Posted
Vulnerability Enhancements
While attackers move quickly to weaponize real vulnerabilities, CTI teams need efficient ways to identify the signals vs. the noise. In a previous blog, we discussed the challenge of the abundance of data teams are faced with. Daily streams of unstructured vulnerability reports contain a small number of truly exploited zero-days mixed with commentary, duplicates, and general discussions. Analysts need clearer signals to focus on what’s actively being weaponized in the wild.
To make matters more complex, on a daily basis, analysts face an onslaught of vulnerability data from a variety of sources. They have to keep track of those sources, collect the relevant details, and compile all available context to ensure they have the fullest picture of the threat posed by recently identified vulnerabilities. This process takes significant time, energy, and brain power away from the actual defensive measures, and it doesn’t have to be this way.
With ThreatConnect’s new data consolidation capability, users can quickly access all available information about a given vulnerability in one place. This consolidation happens automatically, starting with the most recently added vulnerabilities, and connects all data available about a given vulnerability across the different sources and feeds a user has available to them. With this capability, analysts can trust that when they visit a Vulnerability Details page in ThreatConnect, they are seeing all of the available information about that Vulnerability. All of the attributes, tags, and associations from the various sources and feeds the user has enabled are captured, cited, and displayed in a Unified View, providing a single page that can be used for contextualization.
Accessing the New Unified View
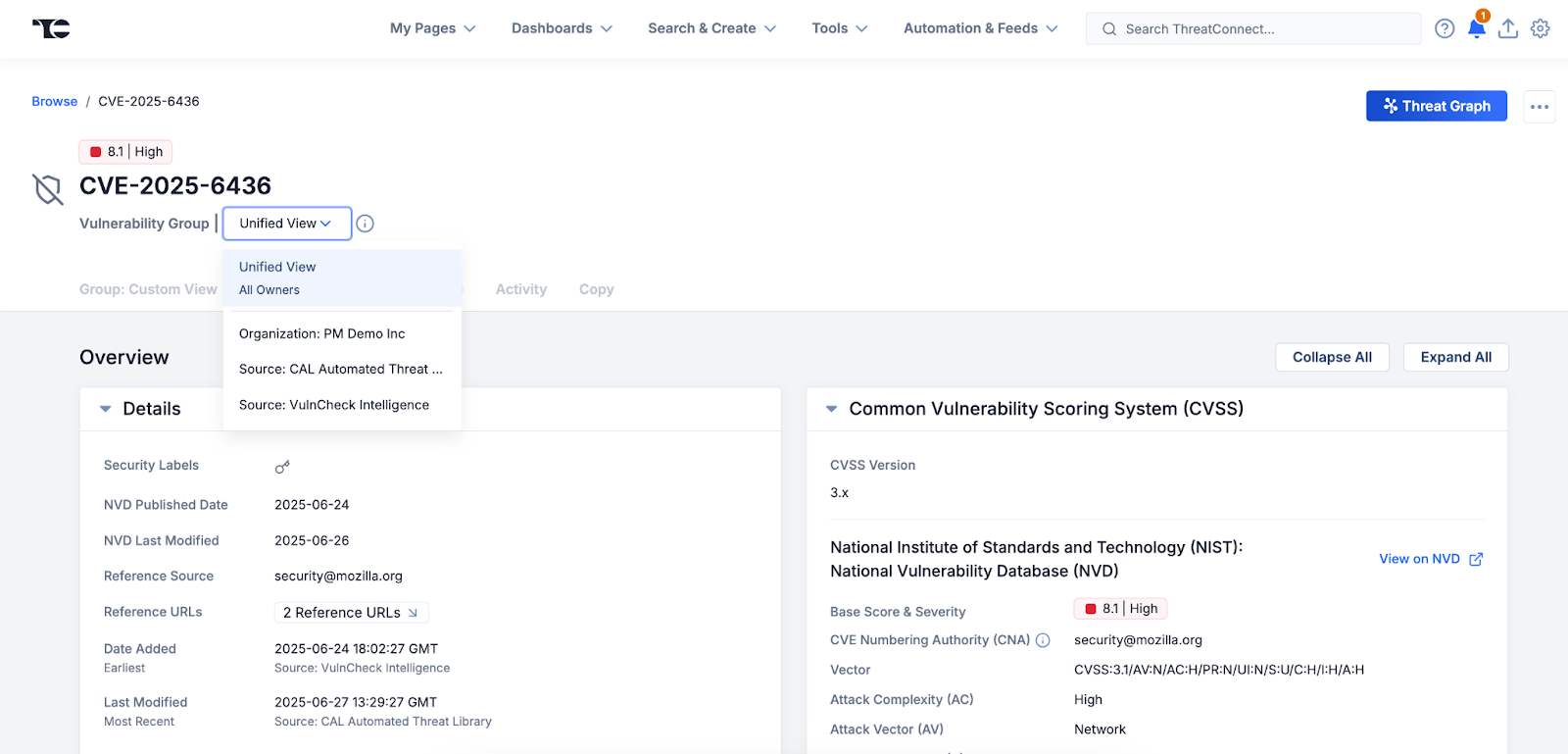
When a user clicks to open a Vulnerability Details page, if that Vulnerability has a Unified View option, the Unified View for that Vulnerability will automatically open by default. Users can choose to visit a specific version of the object by clicking the dropdown at the top of the Details page and selecting the version of the Vulnerability they want to view. However, it is notable that the data on every specific version of the object is available in the Unified View as well. As previously mentioned, the attributes, tags, and associations for a particular version of a Vulnerability are all cited and easily accessible via the Unified View.
Users can view a specific version of the Vulnerability via the Menu
CVSS AND KEV Data
In addition to consolidating the various versions of a Vulnerability that a user may have access to from the different sources and feeds they have in ThreatConnect, 7.10 also introduces two new cards on the Vulnerability Overview tab, Common Vulnerability Scoring System (CVSS) and Known Exploited Vulnerability (KEV). These cards are available on all Vulnerability object overview tabs as of 7.10, and the information in the card does not differ between the different versions of a vulnerability.
CVSS versions
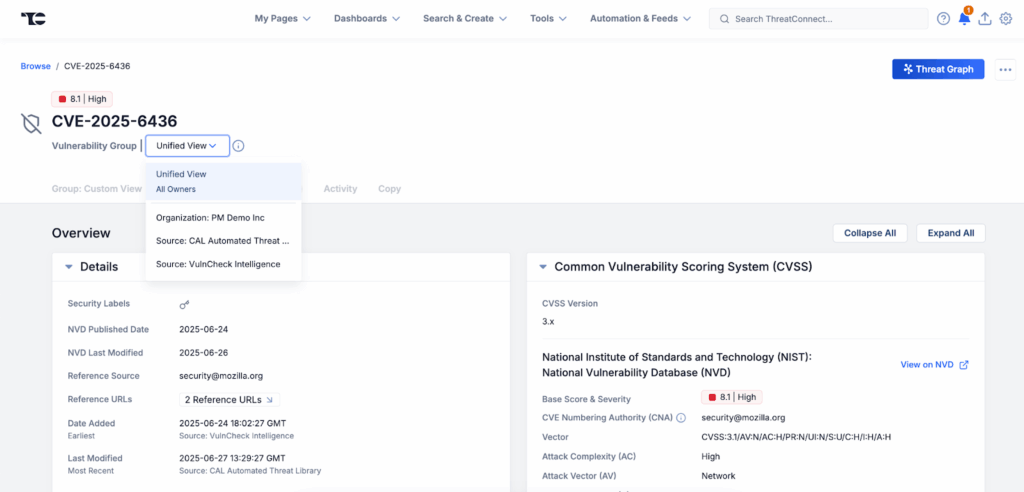
The data displayed in the CVSS card are pulled directly from the National Institute of Standards and Technology (NIST) National Vulnerability Database (NVD) and displayed in ThreatConnect for your convenience. If there is more than one CVSS version available for a given vulnerability, then the user will have the option to view the fields from each CVSS version by selecting one of the radio buttons next to the CVSS version number at the top of the card.
Users can navigate to different CVSS versions using the radio buttons
KEV data and fields
Similar to the CVSS information, KEV data is pulled directly from the U.S. Cybersecurity and Infrastructure Security Agency (CISA) Known Exploited Vulnerabilities Catalog. The data is displayed in the KEV card as shown below with links to related CWEs and additional notes, as available. This information is presented as provided by CISA, and does not undergo any additional validation or enrichment before being shown in the ThreatConnect UI.
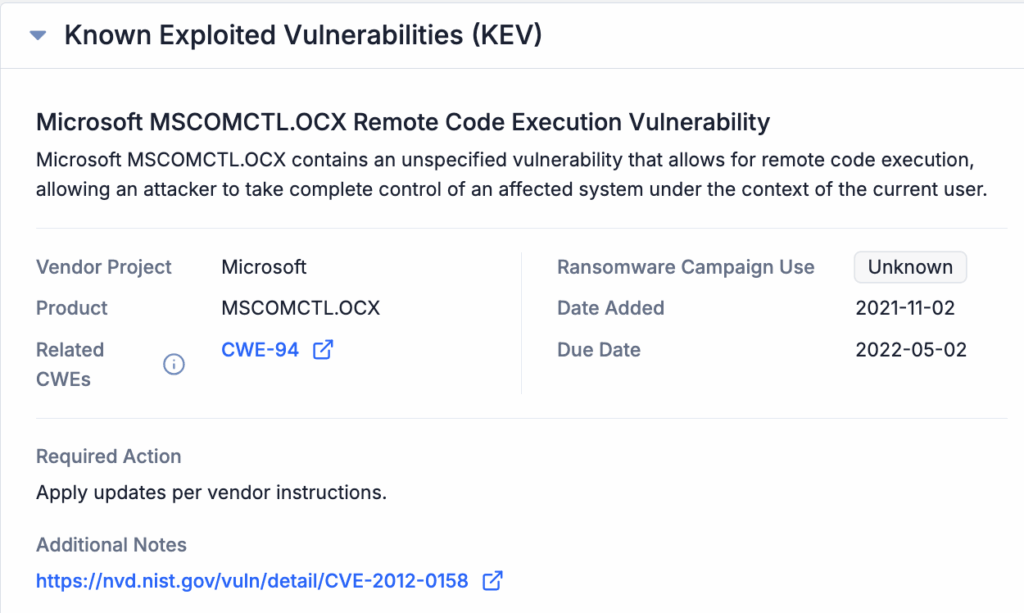
KEV data is presented exactly as provided by CISA
The Creation of a Unified View
In this version of ThreatConnect, the consolidated versions of Vulnerabilities are created automatically without any user action required. Upon updating to ThreatConnect 7.10, a monitor will begin running at a regular interval. The monitor looks for Vulnerability objects in your instance that share a name/summary. Any vulnerability objects that have the exact same name as another vulnerability object available in your instance will be connected to one another and available in a Unified View.
Because the data stored in a ThreatConnect instance can vary from customer to customer, it may take a few days for the monitor to consolidate vulnerabilities across an instance. However, if you notice vulnerability objects are not being unified after the initial few days, please reach out to your customer success representative for assistance.
Bottom line: These enhancements to vulnerability data transform overwhelming vulnerability noise into precise, actionable intelligence – letting analysts focus on defending against real threats instead of chasing false leads.