Posted
Splunk Users Can Now Launch Playbooks Directly from Splunk With ThreatConnect App Updates
Earlier this week, the latest ThreatConnect App for Splunk (v3.1) was released to Splunkbase. This release for Splunk is all about taking action and enabling our customers to fully leverage the power of the ThreatConnect Platform while working directly inside Splunk or Splunk Enterprise Security. This is a big release for us, and one in which Splunk users will see a lot of benefit.
Launch Playbooks Directly from Splunk
The ThreatConnect App for Splunk has always provided Splunk users the ability to leverage customizable threat intelligence integrated into Splunk from their ThreatConnect accounts. Now, as seen in Figure 1 below, you can launch ThreatConnect Playbooks directly from the Splunk interface.
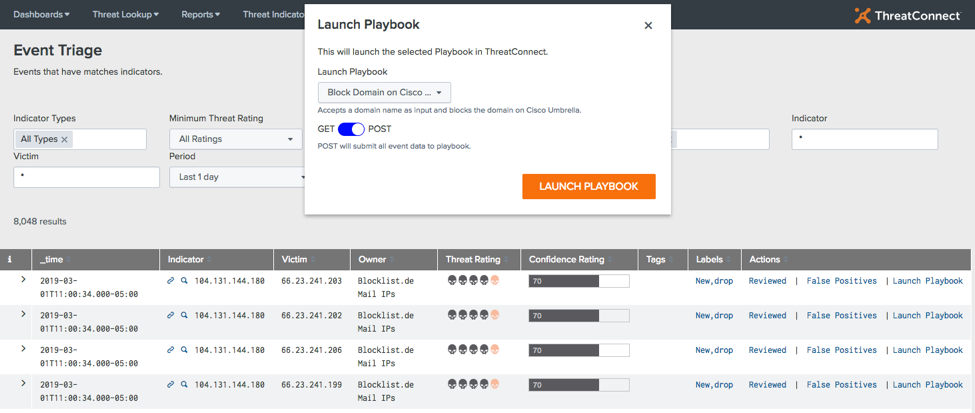
Figure 1: Launch a ThreatConnect Playbook directly from the Splunk interface
Manage Downloading and Configuration of Playbook Workflow Actions
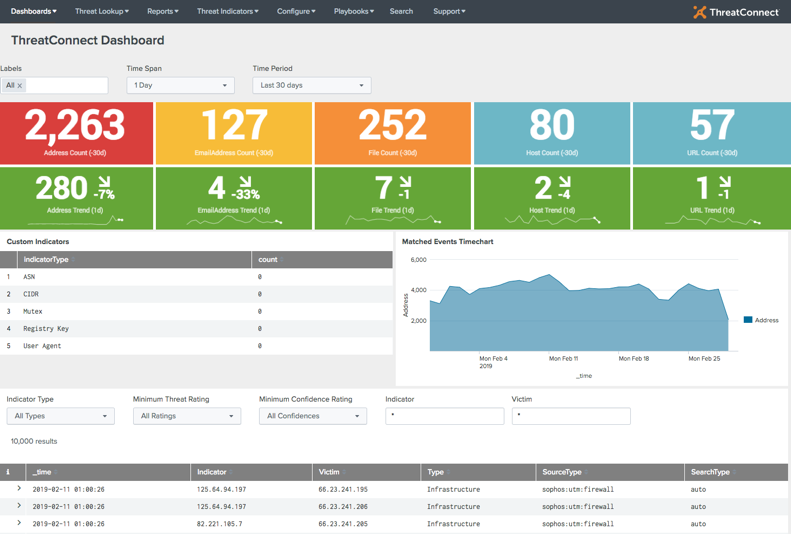
Directly from the ThreatConnect App Dashboard, you’ll now see a Playbooks option in the navigation (Figure 2). This is where you can manage the downloading and configuration of Playbooks from ThreatConnect, and the configuration of Playbook Workflow Actions all without worrying about logging into a separate Platform or interface.
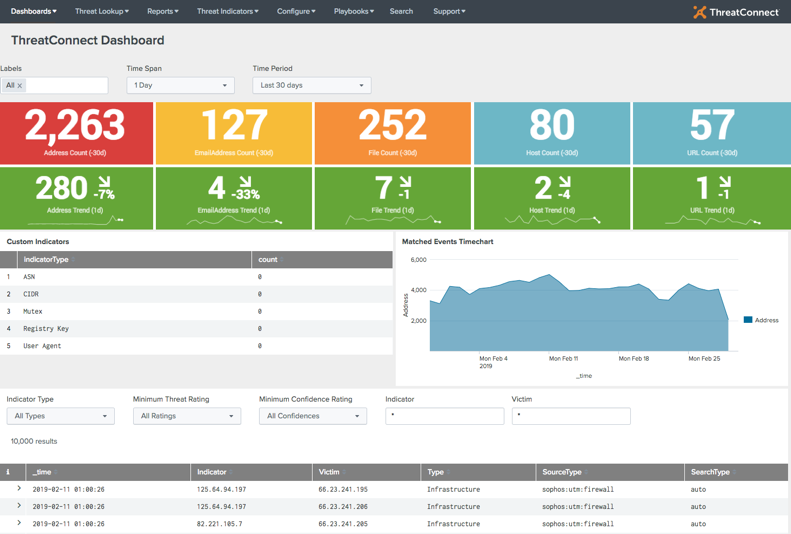
Figure 2: ThreatConnect Dashboard view from within Splunk
Make Faster Decisions with Automation and Orchestration
What’s this mean? Well, now Playbook Actions can be leveraged right from the Event Triage Dashboard, as part of Enterprise Security Adaptive Response, and as a part of Workflow Actions on Events. Integrate threat intelligence into response efforts while tying your technologies together to orchestrate decision making based on Events happening in Splunk.
For more information, reach out to sales@threatconnect.com for a demo. If you’re a current customer, please reach out to your designated Customer Success team for details.