Posted
This Friday, we introduce a Playbook Component that allows you to change the status of an Indicator. An Indicator’s status classifies the Indicator as either active or inactive. An active status indicates that the Indicator should be treated as an indicator of compromise (IOC) at the current time. An inactive status lets you keep an Indicator in ThreatConnect for historical records while also communicating that the Indicator should no longer be considered an active IOC. You can read more about Indicator status here.
Installation and Usage
You can find the Component to update Indicator status in our Github repository here. To install it in ThreatConnect, download this file and import it from the “Playbooks” page in ThreatConnect.
Once it is installed, you can turn on the Component and use it in another Playbook (there is an example Playbook using this Component here).
How it Works
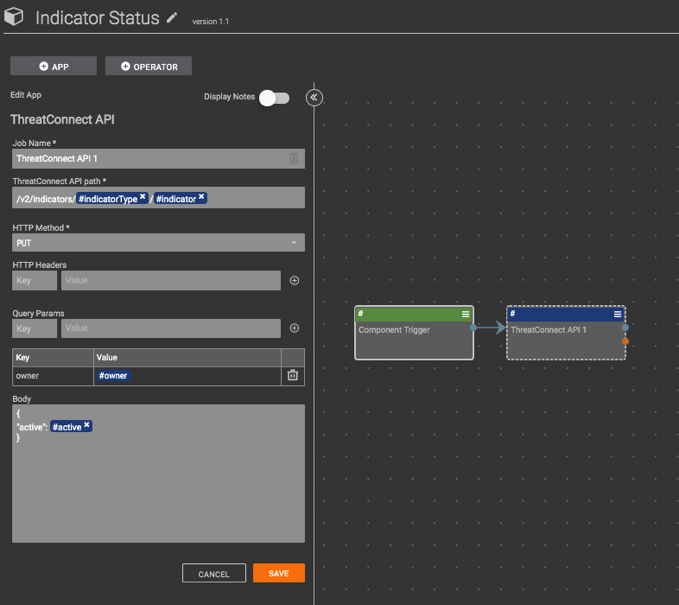
The functionality of setting an Indicator’s status has been created as a Component rather than a Playbook because of the advantages of Components described here. The component works using the “ThreatConnect API” playbook app to make an API request changing the Indicator’s status.
Thanks for reading! If you have any questions or feedback, feel free to raise an issue. Also, don’t forget to explore our repository of Playbooks, Playbook Components, and Playbook Apps.