Posted
Binary file hashes are a common indicator used in information security. Unfortunately, files hashes are hard to read, let alone memorize. Here are some examples of what file hashes look like:
18f8e43b6de2dcf7c8e96af329ded882 0cc61d25f0e009e730e3a95d778325ed16ef26da 88237ec59eefc109f564e055216d8b7c6a4afd88ced7e3ef81a5801b083cecd2
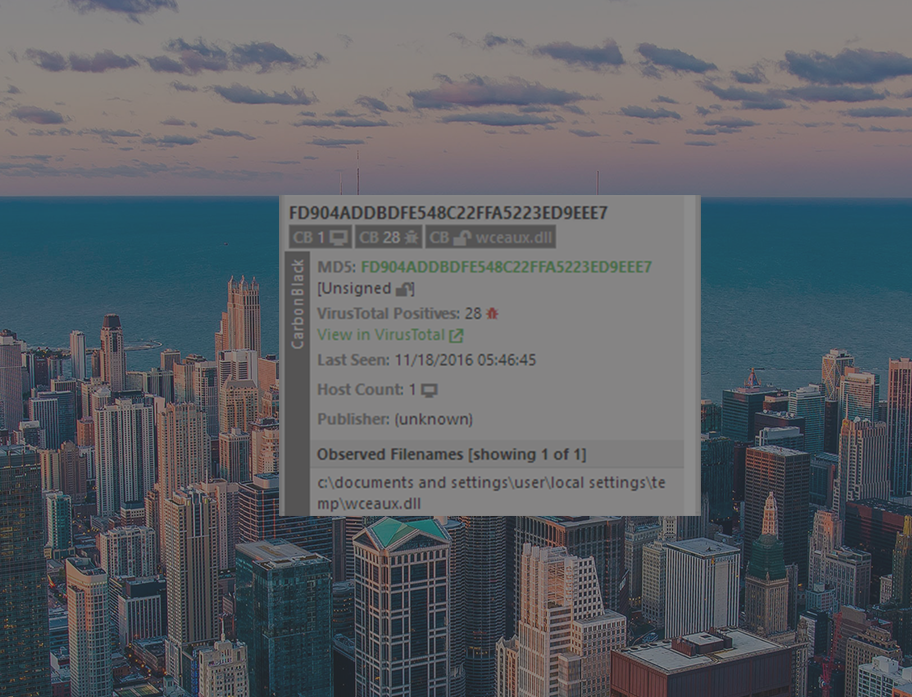
I challenge you to memorize one of these, let alone the thousands that run in your environment every day. An information security vendor, Carbon Black, helps organizations keep a record every time a binary runs in their environment. When Polarity is connected to Carbon Black, Polarity will:
- Recognize any time there is a file hash on your computer screen
- Check your Carbon Black instance to see if it has run in your environment
- If there is a hit, overlay useful information from Carbon Black
Polarity can overlay information such as the number of hosts the binary has run on, reputation data, or links to additional details.