
Read insights, thought leadership, and platform updates.
No Blogs Match Your Results
Please try again or contact marketing@threatconnect.com for more information on our blogs.
From Data Overload to Decision Superiority — Avoiding SOC Burnout with Polarity
Modern SOCs don’t fail from lack of talent — they fail from tool fatigue. Analysts spend more time context-switching than analyzing. Polarity by ThreatConnect brings the context to them: federated search across SIEMs, SOARs, TIPs, Ticketing Systems, real-time overlays, and AI-assisted recall that cut cognitive load and improve mission tempo. Solving SOC Burnout with Real-Time […]

Wiz Integration Helps ThreatConnect Customers Act Faster and Reduce Vulnerability Noise
We’re excited to announce a new release that integrates Wiz Cloud Security Vulnerability Findings to ThreatConnect! This new capability will help customers prioritize vulnerabilities based on assets under the purview of Wiz Cloud Security. The combination of Wiz Cloud Security visibility and the vulnerability data across the numerous sources effectively improves the overall security posture […]
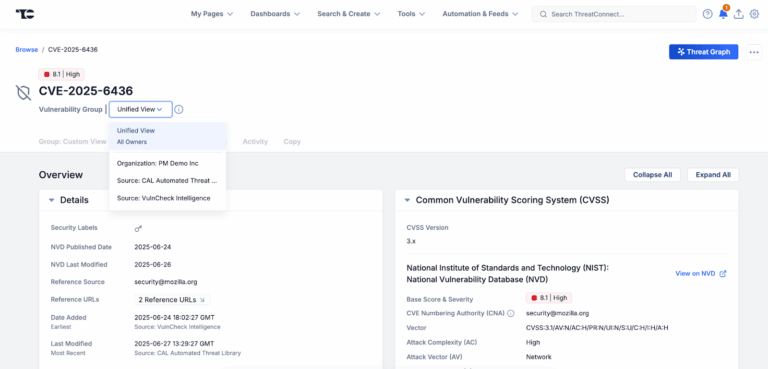
No More Frankenstein Feeds: One Unified View
Vulnerability Enhancements While attackers move quickly to weaponize real vulnerabilities, CTI teams need efficient ways to identify the signals vs. the noise. In a previous blog, we discussed the challenge of the abundance of data teams are faced with. Daily streams of unstructured vulnerability reports contain a small number of truly exploited zero-days mixed with […]

Joining Forces with Dataminr to Accelerate Threat and Risk‑Informed Defense
Today, I’m excited to share important news: ThreatConnect is merging with Dataminr, a pioneer in AI-powered threat, risk, and event intelligence across physical, digital, and cyber domains. Dataminr leads the world in AI-native real-time threat intelligence, empowering organizations like yours with rapid collection, processing, and alerting capabilities. This combination lays the foundation to strengthen your […]

ThreatConnect 7.11 is Live: Where Threat Intel Meets Convenience Store Efficiency
The newest release of TI Ops helps defenders cut through duplicate data, unify threat actor aliases, and focus on what matters most. Just like your favorite 7-Eleven is always open when you need that late-night snack or caffeine fix, ThreatConnect 7.11 is here to deliver cybersecurity convenience that never closes. The latest update stocks your […]

Continuous Control Validation with ThreatConnect Risk Quantifier 9.0
Cyber risk doesn’t wait until the next quarter. Neither should you. ThreatConnect RQ 9.0 let’s you keep up. With the launch of Risk Quantifier 9.0, security and risk leaders finally have a way to see what’s at risk, what it costs, and what to fix, continuously. Powered by Continuous Controls Monitoring (CCM), RQ 9.0 keeps […]
Beyond the Buzz: Analyst-First AI for MITRE ATT&CK
AI Buzzwords vs. AI Breakthroughs Analysts read reports every day that hint at adversary behavior but stop short of mapping to MITRE ATT&CK. Valuable context is lost, and blind spots grow. At the same time, vendors promise “AI-powered” features, but too often, what’s under the hood is little more than regex rules, keyword matches, or […]
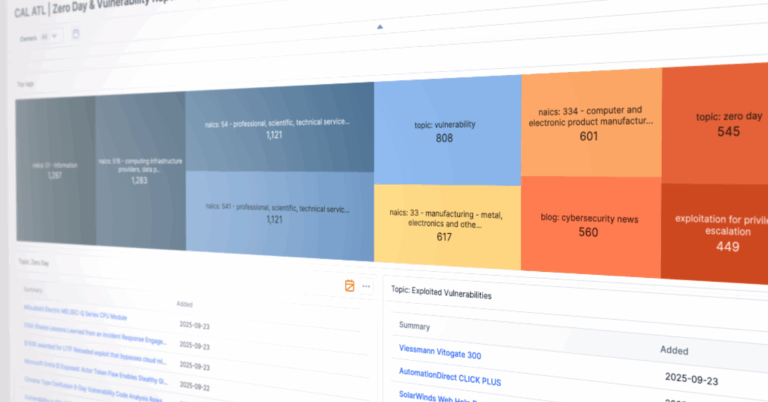
Noise vs. Signal: From Zero-Day Chatter to Actionable Intelligence
The Problem: When “Zero-Day” Means Everything and Nothing CTI Teams’ inbox and feeds overflow daily with mentions of “zero-day” vulnerabilities. Blogs, reports, vendor advisories, and social media all promise the next catastrophic exploit. But behind the scary headlines, there is a lot of noise, generic chatter, academic discussions, or even misplaced buzzwords. Meanwhile, attackers aren’t […]

ThreatConnect’s Director of Information Security & Compliance Shares the Three Keys to Managing Three Teams at Once
The Advanced Persistent Talent series profiles ThreatConnect employees and explores how their work impacts products and offerings, how they got here, and their views on the industry at large. Want to know more about a particular team? Let us know! When you’re operating in a small organization, flexibility is key. It’s not enough to wear […]

Closing the Gap Between Cybersecurity and Compliance: DORA as a Catalyst for Risk-Informed Decision Making
The Digital Operational Resilience Act (DORA) is pushing companies across Europe to demonstrate something many have struggled with for years: measurable resilience. It’s no longer enough to check the compliance box or hand over a set of controls during an audit. Regulators want evidence that organizations can withstand, respond to, and recover from ICT disruptions. […]
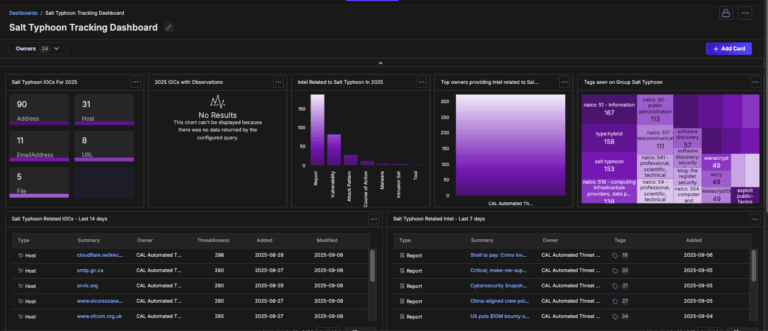
Salt Typhoon Intelligence Dashboard Immediately Available for ThreatConnect
Salt Typhoon—also known in industry and U.S. government reporting as OPERATOR PANDA, RedMike, UNC5807, or GhostEmperor — is a sophisticated, state-sponsored Chinese cyber-espionage group expected to operate under the Ministry of State Security. Active since at least 2019, Salt Typhoon has executed one of the most expansive and consequential global hacking campaigns in modern history. […]
Blending Worlds: How a Large UK Bank Connects Geopolitical, Cyber, and Physical Intelligence with ThreatConnect
Modern financial threats don’t respect boundaries. Inside a large UK bank’s journey to integrate intelligence and streamline response. I recently sat down with a top security intelligence analyst at one of the UK’s largest banks to talk about how they’re reshaping their intelligence program with ThreatConnect. What follows is their story, in their own words, […]
