Posted
Together, ThreatConnect and Carbon Black provide a complete solution for security teams
We’re excited to announce the release of a large bundle of ThreatConnect Playbook Apps with Carbon Black Response (CB Response). This set of Apps greatly increases the ability to take investigative and response actions across enterprise endpoints from the ThreatConnect Platform.
Integrating ThreatConnect and Carbon Black enables analysts like you to organize threat indicators as well as proactively hunt for past and present threats across the organization. With the addition of these new Playbook Apps, immediate actions can be taken to investigate, stop, and remediate potential threats at the endpoint based on external threat intelligence.
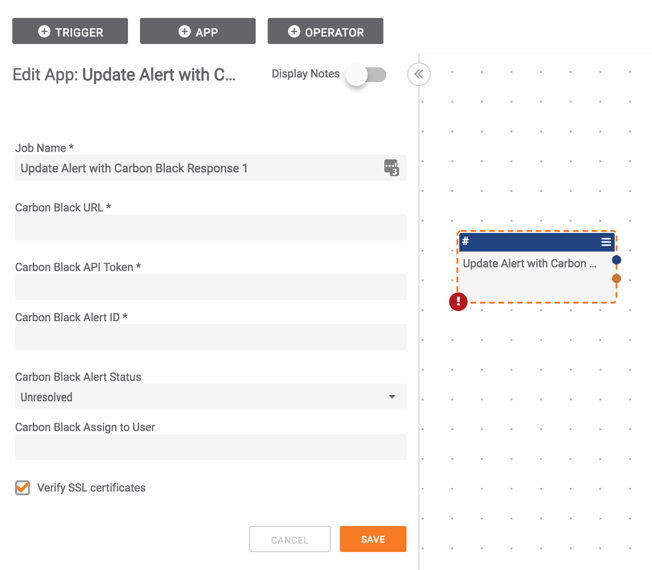
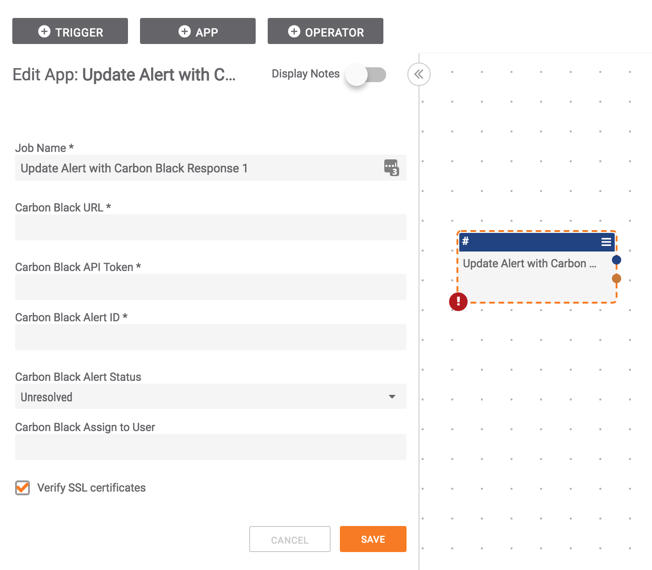
The following 20 Apps are available and enable you to take action in CB Response directly from ThreatConnect (as seen in the screenshot below):
- Alert Search with CB Response
- Ban MD5 Hash with CB Response
- Binary Search with CB Response
- Create CB Response Watchlist
- Create File on Sensor with CB Response
- Delete File from Sensor with CB Response
- Directory Listing with CB Response
- Download Binary with CB Response
- Get Process List from Sensor with CB Response
- Get Sensor Details by ID with CB Response
- Get Sensor Details by Name with CB Response
- Get Watchlist by ID with CB Response
- Get Watchlist by Name with CB Response
- Isolate Sensor with CB Response
- Kill Process on Sensor with CB Response
- Process Search with CB Response
- Retrieve File from Sensor with CB Response
- Unisolate Sensor with CB Response
- Update Alert with CB Response
- Update Watchlist with CB Response
Together, ThreatConnect and Carbon Black provide a complete solution for security teams that enables them to detect threats and perform remediation quickly and precisely by utilizing tools that communicate with each other.