Posted
More and more organizations, both large and small, are beginning to realize the benefits of creating a cyber threat intelligence (CTI) program. In fact, 85 percent of the organizations surveyed in the 2021 SANS Cyber Threat Intelligence Survey said they produce or consume CTI — a 7 percent increase over last year.
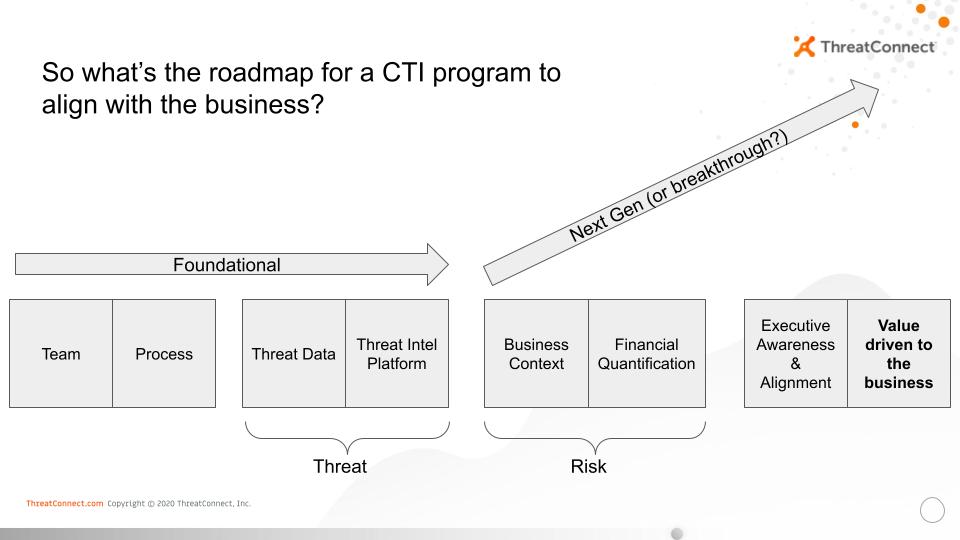
But a modern and effective CTI program isn’t only about establishing a dedicated CTI team, documenting intelligence requirements, and analyzing information about the capabilities and intent of your cyber adversaries. To the contrary, modern and effective CTI programs bridge the gap between the security team and the business leadership.
The Modern Cyber Threat Intelligence Program
According to the SANS survey, more organizations are beginning to measure the effectiveness of their CTI programs. And while that’s a positive sign, there remain significant questions about whether or not organizations are measuring the right things.
The vast majority of respondents to the SANS survey are measuring the effectiveness of their CTI program based on the number of threats and attacks detected (78%), the ability to block threats (70%), and conduct incident response (66%).
However, the difference between a good CTI program and a great CTI program is in its ability to communicate value to the business in terms of risk. This is a realization that many have come to within the threat intelligence community and a core reason why the discussion around cyber risk quantification is heating up in these circles. Currently, there are few CTI programs that have fully realized this vision and for most this is an aspirational goal, but it is one that is not far out of reach as cyber risk quantification becomes more mainstream. It factors heavily into ThreatConnect’s decision to acquire one of the pioneers in cyber risk quantification in late 2020.
By adding context and enriching our understanding of threats and vulnerabilities, a great CTI program helps inform an organization’s risk quantification platform and aligns the entire business to the threats that matter most based on primary and secondary loss magnitude. Threat data also feeds your security orchestration, automation and response (SOAR) platform — all of which should be accessible through a single dashboard.
A modern CTI program will provide executives a prioritized view of the following:
- Financial risk
- Tactical threat
- Actions to take
It fuses risk, threat and response to create a complete decision and operational support system for cyber security. It’s the brains of your operation. By combining cyber risk quantification, threat intelligence, and security orchestration and automation, the security team can provide a single source of truth from the SOC to the C-Suite.
Cyber Risk Quantification (CRQ) gives strategic leaders the ability to identify, measure and manage the financial or operational impact of cyber threats, solving the issue of prioritization once and for all. With this NorthStar understanding of where to focus, the entire organization is on the same page when it comes to where to focus people, process and technology.
A Threat Intelligence Platform (TIP) will support this analysis and deliver deep insight and context to help identify, analyze and take action against the threats that matter most to your business enterprise.
Integrated SOAR capabilities with streamlined workflows and automated playbooks ensure security teams are able to make better, more informed decisions that enable faster SOC mitigations and incident response.
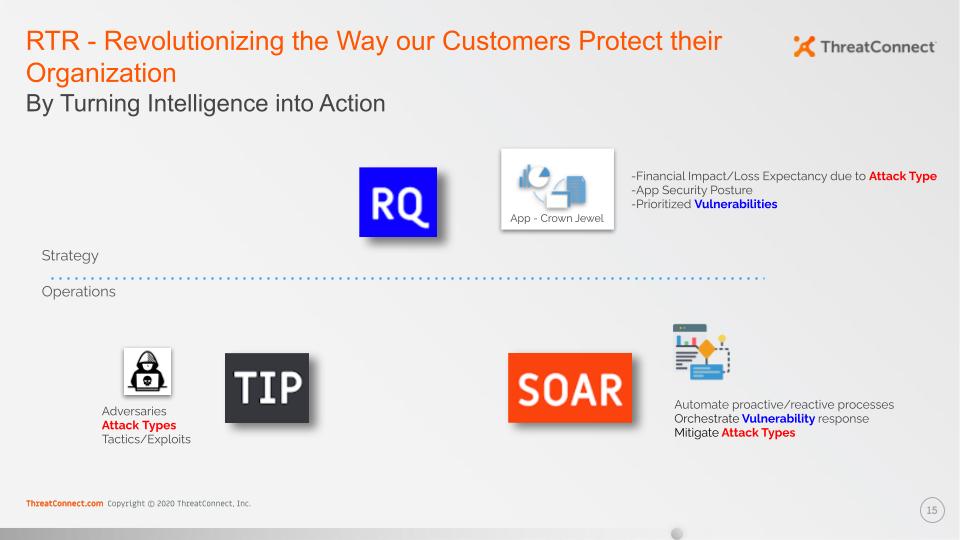
Today’s modern CTI program should be the command center for your cyber operations, maximizing the impact of your existing technologies and connecting the dots between business impact and cyber security. By integrating the strategic, analytical and operational functions of cyber security, a modern CTI program reduces complexity, improves efficiency and aligns security to the objectives of the business.
Remember, a modern CTI program should speak the language of your business, not solely of adversary tactics, techniques, and procedures. The best CTI will turn intelligence into actions that align with business objectives and protect operations, revenue, and reputation.
