Posted
Threat intelligence activities, especially enrichment, analysis, and action, have traditionally required a lot of manual work. Threat Intel Operations analysts are not expected to be coders, spending their time in Python to automate their activities, and it’s not usually a “one and done” activity. Changing APIs and process improvements that require scripts to be updated regularly takes time away from TI Ops analysts doing what they want to be doing – operational, tactical, and strategic threat intel activities.
Drop ‘n Drag is Better
Drop ‘n drag tools are easier to use and much faster than manual coding when building out automation. Drop ‘n drag coding is more visual, easily understandable, and user-friendly. This saves valuable time and improves the availability of Playbooks, both new and updated.
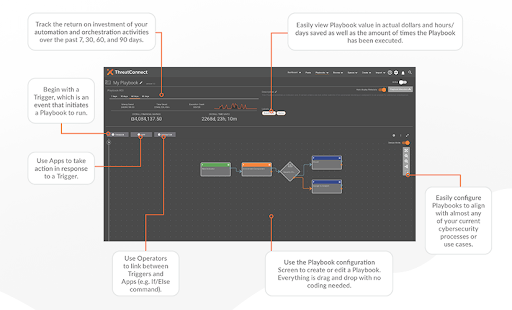
Empower Your TI Ops Analysts
TI Ops and other security operations analysts can leverage ThreatConnect’s low-code automation capability to address threats that can potentially impact your enterprise proactively and rapidly. Full automation is the key to rapid threat intelligence processing and dissemination to power threat response and mitigation.
Cybersecurity Ecosystem Integration is Everything
Playbooks can automate the dissemination of threat intelligence to any of ThreatConnect’s hundreds of integration partners. Low Code Playbook Automation can also handle data from any cybersecurity control or tool, such as firewalls, etc., including those not yet integrated with the ThreatConnect Platform.
Let the ThreatConnect Platform Work for You
The ThreatConnect Platform uniquely leverages risk insights and automation to help focus limited organizational resources on the organization’s top priorities. The ThreatConnect Platform will help move your TI Ops team from reactive to proactive engagement. Your team will more effectively use threat intelligence and knowledge to drive better decisions and more effective action. This allows security teams to more rapidly leverage actionable threat intelligence to close the loop between threat actor activity and defensive cyber measures. This new knowledge enables your team to detect, prevent, and mitigate malicious ongoing threats.
As an example, consider that a new and dangerous cyber threat has been identified targeting banks and financial institutions within the United States. Your threat intelligence sources and review of industry websites indicate that your organization may be facing this threat shortly. Using your IOC data, you have crafted a response plan along with the threat detection and response team to automate a response to this threat to minimize the risk of a successful attack. It will take about three days to program and test the new Playbook. But that may be too long. Another bank in your state was just successfully hit by the threat. The solution? Using ThreatConnect’s low-code automation to quickly and easily construct a playbook. Using the drop ‘n drag playbook builder capability, you can construct the process for the Playbook in minutes.30 minutes., test it, and deploy it the same afternoon.
Learn More
ThreatConnect’s Low Code Playbook Automation can give you the flexibility, consistency, and rapid speed implementation that your team needs.
To learn more about how ThreatConnect can help your organization maximize insight, increase efficiency, and improve overall collaboration, please look at the ThreatConnect Platform. Reach out to us via https://threatconnect.com/contact/, and we’ll be pleased to share a customized demonstration of the ThreatConnect Platform.

