Posted
Typosquatting is a sneaky tactic where bad actors register misspelled versions of popular domain names—think amazn.com instead of amazon.com—to hijack traffic, mislead users, or even steal personal information. Every mistyped domain or accidental click that lands on a fake site instead of yours is a potential risk. In today’s threat landscape, protecting your brand means guarding not just your main domain—but every letter around it.
Cybercriminals often use typosquatted sites to mimic real ones and:
- Harvest user data
- Spread malware
- Phish for login credentials
At ThreatConnect, we understand that typosquatting and combo-squatting aren’t just technical nuisances—they’re real threats to your brand reputation, customer trust, and digital marketing investments. That’s why we developed the DomainThrasher capability for all ThreatConnect customers, a purpose-built capability designed to help our customers proactively detect and investigate spoofed domains before they become a problem.
How It Works
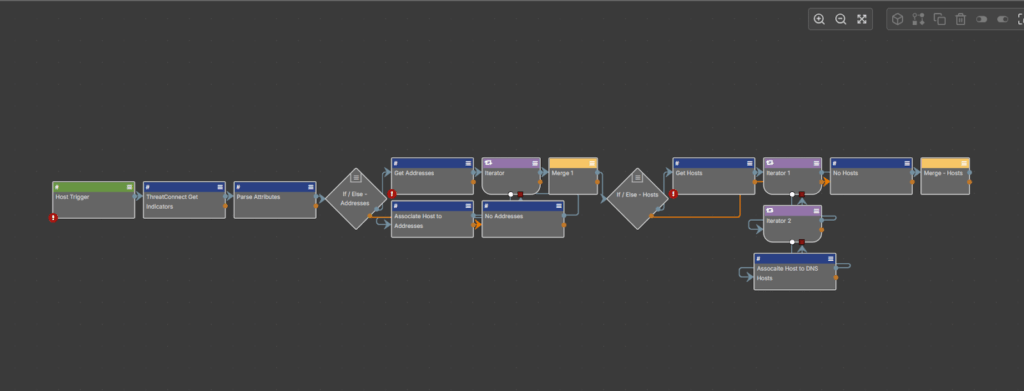
DomainThrasher is powered by two integrated playbooks:
DomainThrasher – DNSTwist, which automatically generates and enumerates potential squatting domain variants using the intelligence of DNSTwist. Customers can add many domains to the DomainThrasher playbook.
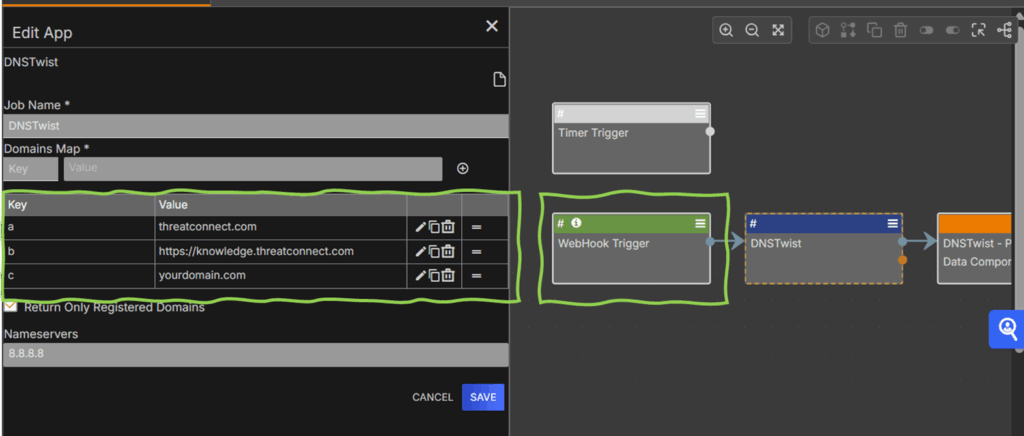
- DomainThrasher – Domain Associations, which processes and enriches those findings, giving teams actionable context to assess threats and respond confidently.
Lead Contributor(s) – Emmet Wray (Director, Customer Success Engineering, Mike Summers (Sales Eng.) & Layne Peterson (System Eng.)
With DomainThrasher, ThreatConnect customers gain automated, scalable insight into domain-based threats, helping them stay one step ahead of brand impersonators and malicious actors—because protecting your brand starts with seeing what others might miss.
How does your Company Access DomainThrasher?
To gain access to the DomainThrasher Playbook and capabilities, please reach out to your Customer Success team or email us at customersuccess@threatconnect.com.
This KnowledgeBase article can be used to guide the setup.
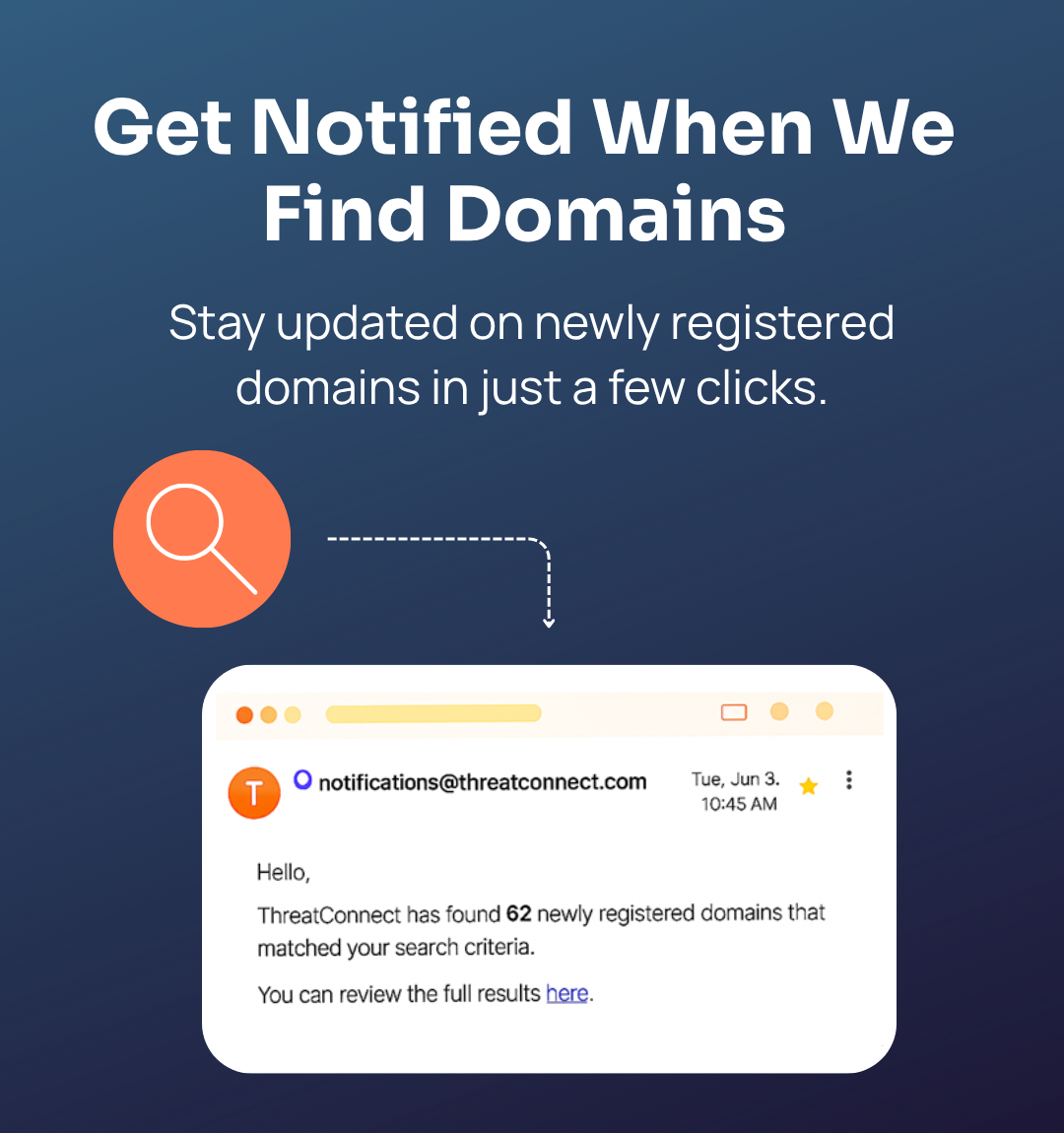
The End Result
On a frequency of your choosing, you can receive notifications of potentially malicious domain registrations based on the domains you have identified for priority monitoring.
The email communications can be directed to any individual or team, including those in the CTI function, those with brand monitoring mandates, fraud teams, or those who can initiate takedown services.
These communications will create out-of-band awareness for those who work outside of the ThreatConnect TI-Ops platform. However, the in-platform dashboards are also a great way to review and action the identified domains.