
Read insights, thought leadership, and platform updates.
No Blogs Match Your Results
Please try again or contact marketing@threatconnect.com for more information on our blogs.
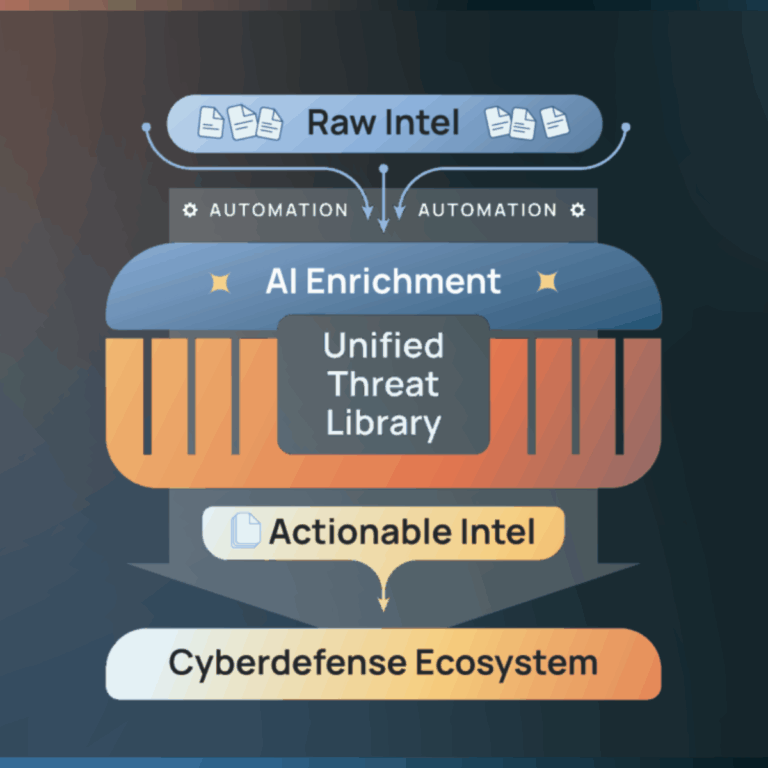
We’ve Hit the Tipping Point in Cyber Defense – Here’s the Fix
With expanding attack surfaces and rising burnout, aligning executives and security teams is more critical than ever. The Intel Hub transforms that alignment into decisive action. For years, cybersecurity teams have fought an asymmetric battle. Threat actors only need to succeed once. Defenders must succeed every time. But the rules of this game have changed […]
Threat-Informed, Financially Grounded: Modern Cyber Risk Quantification with MITRE ATT&CK and Threat Intelligence
As cybersecurity evolves – so do the tools designed to combat recurring problems that exist within. EDR replaced antivirus. MFA displaced passwords. XDR is basically SIEM dressed to impress. RBAC matured into PBAC/ABAC, and so on. Still, despite the tremendous progress with available security tools, today’s CISOs face increasing pressures to deliver clear and defensible […]

The Curious Case of the Vanishing Threat Intel – And How to Solve It
It began, as many mysteries do, with a statement of defeat. “There’s no way we could have prevented this.” Baskerville Bank had just suffered a crippling ransomware attack. Production systems were encrypted. The customer portal was dark for 12 hours. Operational disruptions cost over $3.2M, not counting the inevitable PR fallout, legal action, and suspected […]
Harnessing Generative AI Safely: Why Shadow IT Is Your Next Big Data-Leak Risk—and How Polarity Stops It
Generative AI (GenAI) tools like OpenAI’s ChatGPT and Google’s Gemini offer unparalleled productivity gains—but at what cost? According to the 2025 Verizon Data Breach Investigations Report, 15 percent of employees access GenAI on corporate devices at least once every 15 days—and of those users, 72 percent do so with personal (non-corporate) accounts while another 17 […]

Black Hat 2025: Exposure Management, AI Defense, but No Donuts
Every Black Hat is a bit of a mirror. It shows you the state of the industry, sure — but if you’re paying attention, it also reflects where you are as a practitioner and a company that’s been doing this long enough to notice the small changes. This year’s reflection? The hype is settling. Conversations […]

ThreatConnect’s Axe-Throwing, ex-CIA, Head of Product AI Research: AI Should Unlock Creativity, not Replace It
The Advanced Persistent Talent series profiles ThreatConnect employees and explores how their work impacts products and offerings, how they got here, and their views on the industry at large. Want to know more about a particular team? Let us know! One of the most prevalent criticisms of AI tools today is that they could be […]

ThreatConnect 7.10 is Live: Unified Vulnerability Intelligence, Enhanced Search, and Streamlined Workflows for Security Teams
Every vulnerability tells a story—but when that story is scattered across a dozen different intelligence feeds, understanding the real threat becomes nearly impossible. Consider the challenge: CVE-2023-23397 appears in your threat feeds with conflicting CVSS scores, fragmented timeline data, and intelligence buried across multiple sources. Your analysts burn hours manually connecting these dots while real […]

Why Pizza Parties Won’t Fix SOC Burnout — And How ThreatConnect Helps Put Humans Back at the Center
Security operations centers (SOCs) are burning out. And no, more pizza parties won’t fix it. According to the latest SANS SOC Survey, a staggering 84% of security professionals report feeling burned out. Nearly 70% say that relentless alert volumes are bleeding into their personal lives. Meanwhile, the cybersecurity workforce gap has grown 19% in the […]

Native Domain Abuse Alerting – Informing Threat Ops: ThreatConnect’s DomainThrasher
Typosquatting is a sneaky tactic where bad actors register misspelled versions of popular domain names—think amazn.com instead of amazon.com—to hijack traffic, mislead users, or even steal personal information. Every mistyped domain or accidental click that lands on a fake site instead of yours is a potential risk. In today’s threat landscape, protecting your brand means […]
Supercharge Your Workflow: Introducing Polarity’s Document Search and Enhanced API Security!
We’re thrilled to announce the latest release of Polarity Client and Server, packed with powerful new features designed to make your investigations faster, more secure, and more efficient than ever before! This update introduces a game-changing Document Search capability and significant enhancements to our API with new API Tokens, opening up a world of possibilities […]
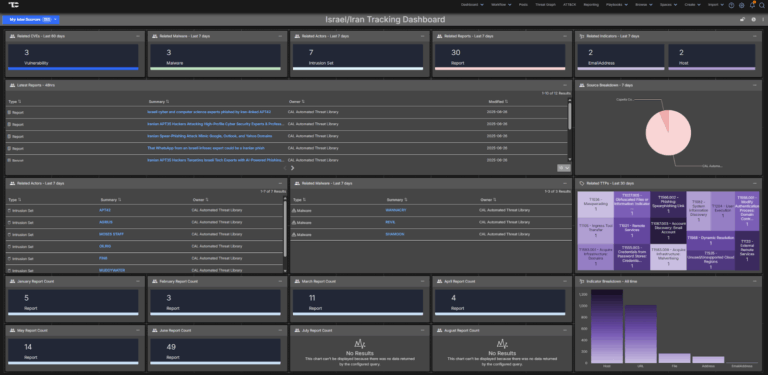
Israeli–Iranian Conflict Intelligence Dashboard Immediately Available for ThreatConnect
The geopolitical tensions between Israel and Iran continue to pose significant cyber and physical security risks to organizations across the globe. With threat activity emanating from advanced state-sponsored actors, hacktivist collectives, and opportunistic criminal groups, security teams must remain agile, informed, and proactive. The Israeli–Iranian Conflict Intelligence Dashboard is designed to equip defenders with timely, […]

ThreatConnect’s Non-Traditional Threat Expert: Sometimes You’ve Got to Look at the Bigger Picture
The Advanced Persistent Talent series profiles ThreatConnect employees and explores how their work impacts products and offerings, how they got here, and their views on the industry at large. Want to know more about a particular team? Let us know! People find their way to the world of threat intelligence in all sorts of ways. […]
