Posted
Mustang Panda—also known in industry and government reporting as BASIN, BRONZE PRESIDENT, CAMARO DRAGON, EARTH PRETA, FIREANT, G0129, HIVE015, HoneyMyte, LUMINOUS MOTH, Polaris, RedDelta, STATELY TAURUS, TA416, TANTALUM, TEMP.HEX, TWILL TYPHOON, or UNC6384—is a highly active, state-sponsored Chinese cyber-espionage group assessed to operate under the People’s Republic of China (PRC). Active for over a decade, the group is distinguished by its high operational tempo and “volume over stealth” approach to espionage.
Mustang Panda has consistently targeted entities that intersect with Beijing’s geopolitical priorities, particularly government and diplomatic institutions, maritime logistics organizations, and religious institutions. Their campaigns demonstrate a persistent focus on intelligence collection related to foreign policy, trade routes, and sensitive diplomatic engagements.
Multiple cybersecurity vendors and government agencies assess with high confidence that Mustang Panda operates in alignment with PRC strategic objectives, based on victimology patterns, infrastructure choices, and activity timing that aligns with Chinese working hours (UTC+8).
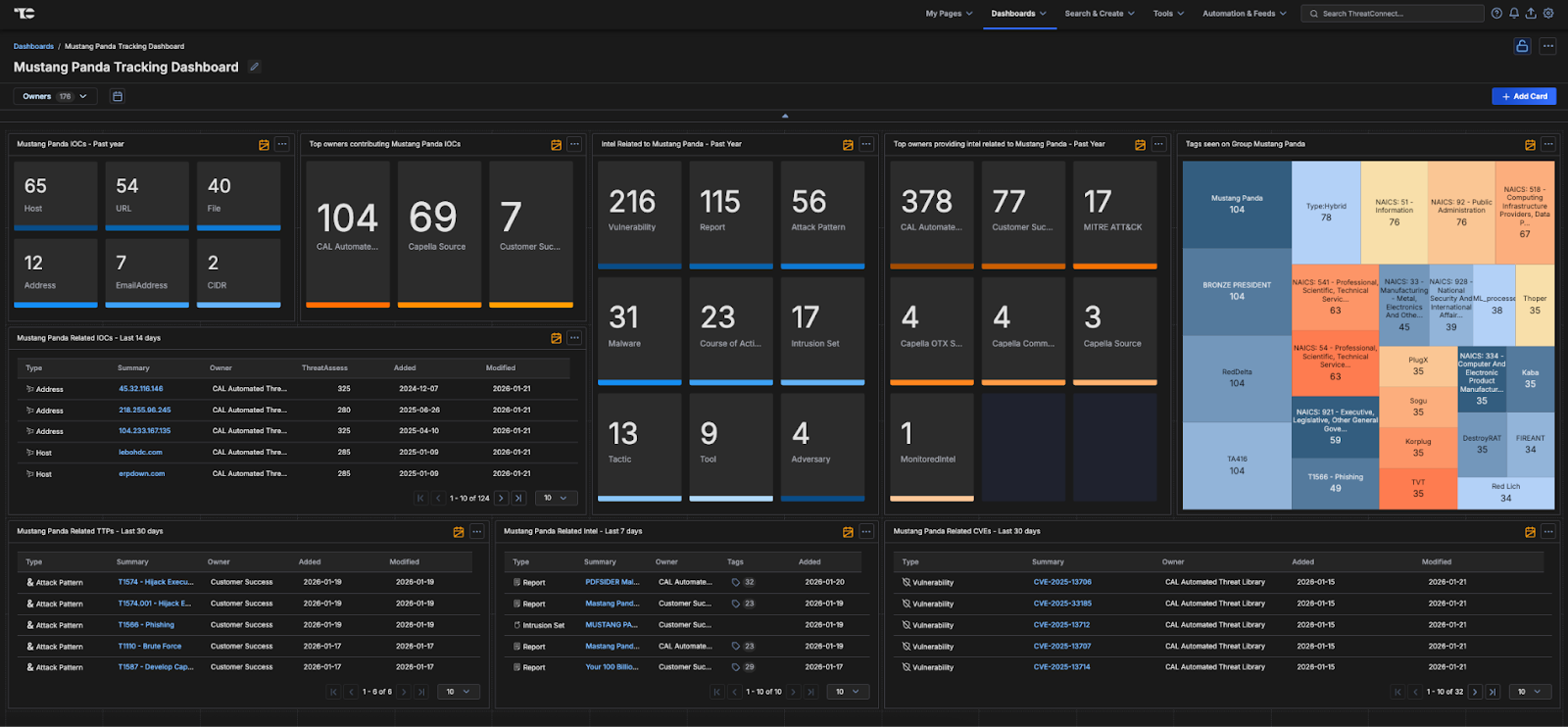
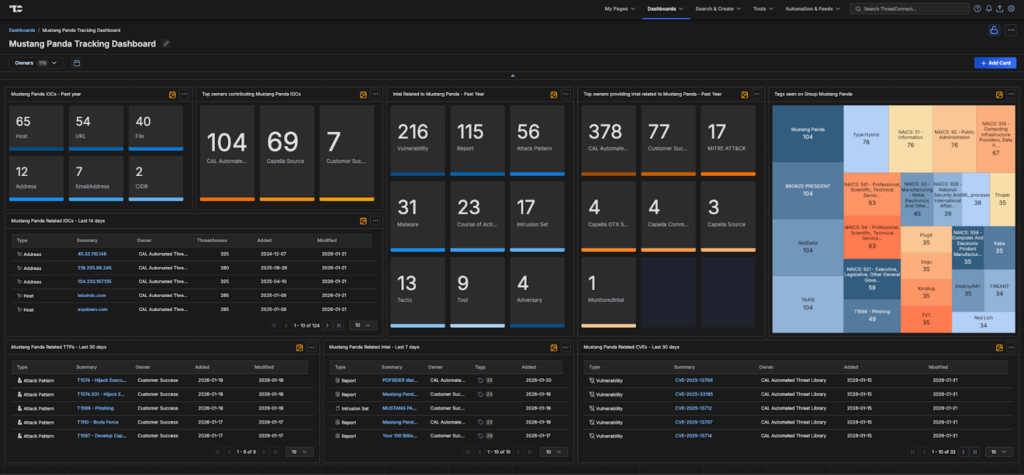
The new Mustang Panda Dashboard in ThreatConnect offers security teams centralized visibility into this highly active and adaptable adversary.
Key Benefits:
- Centralized Intelligence: Aggregates Mustang Panda-related IOCs, TTPs, malware families, and campaign telemetry from open sources, commercial feeds, and internal data.
- Continuous Threat Tracking: Monitors real-time updates on actor infrastructure, targeting patterns, and evolving tradecraft.
- Accelerated Incident Response: Provides enriched, contextual intelligence to reduce detection-to-response timelines.
- Visual Reporting & Executive Insights: Interactive charts, timelines, and executive-ready dashboards support risk prioritization and communication.
- Automated Correlation: Leverages ThreatConnect’s automation engine to map Mustang Panda indicators across intrusion sets, malware families, and victim profiles.
Mustang Panda’s consistent targeting of government, diplomatic, and maritime entities underscores the ongoing risk to sensitive political and economic interests worldwide.
The Mustang Panda Dashboard equips defenders with the ability to visualize campaigns, correlate activity, and act decisively—directly within the ThreatConnect platform.
Note: To maximize the value of this dashboard, organizations may benefit from integration with premium threat intelligence sources such as Dataminr, Mandiant, Recorded Future, or CrowdStrike.
Lead Contributor – Travis Meyers, Customer Success Manager
To gain access to the Mustang Panda Dashboard, please connect with your Customer Success team or reach out to us through our contact form.
Further Resources
For more detailed information and resources on Salt Typhoon, please refer to the following:
| Resource | Description | Link |
| MITRE | As a not-for-profit organization, MITRE acts in the public interest by delivering objective, cost-effective solutions to many of the world’s biggest challenges. | MITRE Article |
| The Hacker News | THN Media Private Limited, the parent organization behind The Hacker News (THN), stands as a top and reliable source for the latest updates in cybersecurity. As an independent outlet, we offer balanced and thorough insights into the cybersecurity sector, trusted by professionals and enthusiasts alike. | THN Article |
| Reuters | Reuters is the leading global source of news coverage. We have been licensing content and information to media organizations, technology companies, governments and corporations since 1851. | Reuters Article |
We urge all organizations to remain vigilant and proactive in their cybersecurity efforts. By implementing these recommendations, you can significantly reduce your risk and protect your critical assets.
Mustang Panda Known Exploited Vulnerabilities
| CVE ID | Product | Description |
| CVE-2025-55182 | IoT / Web Apps | React2Shell: Critical flaw exploited by the RondoDox botnet (associated with Mustang Panda) to compromise IoT devices. |
| CVE-2025-14847 | MongoDB | MongoBleed: Active exploitation allowing unauthenticated attackers to coerce servers into leaking sensitive memory data. |
| CVE-2025-9491 | Windows UI | LNK Bypass: Confirmed extensive exploitation by Mustang Panda to deliver PlugX via malicious shortcut files |
| CVE-2025-41244 | VMware Tools | Exploited alongside Windows flaws for privilege escalation and persistence. |
| CVE-2024-21893 | Ivanti Connect Secure | Authentication bypass used to deploy MetaRAT (PlugX variant) targeting shipping companies in Japan. |
| CVE-2024-0012 | Palo Alto PAN-OS | Exploited for authentication bypass, often leading to ransomware-like behavior or espionage. |
| CVE-2025-10585 | Google Chrome | Zero-day in the V8 engine, patched but actively exploited. |
| CVE-2023-4966 | Citrix NetScaler | Citrix Bleed: Session hijacking vulnerability used to bypass authentication. |
| CVE-2025-6202 | DRAM (Hardware) | Rowhammer Variant: Advanced hardware-level attack bypassing DDR5 protections. |