Posted
The critical challenge for Security Operation Centers (SOC) is minimizing the window of opportunity for attackers by quickly detecting and responding to threats. The time taken to detect and mitigate the threats are tracked by two metrics: Mean Time To Detect (MTTD) and Mean Time To Respond (MTTR). The efficiency of the SOC is typically measured by these two metrics and SOCs strive to keep these metrics low by leveraging various tools and specialist teams. Security tools enabling effective collaborations between these specialist teams are often overlooked and lead to teams working in silos and interacting in a reactive manner. Two core teams in a typical SOC are SOC Analysts and Cyber Threat Intel (CTI). This blog identifies three important improvements to break the silos between these teams and run a more efficient SOC:
- Make different SOC teams share information organically and proactively in real-time
- Visualize the relationship between Cases to get the full context and reuse prior knowledge
- Allow bulk actions on Cases to expedite resolution and avoid mundane, repetitive work.
SOC Structure
A SOC analysts team is generally organized into multiple tiers and the number of tiers varies depending on the organization’s size. Tier 1 analysts are the frontline team that monitors alerts and creates cases for real threats, which will be further investigated by the other SOC tiers. Apart from Alert triage and prioritization, SOC teams are also responsible for remediation and recovery. The main challenge for SOC Analysts teams has always been dealing with the increased complexity of investigations, false positives, and lack of context behind threats. To get a better context for the investigation, the SOC Analysts team relies on the Cyber Threat Intelligence (CTI) team which exclusively focuses on improving the context of threats by enriching the Indicator Of Compromise (IoC) involved in each threat and investigating deeper on threat actor behavior.
CTI Teams leverage tools that automate threat data collection from hundreds of threat sources. Threat data is further normalized and enriched using automated playbooks and deep manual research methods to deliver a single high-fidelity threat intelligence report and service to the rest of the security teams. The critical consumer of this Intel is the SOC Analysts team.
The efficiency of the SOC depends on how quickly the SOC Analysts team takes advantage of the information from the CTI team. Some SOC tools address this need by offering collaboration or war rooms to bring CTI and SOC Analysts teams together to investigate incidents. This is a step in the right direction but would need additional manual effort and time for the teams to gain the necessary context. A more optimal way would be to make the CTI team’s research flow into the SOC Analysts team’s tool organically and in real time.
How can Threat Intel power security operations in an organic manner?
ThreatConnect’s Intelligence-Powered Security Operations approach enables CTI teams to do their investigative work as usual, and the threat IoC context they build is automatically fed to the SOC Analyst teams. This is only possible when the tools used by both teams share a common data model. As the CTI team enriches the context of the IoC, it is made available to SOC Analysts investigating that IOC in real-time. This allows the SOC Analysts team to always have immediate access to the latest information from the CTI team. These teams don’t need to go out of their way to share information in a reactive manner in meetings or email threads.
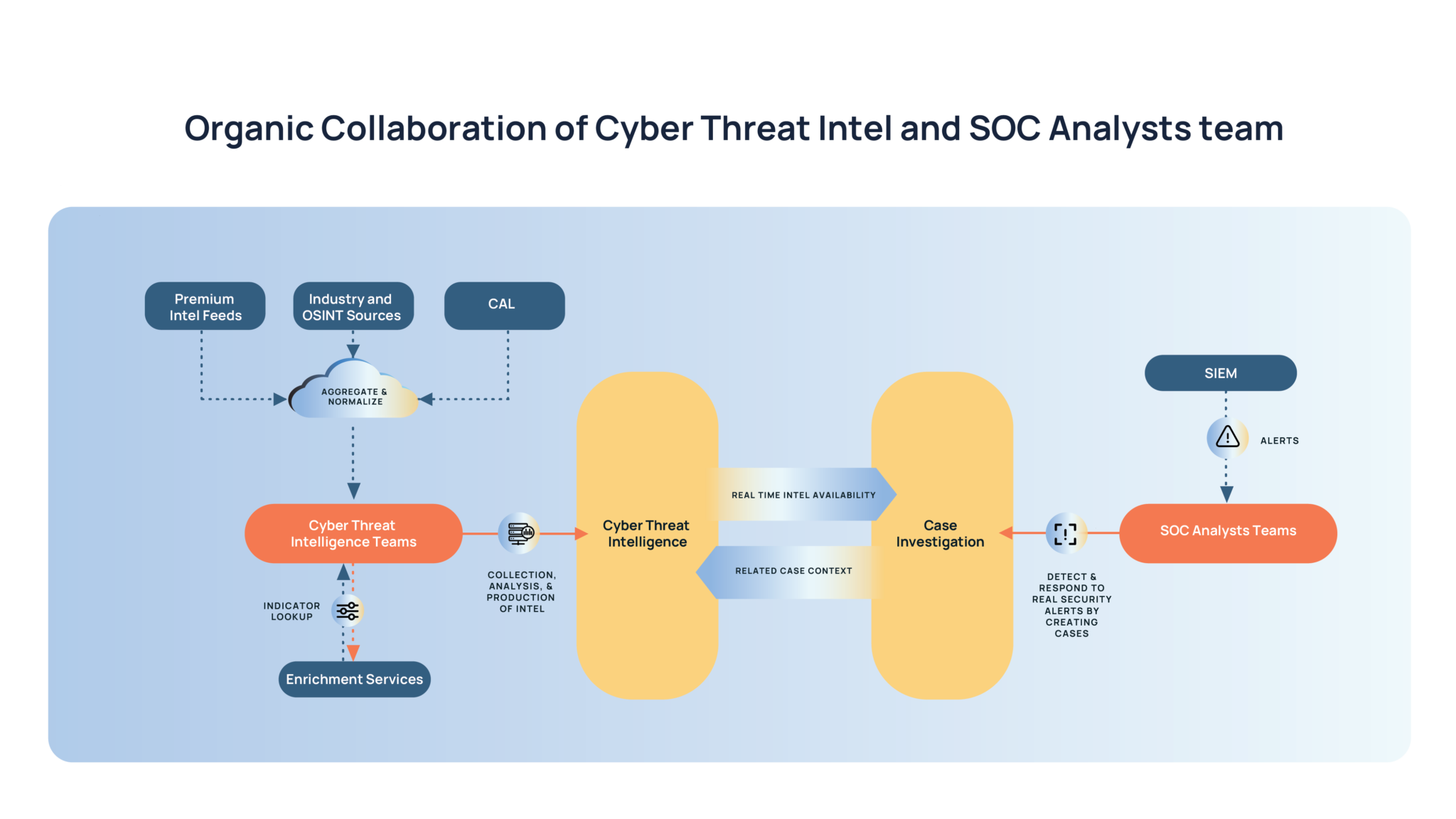
SOC Analysts team typically identifies several IOCs as part of a Case investigation and queries the IOCs against internal and external intelligence repositories to gain any additional insights to assist with the investigation. With ThreatConnect’s Intelligence-Powered Security Operations, Cases are automatically updated with relevant intel gathered by the CTI team and malicious IoCs are identified by an automatic lookup against the interested 3rd party feeds.
How cool would it be to group and visualize similar threats?
Now that we have a real-time view of IoC context available for Cases, grouping and visualizing similar threats that occurred both in the current and past time frame will help SOC Analysts to get a holistic view.
With CTI’s IoC context automatically embedded in a Case, ThreatConnect’s Threat Graph enables visualization of the patterns and links between the threat groups and IoCs. Using this, SOC Analysts can intuitively understand the complex relationships between cases in a fraction of the usual time required.
With shared visibility, teams can quickly understand complex attacks with contextual relationships among all involved entities. Users should also be able to pivot on IoCs and Groups to visualize similar Cases that are active or have occurred in the past. This will help SOC Analysts in deeper investigations, observations, and learnings that can result in faster decision-making.
With the Threat Graph view for Investigation, the SOC Analysts’ team:
- Identifies similar cases faster using shared patterns among the threat actors
- Enables analysts to assess all entities, analyze it, and make decisions on the further course of action
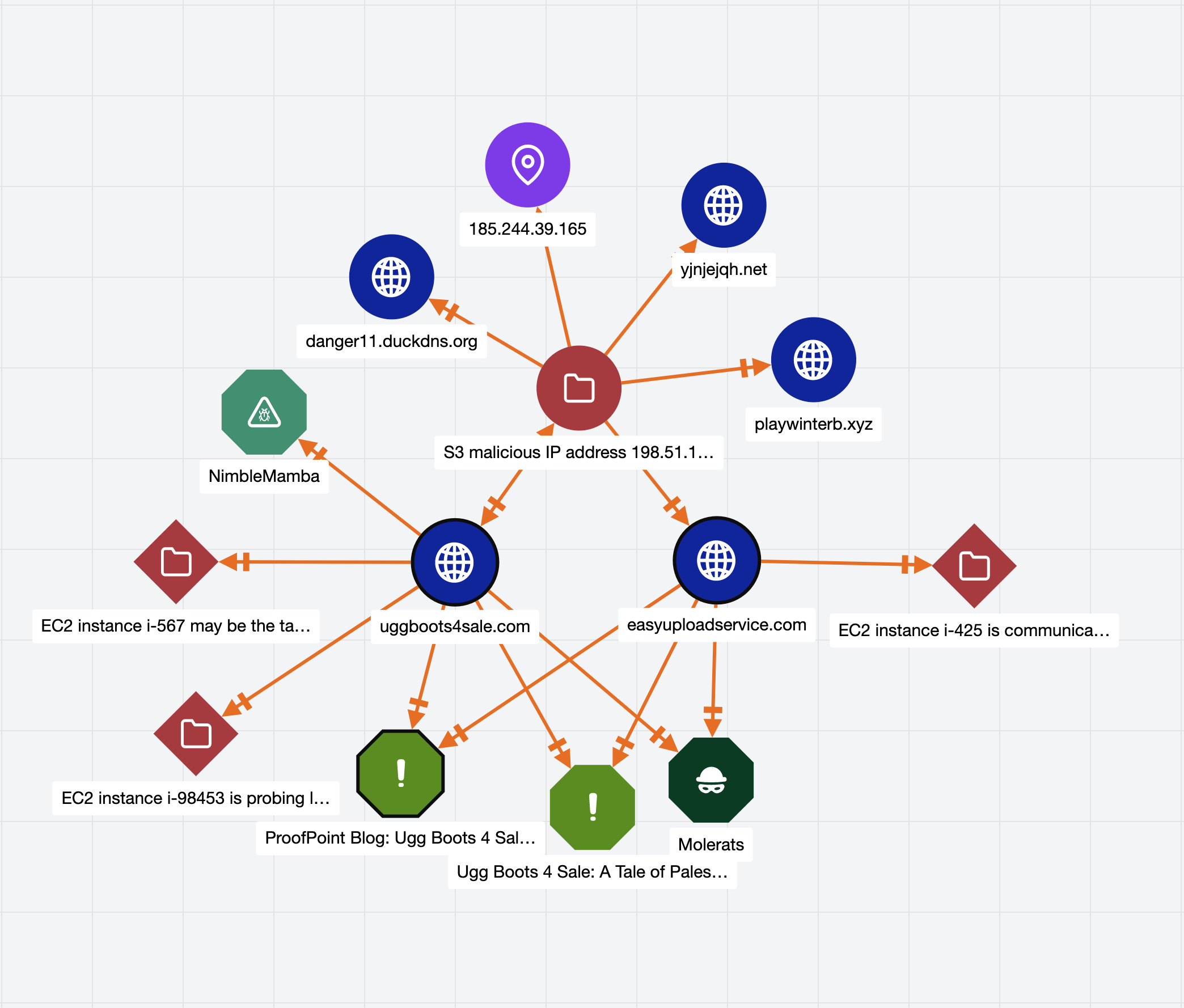
In the Graph shown above, you can see all related Indicators collected in a Case. Pivoting on each indicator to understand the threat groups and other related cases will give a full context of the attack.
From a SOC Manager’s point of view, this view can be leveraged to identify similar Cases and understand past cases and the personnel involved in those Cases. This helps them to either assign it to the same resource or leverage the knowledge of that person as well.
I can visualize now – can I take bulk actions based on my investigation?
When we have the ability to visualize relationships and group Cases, enabling analysts to act on them quickly helps them respond to threats faster
To enable faster triage of related Cases, ThreatConnect offers the ability to take bulk actions. Bulk actions could be:
- Assigning all related Cases to an Analyst. (This could be based on expertise from past cases)
- Assigning Cases to Analysts based on resorting to a common resolution
- Closing the cases and more
This will help SOC Analysts to avoid mundane, repetitive work, which improves morale and reduces MTTR.
Key Takeaways:
- SOC’s efficiency is measured by faster identification of real threats (MTTD) and responding(MTTR). To achieve higher efficiency, collaboration among CTI and Security Analyst teams is very critical.
- Forcing an unnatural collaboration to increase efficiency will result in poor employee morale and threat response.
- Leverage the right tools that organically foster collaboration, gamify threat investigation, and avoid frustratingly mundane work.
We build ThreatConnect with these objectives in mind.
ThreatConnect not only enables CTI teams to investigate a threat but also helps to disseminate the findings to SOC Analyst teams in real-time to foster collaboration. With readily available Intel as part of the Case, SOC Analyst teams can quickly take action to contain the real threats and their related IOCs.
To learn more, please take a look at the ThreatConnect Platform. Reach out to us, and we’ll be pleased to share a customized demo of the ThreatConnect Platform.

