Posted
I’ve got 99 problems, but keeping up with the news isn’t one
Collecting is the sort of thing that creeps up on you. ~Paul Mellon
“Did you see that latest report on [ransomware, ShadowBrokers, insert topic du jour here]?” Keeping up with the latest research in the field is a key task for any infosec analyst, and it’s daunting. There’s so much coming out from different researchers and yes, vendors, that you could spend your entire work week doing nothing but reading other people’s analysis.
In the past, the ThreatConnect Research Team has devised clever ways to navigate the mountain of quality public threat intelligence reports – including RSS feeds, a Slack channel, Twitter, a roulette wheel – but felt like we could do better. We really wanted:
- An automated way for ThreatConnect to ingest all of those technical blogs we like to follow in a format that’s easy to read (hello markdown!)
- Properly parsed and associated indicators so those publications become part of our overall knowledge base and fodder for our sweet analytical enrichment techniques
- Fewer clicks and open tabs
- A foosball table in the office (this request was denied by management)
Keeping with our ethos of being “for analysts, by analysts”, we built a system that does just that and started ingesting 55 blogs. And it was good. After we showcased our handiwork and its obvious utility to an analyst, leadership agreed to the foosball table let us share it with all of you.
So grab your coffee (or Red Bull – we won’t judge) and start your day in ThreatConnect by checking out what’s new. Behold: the Technical Blogs and Reports Source!
What is the Technical Blogs and Reports Source?
The Technical Blogs and Reports source is a source that is open to all ThreatConnect users with access to the ThreatConnect Multi-tenant Cloud. As we mentioned, it is populated with the blog posts from 55 blogs (and counting) which have been chosen for their quality by us (the ThreatConnect Research Team).
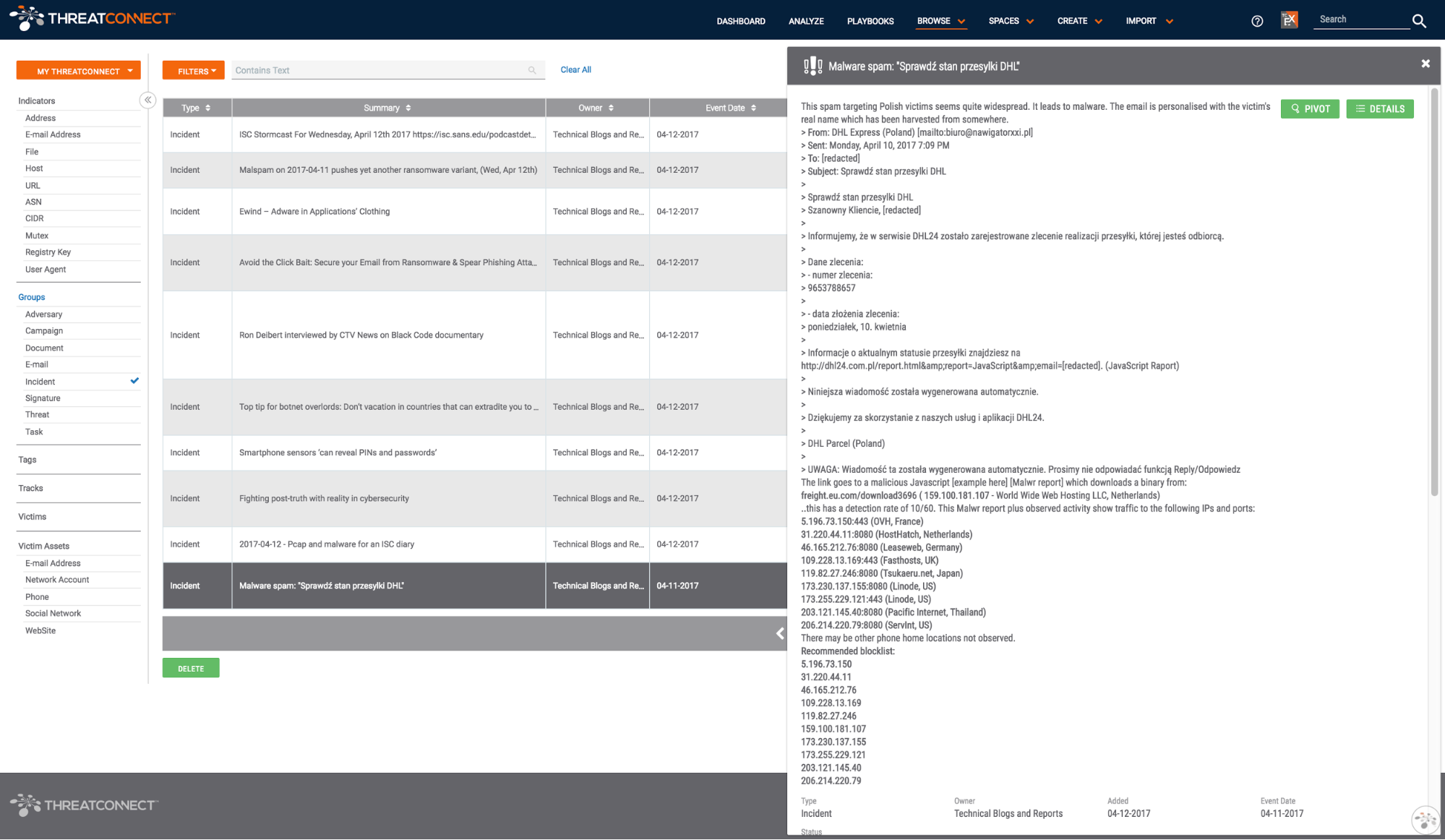
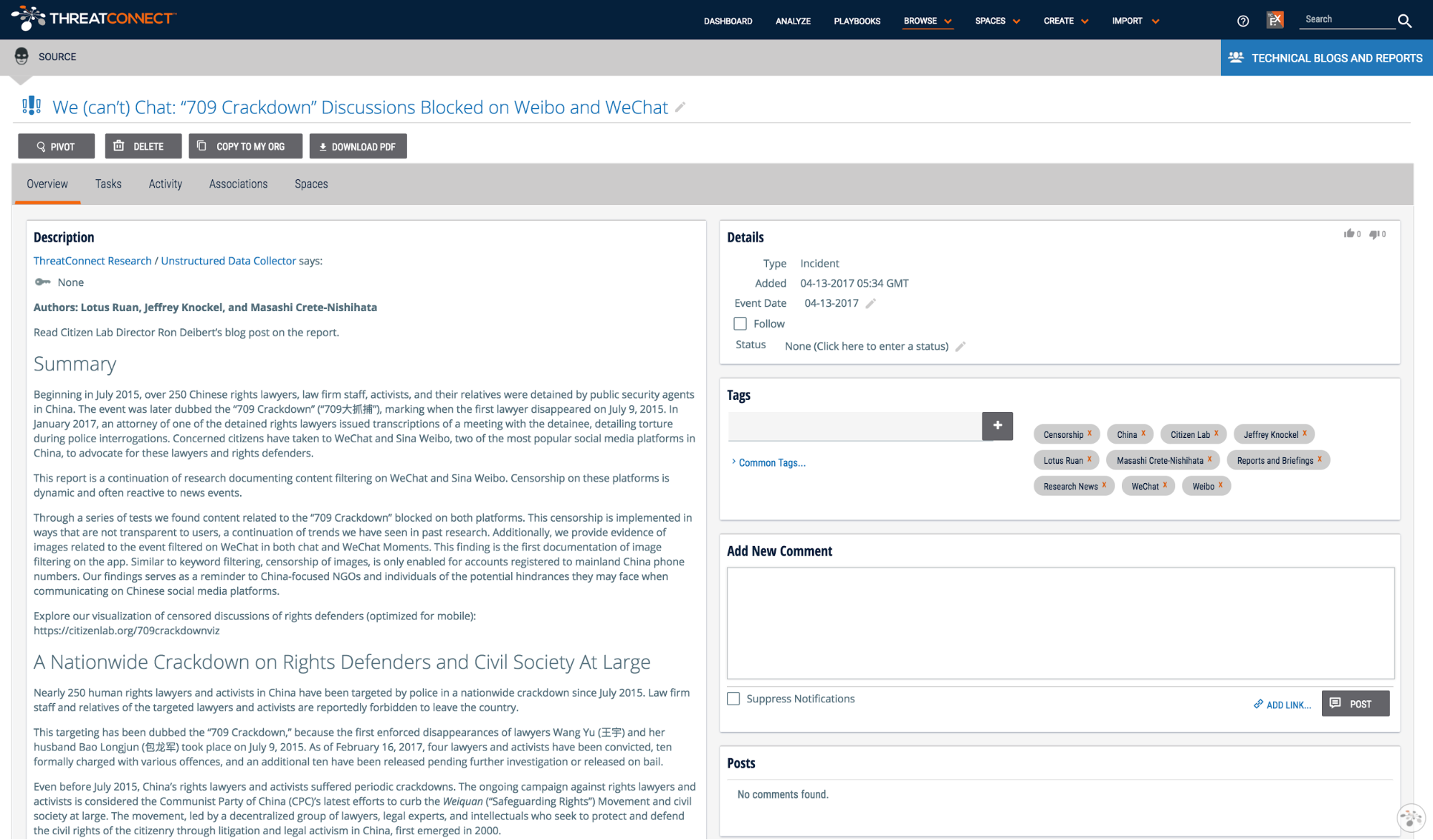
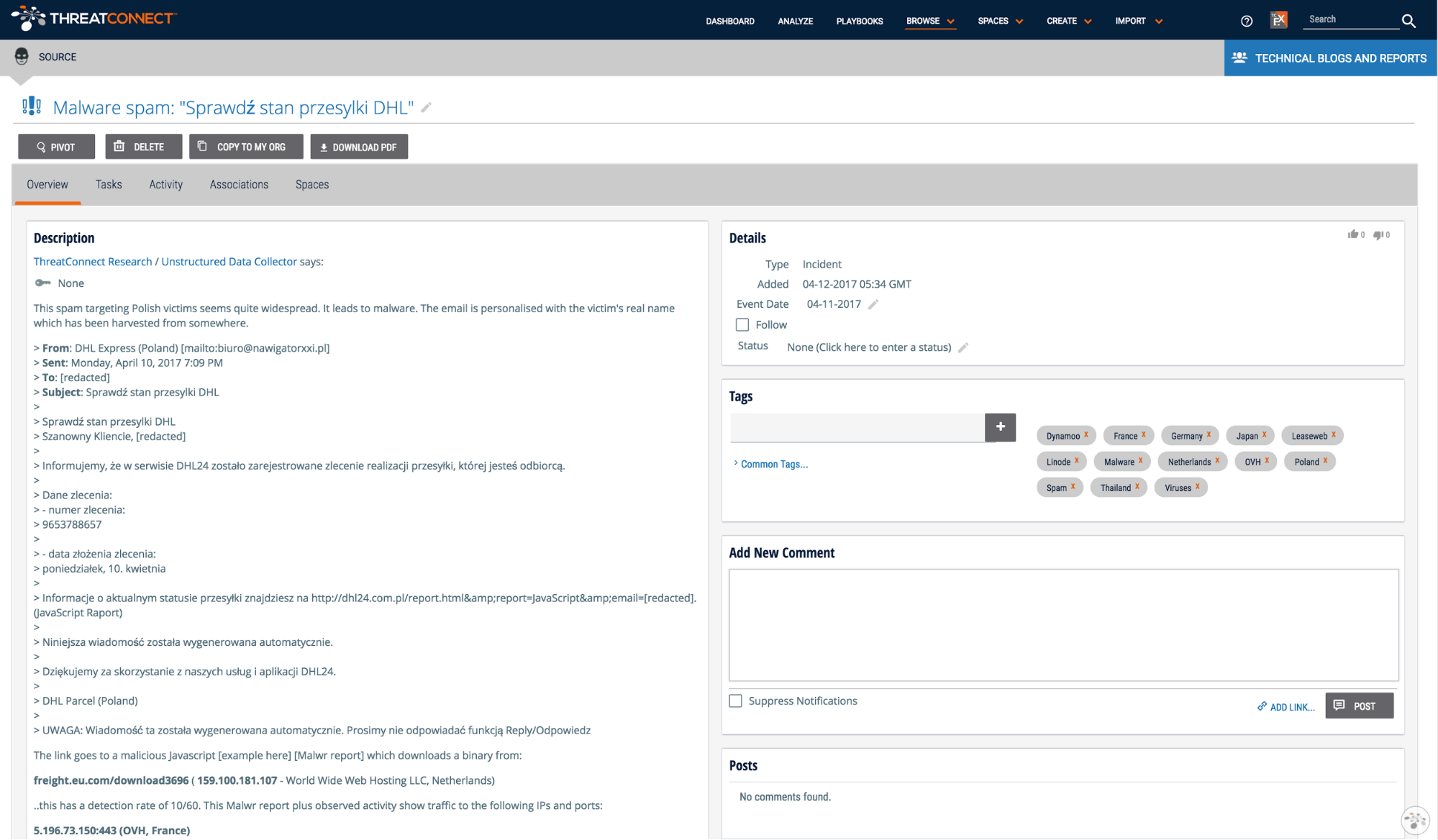
Each new post is represented by an incident in the Technical Blogs and Reports source. The content of the blog post is converted to markdown and added as the incident’s description.
All of the indicators provided in the post are parsed out and associated with the incident saving you the work of finding the indicators. To explore this content in ThreatConnect, jump to the “How do I use it?” section at the end of this post.
Why Should I Care?
The Technical Blogs and Reports source allows incident responders, researchers, and analysts to stand on the shoulders of giants by having access to the work produced by other researchers and malware analysts. Whether you are an independent researcher or work for a Fortune 10 company, this source lets you be more effective and fight at a higher weight-class by bringing content from many, disparate locations into one place and ‘translating’ that content into a common data-model. You may not be an expert on the newest forms of Ransomware, but with the Technical Blogs and Reports source, it is easy to find pertinent information that can bring you up to speed.
In addition to having quality research curated in one place, the Technical Blogs and Reports source also provides more context and intelligence about specific indicators that you may run across in the course of an investigation or research effort. In ThreatConnect, if an indicator in one owner (a community, organization, or source) also exists in another owner to which you have access, an “Additional Owners” card like the one below will show you other places where the same indicator exists (you can see this in action here).
Say you are investigating a file that calls back to usawaterproofing[.]com. Creating usawaterproofing[.]com as a host indicator within your organization in ThreatConnect will show you that the same indicator exists in the Technical Blogs and Reports source which provides you some immediate context surrounding this indicator. The same principle applies when using the Analyze feature to find what ThreatConnect knows about given indicators. With an influx of new information coming into the Technical Blogs and Reports source, it is easier to find helpful context around indicators in ThreatConnect.
How Do I Use It?
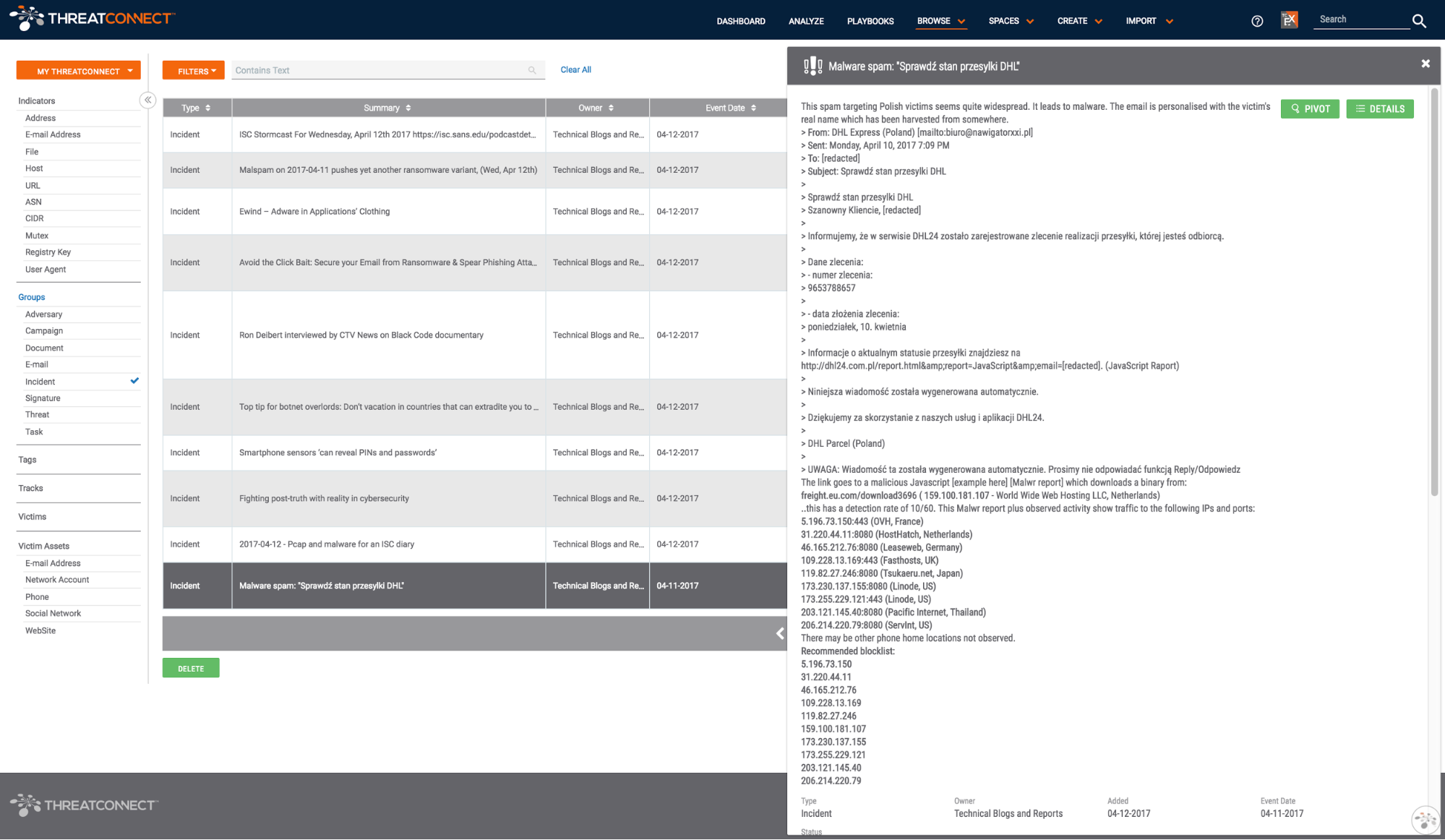
The easiest way to find the most recent blog posts in the Technical Blogs and Reports source is to view all incidents in the source. In fact, with the updated browse screen released in ThreatConnect version 4.4, you can bookmark: https://app.threatconnect.com/auth/browse/index.xhtml?filters=typeName%20in%20(%22Incident%22)&intelType=groups&owners=10666 which will take you right to the list of the most recent incidents.
Technical Blogs and Reports Source Incident List
If you are interested in a particular subject (be it a malware family, APT group, TTP (Tactic, Technique, and Procedure), etc.), you can find related content by searching through the tags in the Technical Blogs and Reports source.
Lastly, you can simply search for a topic in ThreatConnect using the search feature in the upper right-hand corner. Oftentimes, this will turn up some blog posts in the Technical Blogs and Reports source which are related to the given topic.
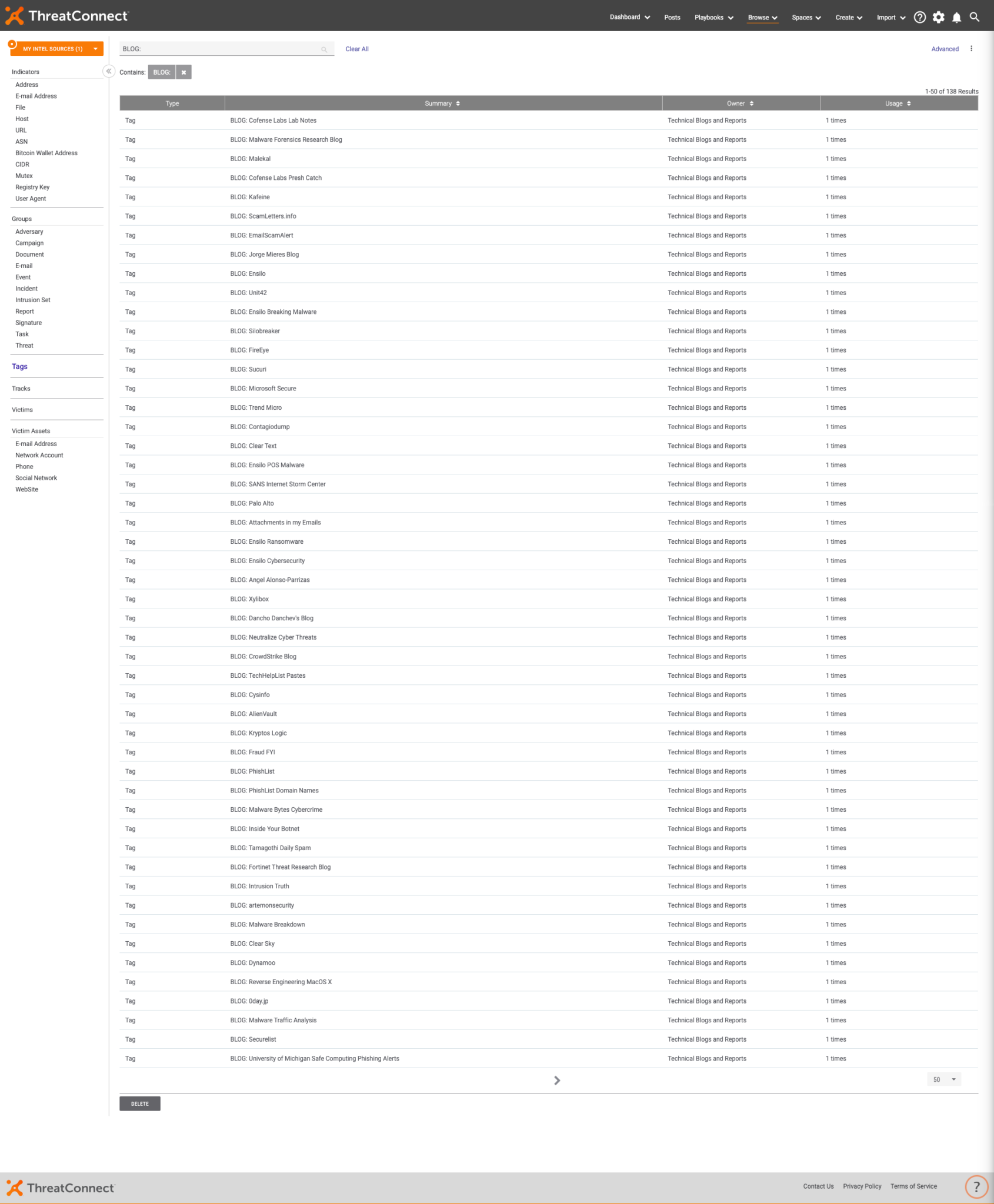
What Blogs are Being Pulled into the Source?
Below is a list of all of the sources from which content for this source is gathered. A few of the sources listed below have multiple blogs which we are pulling in. This list is subject to change as quality blogs come and go.
- Cofense Labs Lab Notes
- Malware Forensics Research Blog
- Malekal
- Cofense Labs Presh Catch
- Kafeine
- ScamLetters.info
- EmailScamAlert
- Jorge Mieres Blog
- Ensilo
- Unit42
- Ensilo
- Breaking Malware
- Silobreaker
- FireEye
- Sucuri
- Microsoft Secure
- Trend Micro
- Contagiodump
- Clear Text
- Ensilo POS Malware
- SANS Internet Storm Center
- Palo Alto
- Attachments in my Emails
- Ensilo Ransomware
- Ensilo Cybersecurity
- Angel Alonso-Parrizas
- Xylibox
- Dancho Danchev’s Blog
- Neutralize Cyber Threats
- CrowdStrike Blog
- TechHelpList Pastes
- Cysinfo
- AlienVault
- Kryptos Logic
- Fraud FYI
- PhishList
- PhishList Domain Names
- Malware Bytes Cybercrime
- Inside Your Botnet
- Tamagothi Daily Spam
- Fortinet Threat Research Blog
- Intrusion Truth
- artemonsecurity
- Malware Breakdown
- Clear Sky
- Dynamoo
- Reverse Engineering MacOS X
- 0day.jp
- Malware Traffic Analysis
- Securelist
- University of Michigan Safe Computing Phishing Alerts
- Sketchymoose
- VMRay
- Krebs on Security
- Remove Trojans
- Kleissner
- University of Chicago Latest Email Scams
- Citizen Lab
- BroadAnalysis
- Talos
- Recorded Future Analysis Blog
- Brown University Phish Bowl
- Online Threat Alerts
- THREATgeek
- Yoroi Blog
- Breaking Malware
- ESET We Live Security
- TechHelpList Spam
- Heimdal Security
- US-CERT Alerts
- BAE Systems Threat Research Blog
- Hazmalware
- Vitali Kremez
- Biebs the malware guy
- Precisionsec
- ThreatTrack
- Blaze’s Security Blog
- Bitdefender Labs
- Malwageddon
- Maltiverse Blog
- PhishList Email Scams
- Cyphort
- R3MRUM
- 360 Netlab Blog
- US-CERT Analysis Reports
- Pcap Analysis
- Security 0wnage
- Dragon Threat Labs
- The Ransomware Blog
- Beware of Email Scams
- Google Security Blog
- VirIT
- Johannes Bader’s Blog
- Brendinghat
- PhishList Phone Numbers
- VIPRE Labs Blog
- Cryptolaemus Pastedump
- ReversingLabs
- Cofense
- Cert Polska
- Zerophage Malware
- Malware Reversing
- TruShield
- Malware Tracker
- Cybereason
- Misterch0c’s Blog
- ReaQta Blog
- Objective-See
- Bad Packets Report
- DeepEnd Research
- DocuSign Alerts
- GovCERT.ch
- Malware Party
- Check Point Research
- Fox IT
- SlashNext
- Nioguard
- SlashNext Malware
- SlashNext Phishing
- Volexity
- Malware Bytes
- Contagio Mobile
- Team Cymru
- HYAS
- malware@prevenity
- Cisco Umbrella
- Zscaler
- PhishMe
- ID Ransomware
- My Online Security
- Scam Reports
- Ropchain
- Arbor Threat Intelligence
- US-CERT
- Contagio Exchange
- RiskIQ
- Proof Point
- CrySyS
- Malware Bytes Threat Analysis
Have a blog that you’d like to have pulled into the Technical Blogs and Reports Source? Tweet a link to the blog to @ThreatConnect with #TCTechblogs.
[av_hr class=’default’ height=’50’ shadow=’no-shadow’ position=’center’ custom_border=’av-border-thin’ custom_width=’50px’ custom_border_color=” custom_margin_top=’30px’ custom_margin_bottom=’30px’ icon_select=’yes’ custom_icon_color=” icon=’ue808′ av_uid=’av-1n5ylm4′]