Posted
 This was one of the first graphics we created for the ThreatConnect Platform, but it’s one that’s still very meaningful to our latest release. It may seem quaint, and the graphics have certainly improved over the years, but the vision remains the same: threat intelligence can guide security operations towards better decisions, and security operations serves as the source of some of your best (native) threat intelligence. And that brings us to ThreatConnect 6.1: The Tao of Intel-Driven Operations.
This was one of the first graphics we created for the ThreatConnect Platform, but it’s one that’s still very meaningful to our latest release. It may seem quaint, and the graphics have certainly improved over the years, but the vision remains the same: threat intelligence can guide security operations towards better decisions, and security operations serves as the source of some of your best (native) threat intelligence. And that brings us to ThreatConnect 6.1: The Tao of Intel-Driven Operations.
If our launch of Workflow in 2020 was a big step towards realizing that vision, then ThreatConnect 6.1 takes it to the next level.
As stated by Gartner in their document titled How to Use Threat Intelligence for Security Monitoring and Incident Response, there’s a challenge on our hands when it comes to the utilization of threat intelligence.
“Modern security tools can ingest and leverage threat intelligence. However, they often don’t include guidance on the best way to utilize it.”
This highlights the stark differences observed between simply ingesting threat intelligence into a security tool and comparing that to a solution that is smart enough to present that information to an analyst in a way that they can use it to make informed decisions that help during analysis, investigation, and response. This is something that we at ThreatConnect have been laser focused on for years and, in ThreatConnect 6.1, we’re giving threat intel analysts a direct window into ground-truth operational data, and we’re giving SOC analysts a single-page view of relevant, contextualized intelligence, all the way to the adversary level.
You’ll also see some new capabilities that help analysts on any team make more effective, better-informed decisions with information that’s presented to them directly from where they’re completing analysis or investigation.
The benefits of these types of capabilities don’t stop at the analyst level. They’re felt across the entirety of the business. To help better understand how these seemingly analyst-level capabilities can introduce business-level benefits, we’ve invited our fictional CISO, Sriya, to help tell the story.
Meet Sriya! Sriya’s a CISO at a publicly-traded Fortune 500 company. Her job is to minimize risk to the business, maximize the effectiveness of the security organization, and provide value to her company’s shareholders. She’ll be calling out specific areas in ThreatConnect 6.1 that can help her get that job done, and will be making appearances in future blogs wherever we need to demonstrate ThreatConnect’s strategic capabilities!
ThreatConnect 6.1 demonstrates the importance of having a single platform, which truly intertwines the capabilities of a TIP and a SOAR. TIP + SOAR = One Big Beautiful Web of Information
There are quite a few exciting improvements and updates in 6.1, but here we’ll focus on three:
- Linking Cases and Intelligence
- Report Cards Everywhere
- Actionable Artifact Context
Let’s dive in!
Linking Cases and Intelligence
To better understand the impact Linking Cases and Intelligence will have on our users, let’s step into their shoes:
“As an analyst, I want to be able to understand if there is a previous or open investigation related to a piece of threat intelligence. This provides insight into previous work done across the rest of the security team that may relate to what I’m currently looking at. I don’t have a good way of understanding potential associations between threat intelligence and cases making it difficult for me to get more predictive during investigation and analysis.”
If you think about a typical threat analysis use case, when looking at a specific adversary, you likely want to see all Cases that your team has investigated related to that adversary to understand if it’s something that has been seen before within your organization. ThreatConnect 6.1 not only makes this a possibility – it does so innately from the same page you’re doing the initial adversary analysis on which saves time and frustration that’s oftentimes introduced when clicking around multiple interfaces.
Sriya the CISO says…
From a CISO’s perspective, this approach confers several benefits. By allowing multiple teams to work together in one platform, you reduce overall cost of ownership, as well as encouraging more effective team collaboration and silo-reduction. Because cross-team insights are presented directly in the software (rather than through complex integrations and procedures), you reduce team overhead, allowing the team to focus on critical defense rather than logistics. Finally, by giving teams the opportunity to learn and evolve their defenses from each other’s data, you end up maximizing investment in the teams, the software, and any data or intel feeds or subscriptions.
Now, users are able to understand relationships across Cases and Intelligence in ThreatConnect through Defined & Potential Associations.
Defined Associations are exactly as they sound: associations that are manually defined by the user (or automatically via a Playbook, integration, or API). Users can now directly link Cases and Artifacts to Indicators and Groups. For example, when investigating an case involving a particular Malware Family, the Case can be linked directly to the Threat or Adversary involved.
Potential Associations happen when ThreatConnect suggests an association may exist without involvement from the user. ThreatConnect says that ‘we think this adversary is related to this case because this adversary is related to bad.com and bad.com also appears on this case’. This is now able to happen across indicators, groups, and cases – a big, beautiful web.
If the information presented to you warrants further investigation, easily open up a Case immediately from the Indicator Details page you’re working from. Easy as pie!
Report Cards Everywhere
“As an analyst, I want to be able to better gauge the trustworthiness of a particular piece of threat intelligence. This requires the ability to determine which of my feeds are providing high quality intelligence so that I can focus my time and effort on the most accurate sources of relevant intel.”
Getting immediate access to the information needed to make better strategic and tactical decisions is critical during any sort of analysis or investigative process.
With a news article, understanding the validity and bias of the source is just as critical as the content of the article itself. Intelligence is the same way: when viewing an indicator, you might ask of the feed reporting it:
- How often does this feed report a false positive?
- How timely is this feed compared to other feeds?
- Does this feed provide a wide breadth of information (e.g. is it only interested in phishing domains, or does it cover other topics)?
- Do indicators in this feed tend to be more critical / malicious then others?
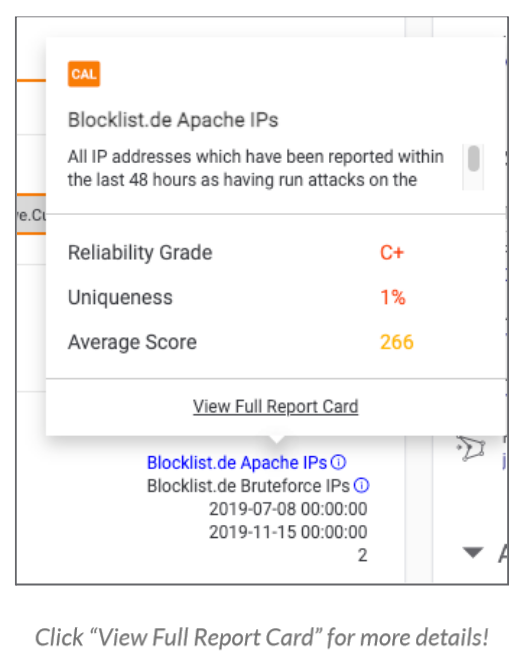
With Report Cards Everywhere, evaluate the efficiency and accuracy of OSINT and ThreatConnect-generated threat intelligence feeds and use that as a data point when determining how to move forward with a specific piece of intelligence during your analysis or investigative processes.
All users now have access to Feed Explorer, a part of ThreatConnect that shows you information like reliability and uniqueness of particular intelligence feeds.
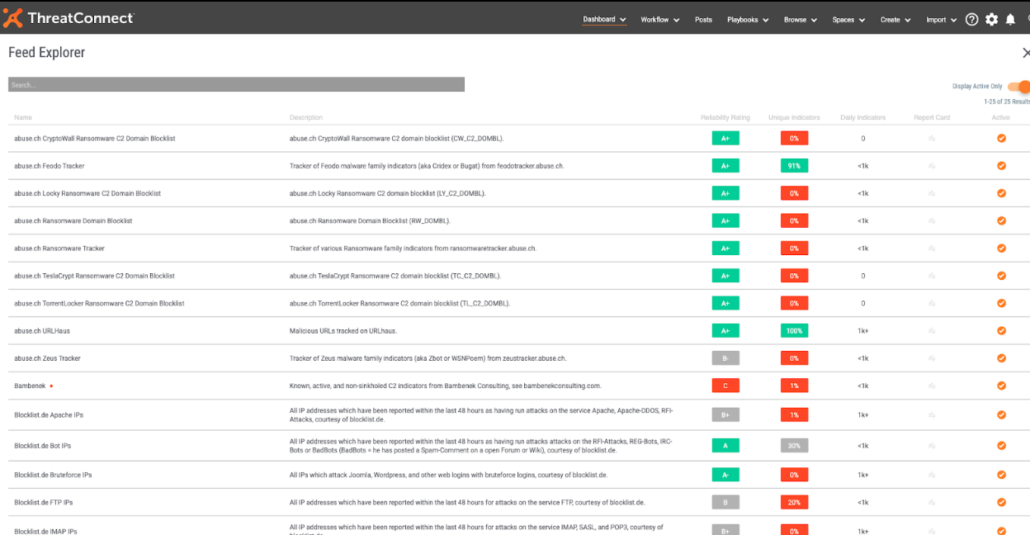
Additionally, users will now see a prompt in the form of a green dot if ThreatConnect is recommending, “Hey, this feed is pretty good, you might want to turn it on.” The opposite can also happen, a red dot indicating, “Hey, not so sure about the quality of this particular feed. You may want to reconsider having it active.”
The information provided from Feed Explorer is great, but with ThreatConnect 6.1, it’s being provided to users almost everywhere within ThreatConnect – hence Report Cards Everywhere.
With Report Cards Everywhere, Analysts have another datapoint to provide them with additional moment-in-time context about the specific piece of intelligence they’re looking at right from the interface they’re working from. The information from Feed Explorer is presented to them directly from the Indicator Details page, saving time from switching between screens and will ultimately lead to a more informed and efficient security team.
Sriya the CISO says…
Some of my team’s most important skills are soft skills like critical thinking and bias checking. Report Cards Everywhere not only gives my teams valuable context to help us maximize our data collection efforts, it’s also a built in tool to help the team leverage and develop those soft skills, increasing overall team experience and expertise. It also helps reduce the risk that analysts will waste time chasing false positives and helps them focus on the most critical threats to our business.
Actionable Artifact Context
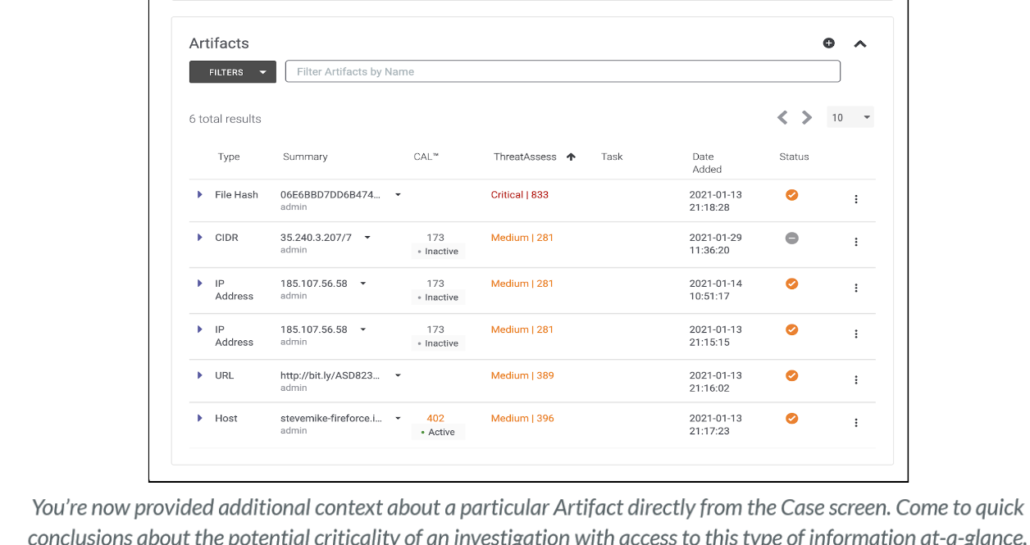
“As an analyst, when I’m looking at an Artifact, I need to understand additional context around it – just knowing it exists and it’s related isn’t enough. I may have hundreds of Artifacts on a Case. When I open a Case, I want to quickly be able to determine how critical my case is (and if it’s likely associated with a false positive) by utilizing information provided to me by ThreatConnect directly from the Artifacts List.”
In ThreatConnect 6.1, we have significantly expanded the amount of context provided to an analyst when viewing Case Artifacts. Now, when a SOC Analyst is investigating a Case, they’re armed with the threat intelligence they need to make more informed decisions without leaving the page.
Users can now see which Task added the Artifact, CAL details, derived indicators, and much more. Additionally, the Artifact list on a Case can now be sorted by ThreatAssess, allowing the most critical items to bubble up to the top of the list.
Pulling it All Together
ThreatConnect is changing the way security works. We’re invested in not only giving you the information you need to make better decisions, but providing it to you in a way that saves you time, saves you frustrating, improves collaboration across your team and technologies, and ultimately drives down risk.
Like we said in the beginning:
TIP + SOAR = One Big, Beautiful Web of Information
A big thank you to Sriya, our fictional CISO, for helping guide us through the business-level benefits provided through this release!
If you’re a current customer and have questions about 6.1, please reach out to your dedicated Customer Success team member.
Not yet a customer but curious how we can partner with your organization? Reach out to sales@threatconnect.com
