
Read insights, thought leadership, and platform updates.
No Blogs Match Your Results
Please try again or contact marketing@threatconnect.com for more information on our blogs.

Preparing Organizations To Stop Ransomware in 2023
The new year is almost upon us, and 2022 has been a game of ransomware hardball. However, lessons learned this year can help organizations take proactive steps to protect themselves from ransomware in 2023. If you followed Cybersecurity and Infrastructure Security Agency (CISA) alerts on ransomware for the year, you would have noted malicious activity […]

ThreatConnect’s Intelligence Anywhere Puts Critical Information Within Fast and Easy Reach
In cybersecurity, contextual data is important. Contextual data with speed becomes everything. But many cybersecurity teams are too far away from the critical information they need to make fast and accurate decisions. Time is not on your side. It is just an unfortunate fact that threat and security researchers spend too much time digging through […]

Intelligence-Powered Security Operations: Evolve Beyond Traditional SecOps
In the fast-paced, ever-changing cybersecurity landscape today, organizations recognize the need to transform their security operations to achieve greater effectiveness and deliver better protection while demonstrating a measurable return on investment. When threat intelligence operations (TI Ops) infuses cyber threat intelligence into everything a security team does, it results in better decision-making, greater efficiency, and […]

Intelligence-Powered Security Operations Can Propel U.S. Critical Public Infrastructure to Meet New Cybersecurity Performance Goals
The stakes facing USA’s critical public infrastructure organizations in today’s threat environment are higher than ever before. Targeted with an onslaught of relentless attacks and malicious activity, threat actors can and must be stopped every single time. Through a combination of prevention and blocking, if even one successful attempt to sabotage a water system, community […]

It’s Time to #StopRansomware With Vulnerability Prioritization and Remediation
One of the main tips & guidance from the Cybersecurity and Infrastructure Security Agency (CISA) is to “Keep Calm and Patch On.” CISA emphasizes addressing vulnerabilities twice in this section. Two out of the four tips focus on the importance of finding and addressing vulnerabilities. For many organizations, that’s easier said than done. Vulnerability management […]

Healthcare Email Threats are Growing – Combat Them with Phishing Analysis & Response
In recent years, healthcare providers are increasingly being targeted with coordinated, sophisticated Phishing and Business Email Compromise (BEC) campaigns. As these attacks continue to grow, security teams need tools to help save time and address the threats more effectively. In one recent example, the Health and Human Services Health Sector Cybersecurity Coordination Center (HHS HC3) […]
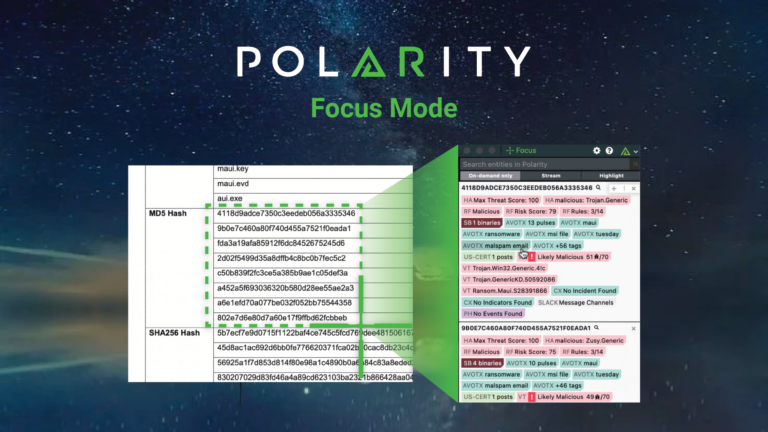
Polarity Focus Mode
With Polarity Focus, you can get the power of Polarity’s On-Demand Mode using any application, from Wireshark to images! Just hit a quick shortcut key and select the area of your screen you want Polarity to search. Not only that, but you can also copy any text that was recognized in the screenshot and the […]

Improve SOC Efficiency with Intelligence-Powered Security Operations
The critical challenge for Security Operation Centers (SOC) is minimizing the window of opportunity for attackers by quickly detecting and responding to threats. The time taken to detect and mitigate the threats are tracked by two metrics: Mean Time To Detect (MTTD) and Mean Time To Respond (MTTR). The efficiency of the SOC is typically […]

Maximize Impact with ThreatConnect 6.7
At ThreatConnect, we enable teams to achieve maximum impact on their security program by improving insights, efficiency, and collaboration. We are continuously building and iterating on our Platform based on feedback from our customers to simplify processes, speed up security tasks, and deliver a seamless user experience. The ThreatConnect 6.7 release delivers a more streamlined […]

ProxyNotShell Zero-day Vulnerabilities Exposed
The Latest on ProxyNotShell and How To Respond If You’re Impacted Word is spreading fast about two of the newest zero-day (0-day) vulnerabilities targeting Microsoft Exchange servers, now referred to as “ProxyNotShell” – and how their initial mitigations fell short of expectations. Given the evidence that these vulnerabilities are already being exploited to mount attacks […]
Cloud-Delivered Cyber Threat Intelligence Platforms Bring Quick Time to Value
If you don’t have a cyber threat intelligence (CTI) platform, then you need one. The challenge is getting your entire security team, from the CSO or CISO to the security and threat-analyst teams in the trenches, trained and able to use the platform to support daily incident response, network defense, and threat analysis. That’s the […]
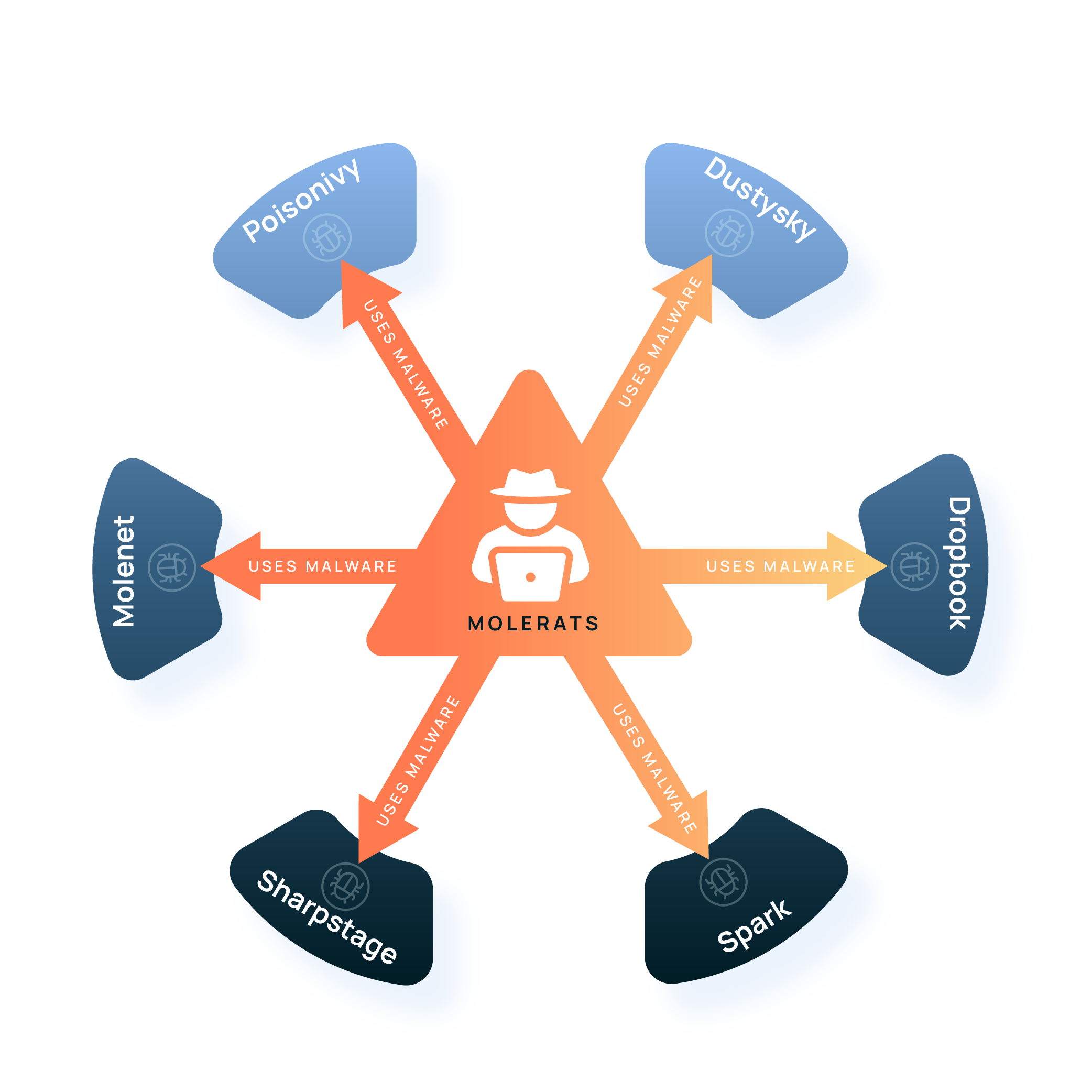
Threat Graph – Seeing is Believing
We all know the saying that, “a picture is worth a thousand words.” It is a fact that people derive meaning faster from imagery and graphics. At our core, humans are visual. Imagery can convey thoughts much faster and more efficiently than just words. Consider an example where you need to describe the shape of […]
