Posted
The recent Log4J vulnerability (CVE-2021-44228) issue has set the cybersecurity world ablaze. Security teams are working overtime to quickly patch vulnerabilities and better understand how this issue affects their organization. We’d like to show how you can use the ThreatConnect Intel Driven Operations Platform (SOAR+TIP) to research a vulnerability, pull in relevant data, and produce a report to share with stakeholders. Ultimately, this will save your team time and resources, so they can get back to enjoying their holidays (move aside Grinch4J, ThreatConnect is here to save Christmas).
In short, Log4Shell is a zero-day vulnerability within the logging functionality, used by a large portion of the internet, that arises from the logger trusting and executing user-provided data. Attackers are able to exploit this by sending a specially crafted string to a vulnerable server that will be executed when logged.
Now, let’s see how ThreatConnect can be used to quickly investigate this CVE and produce a production bulletin report for your stakeholders. (Note: We are using a set of enrichment playbooks to provide all of this context upon the creation of a Vulnerability object in ThreatConnect.)
Step 1 – Creation Screen
First, we need to create the group object within ThreatConnect and apply the name of the CVE as the tag. Recall that in ThreatConnect 6.3, we introduced new Group Objects and the one our users were most excited about was Vulnerability Objects.
Once the correct CVE is typed in, we click save to create the vulnerability object within the platform.
This will take us to the object for the CVE which has already started to perform the magic in the backend.
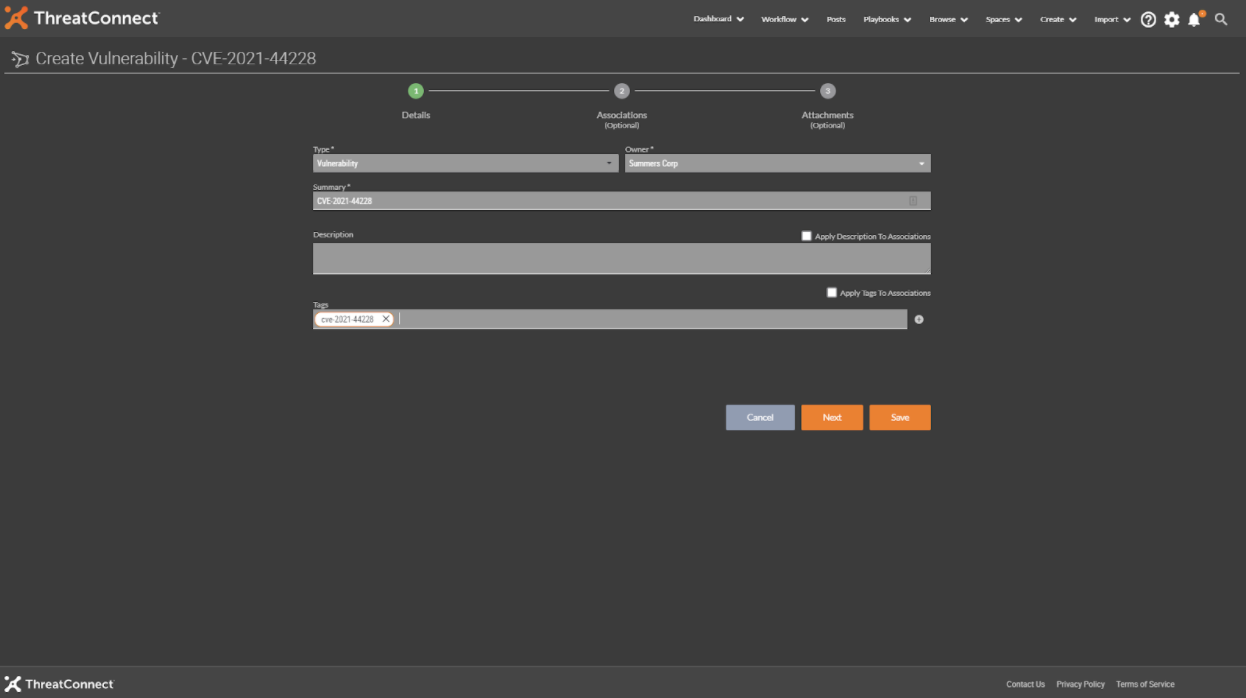
Step 2 – CVE Details Screen
As the data is pulled from the National Vulnerability Database, we can quickly review the details about the CVE.
Here you can see the details, the CVSS score and its criticality, and the Severity and Metrics matrix. This matrix helps analysts understand the overall severity and impact a vulnerability may have on an organization.
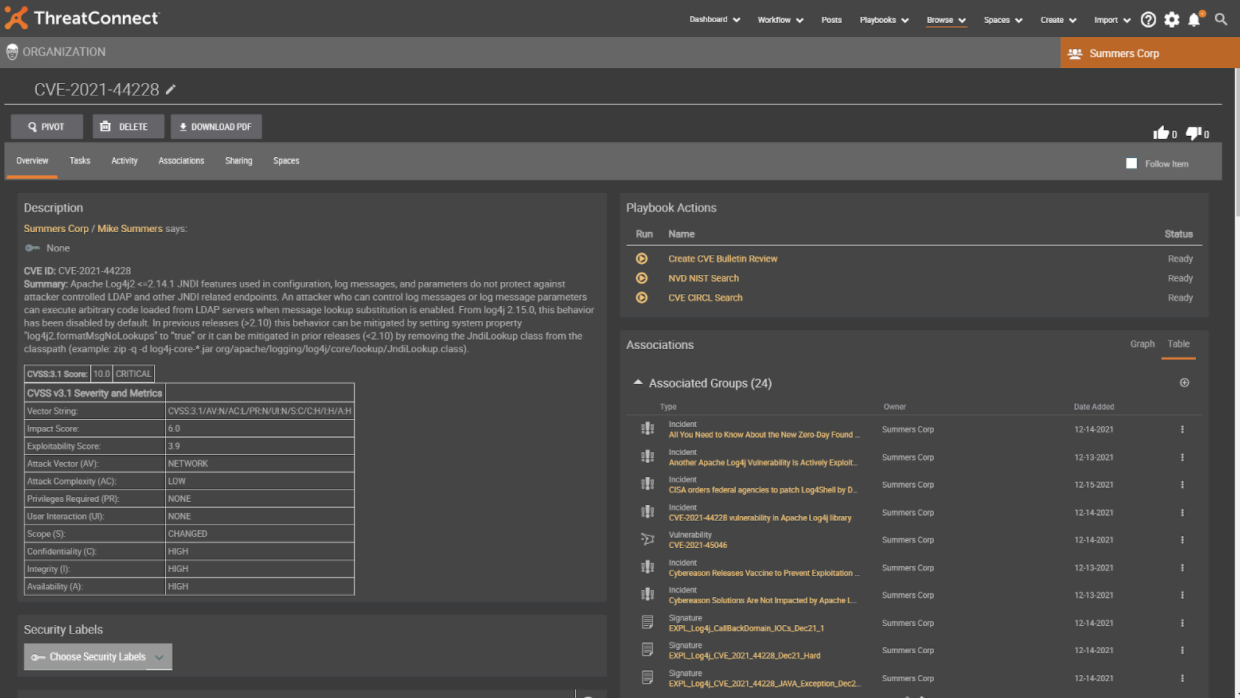
References area
We are also pulling in any references that have been associated with the CVE from the National Vulnerability Database. Here we can highlight and copy links to bring them up for additional research.
Associated Groups
As we scroll back up, we can see a section for Associated Groups – this includes any technical blogs and reports we’re bringing into the platform for quicker access and review for your analyst. We save them the hassle of going to multiple websites to find the information they are looking for without leaving the platform and they can bring up an article by clicking directly on it. A quick review of the tags and source can identify where the article came from.
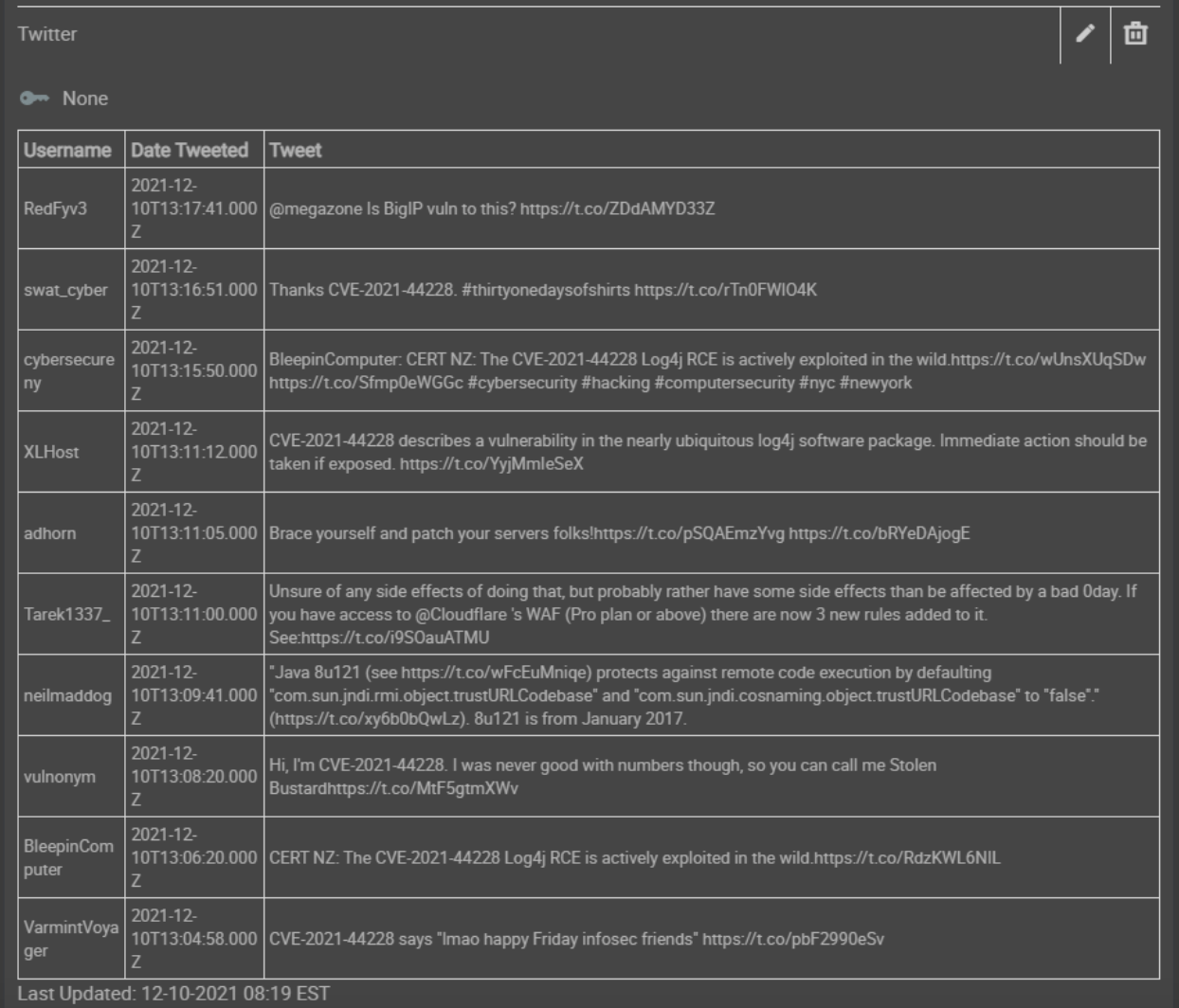
Twitter Integration
And my personal favorite for those in the know, this is where all of the news breaks for vulnerabilities – Twitter. Our newly built Twitter integration searches for the CVE over the past 7 days and brings in the most recent tweets, removing retweets and setting the language to your desired preference. This is all done in a matter of seconds and brought back into the platform to be displayed for quick view.
Having these integrations, save our analysts time and allows them to focus on what matters most and not waste valuable cycles on collecting this intel manually.
Step 3 – CVE Bulletin Review
Default PDF Document
Now that we have all of this intel, what are we going to do with it?
The ThreatConnect platform provides a quick and easy way to generate reports that can be forwarded to your stakeholders. By clicking on the Download PDF button, it will generate a report that contains all the information that’s been collected and provide any associated articles. Reports can be customized to include your organization’s logo and formatted to your liking.
Case Management CVE Bulletin Review
After reviewing all of the intelligence gathered and making a decision to inform the appropriate stakeholders, we can manually kick off a playbook to create a CVE Bulletin Review. This utilizes our built-in case management feature and allows for a repeatable process to be created through our workflow templates.
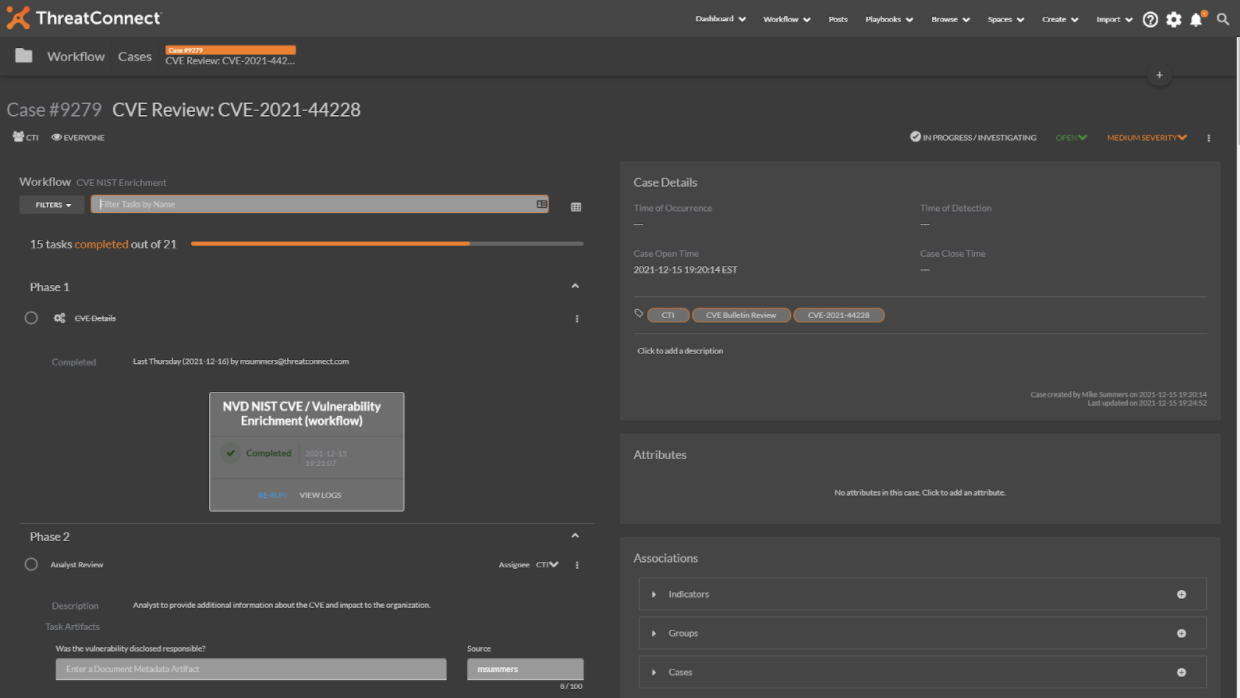
When the Bulletin is created, your analysts can assess the CVE as it impacts your organization – take into account your defense-in-depth measures for that wholistic threat assessment view, and answer the priority-driven questions from your stakeholders.
And finally, we can add steps that can generate a report and notify your Vulnerability Management team that action is required, bringing full circle the Intelligence Driven Operations that organizations are looking to accomplish.
We are excited to share this use case with our customers and hope that it serves to save some time and headaches. Please reach out to us at sales@threatconnect.com if you have any questions or want to learn more about ThreatConnect Intel Driven Operations Platform.
Watch a deeper explanation of this Use Case here!
Written By: Mike Summers, Sales Engineer at ThreatConnect

