
Read insights, thought leadership, and platform updates.
No Blogs Match Your Results
Please try again or contact marketing@threatconnect.com for more information on our blogs.

Watch Our SE Take the Polarity Challenge
Watch one of our SEs take the Polarity Challenge, showing how quickly he can research indicators using Polarity’s Augmented Reality for security data.
Research Roundup: Mustang Panda PlugX Variant Samples and Decryption Script
Howdy, and welcome to the ThreatConnect Research Roundup, a collection of recent findings by our Research Team and items from open source publications that have resulted in Observations of related indicators across ThreatConnect’s CAL™ (Collective Analytics Layer). Note: Viewing the pages linked in this blog post requires a ThreatConnect account. In this edition, we cover: […]
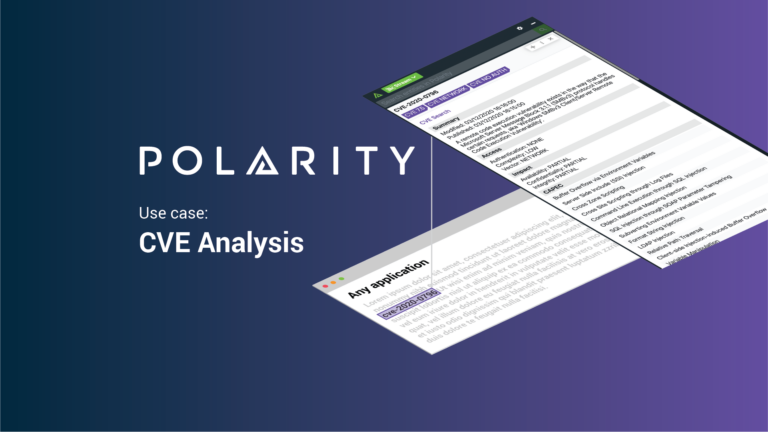
Polarity Use Case: CVE Analysis
Today’s post continues an ongoing series on Polarity Use Cases. Data tells a story, Polarity helps you see it with Augmented Reality overlaying contextual information as you work, giving you the right data at the right time to make informed decisions and take action with speed. No glasses or goggles required, Polarity is software that […]
ThreatConnect and VMRay: Better Malware Analysis
ThreatConnect and VMRay have improved our existing integration with VMRay Analyzer. This Playbook App will allow you to send malware to a sandbox to be further examined and results retrieved with VMRay Analyzer. Leveraging this App, you will be able to perform Phishing Email Triage, Endpoint Investigation, or Malware Hunting. This all leads to more […]
ThreatConnect Research Roundup: Twitter Hacked and APT29 Targets COVID-19 Vaccine
Howdy, and welcome to the ThreatConnect Research Roundup, a collection of recent findings by our Research Team and items from open source publications that have resulted in Observations of related indicators across ThreatConnect’s CAL™ (Collective Analytics Layer). Note: Viewing the pages linked in this blog post requires a ThreatConnect account. In this edition, we cover: […]

Rapidly Triage Network Detection & Response with the Polarity-Gigamon Integration
Today’s post continues an ongoing series on Polarity Integrations. Data tells a story, Polarity helps you see it with Augmented Reality overlaying contextual information from the applications you use every day, no glasses or goggles required. With over 100 powerful integrations, Polarity’s open-source Integrations Library arms you with the right data at the right time […]
ThreatConnect’s Security Operations Maturity Model
ThreatConnect is out to change the way security works with cybersecurity software that reduces complexity for everyone, makes decision making easy and unifies processes and technology to constantly improve defenses and drive down risk. It’s why we’ve evolved from our heritage as a leading Threat Intelligence Platform (TIP) to deliver a full suite of intelligence-driven […]

Polarity Reference Channels: Python Standards
Today’s post continues an ongoing series on Polarity User Tips. Data tells a story, Polarity helps you see it with Augmented Reality overlaying contextual information as you work, giving you the right data at the right time to make informed decisions and take action with speed (no glasses or goggles required). This guide explains how […]
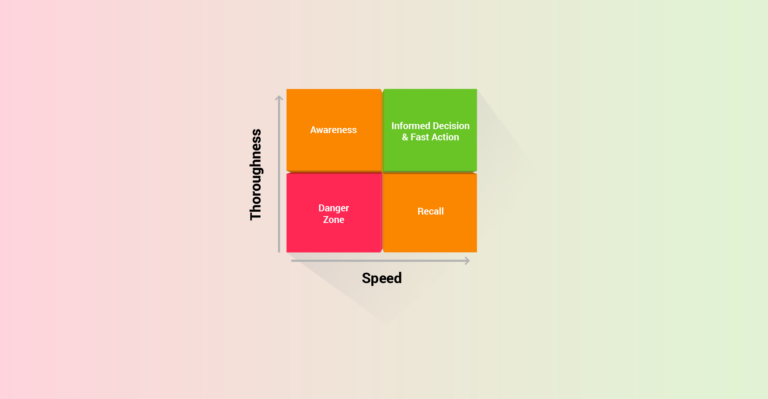
Survey Says: SOC Still Plagued by Inefficiency
There is no shortage of interesting research characterizing the challenges faced by SOC teams. Two recent reports from Exabeam and Devo/Ponemon include all the well known stats reminding us that SOCs suffer from too many tools, not enough people, and ongoing challenges with key metrics like MTTD and MTTR. Both reports also include a few unique perspectives on data […]
5 Reasons CISOs Need Security Operations, Automation, and Orchestration (SOAR)
At ThreatConnect, we are out to change the way security works by making cybersecurity software that reduces complexity for everyone, makes decision making easy and unifies processes and technology to constantly drive down risk. To make good on this core idea, we’ve evolved from our heritage as a leading Threat Intelligence Platform (TIP) to deliver […]
Realizing the Benefits of Security Orchestration, Automation, and Response (SOAR)
SAO, TIP, SIRP: Better Together When industry analyst firm Gartner, Inc. coined the term SOAR (Security Orchestration, Automation, and Response), it was because they recognized the benefits innately achieved when the capabilities of three previously very separate platforms are fused together: security orchestration and automation (SOA), security incident response (SIR) and threat intelligence platform (TIP) […]
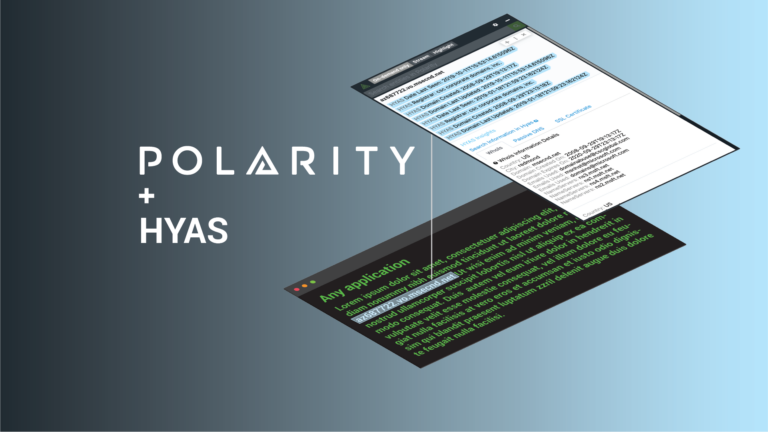
Immediately Triage Threats with the Polarity-HYAS Integration
Today’s post continues an ongoing series on Polarity Integrations. Data tells a story, Polarity helps you see it with Augmented Reality overlaying contextual information from the applications you use every day, no glasses or goggles required. With over 100 powerful integrations, Polarity’s open-source Integrations Library arms you with the right data at the right time […]
