persistent drive to learn, an […]

How Financial Services Companies Drive Informed Cyber Defense Programs with ThreatConnect
Many financial institutions face a constant influx of data from IOCs, open-source feeds, and internal sources that makes it difficult to consolidate and automate intelligence into actionable insights. Without a unified approach to threat intelligence, however, teams can miss critical threats and waste valuable resources on false positives. This is especially risky in a threat […]

How State and Local Agencies Can Rise to New Cybersecurity Mandates with ThreatConnect
Earlier this year, the Trump administration signed an executive order dictating that state and local governments should play a more significant role in national resilience and preparedness—including for cyber attacks. State and local agencies are the frontline of defense for much of the critical infrastructure that underlies our daily lives, such as our utilities, healthcare […]
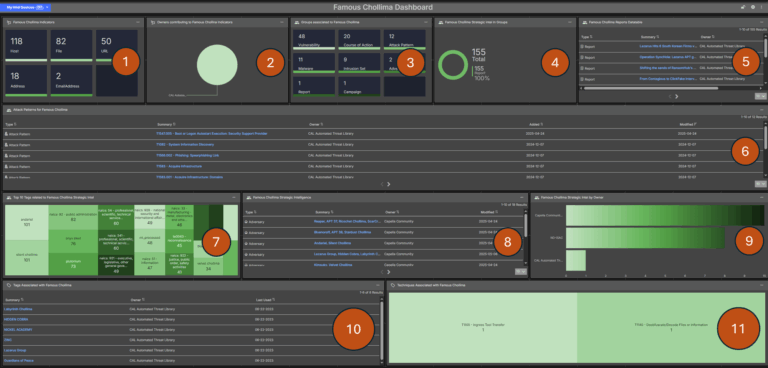
Famous Chollima Intelligence Dashboard Immediately Available for ThreatConnect
Famous Chollima is a North Korean state-sponsored cyber threat actor tracked as active since at least 2018. Their primary objective is to infiltrate organizations by posing as legitimate remote IT workers, thereby generating income for the North Korean regime and conducting cyber espionage activities. They are also known by aliases such as: NickelTapestry PurpleBravo TenaciousPungsan […]

Feedly and ThreatConnect: Delivering Curated Threat Intelligence with Context
Security teams need relevant threat intelligence delivered efficiently, with the context necessary to investigate and act. The new Feedly Threat Intelligence and ThreatConnect TI Op integration makes it easier to collect, enrich, and prioritize cybersecurity intelligence — helping analysts reduce noise and focus on what matters. Through this integration, Feedly’s AI-driven threat data is converted […]

Visit the ThreatConnect Museum of Cyber Defense Past and Future
Ancient wisdom tells us that we must learn from the past to better adapt to what lies ahead. To survive and thrive in the future threat landscape, we must discard artifacts of the past and embrace a more evolved future. That’s why at RSAC this year, the ThreatConnect team opened the ThreatConnect Museum of Cyber […]
5 Companies That Transformed Threat Intelligence Operations with Automation, AI, and Real-Time Collaboration
Cyber threats are growing in volume, complexity, and cost. Yet many organizations still struggle with disjointed workflows, alert overload, and outdated processes that prevent security teams from responding effectively. That’s where ThreatConnect comes in. ThreatConnect helps organizations shift from simply managing threat intel to truly operationalizing it—so they can move faster, reduce risk, and scale […]
