Posted
Information overload is a common challenge facing Security Operations Centers (SOCs). Security analysts are bombarded with hundreds of alerts of potential security events. Sifting through and prioritizing the most important events can take weeks, months, or even longer.
Without the insight of threat intelligence and orchestrated processes to make sense of all the data coming through, analysts can waste valuable time slowly picking away at the problem while highly relevant and potentially harmful events go unaddressed.
An Intelligence-Driven Security Orchestration and Automation Response (SOAR) Platform can help.
Where Should You Start?
By Gartner’s definition, three characteristics make up SOAR: a Threat Intelligence Platform, Security Automation and Orchestration, and Security Incident Response.
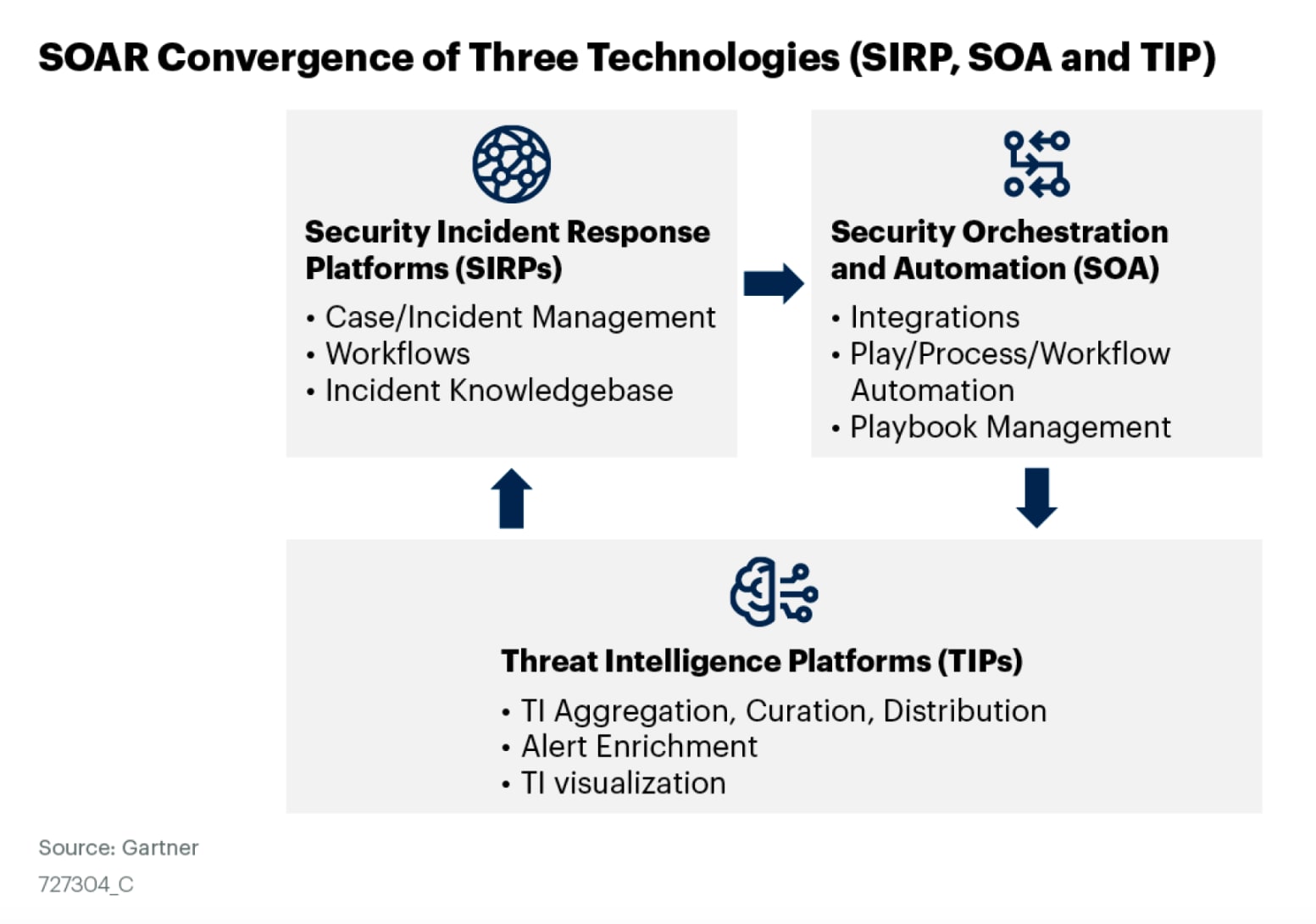
When done correctly, the combination of these capabilities in a single platform leads to the following outcomes across your organization:
- Creates a significant business impact by improving the effectiveness of SOC teams, helping them to triage, correlate, and prioritize alerts and incidents
- Improves situational awareness and enables more confident decision-making by formalizing incident response and creating consistent, measurable outcomes
- Optimizes adopted tools and processes based on valuable in-platform metrics that serve a benchmark for the team’s incident detection and response times
Intelligence-driven SOAR helps in identifying the events that require the most attention so security analysts can prioritize their time and focus on threats that matter the most.
Enriching all correlated event sources with threat intelligence is a great place to start. You will see an instant benefit to prioritizing the triage of those security events, as the number of actionable events goes from many different alerts and priority levels to a much more manageable list that can be addressed by your SOC analysts. Automated enrichment means that when an incident occurs, threat intelligence can be prioritized based on risk, and will decrease the number of potential false positives as well as increase the impact of the correlated event.
Security Operations Teams are able to focus on events that have been prioritized based on valuable intelligence and reduce the time they spend per alert and chasing false positives. Instead of being buried under a mountain of alerts, they have alerts categorized for them in different priority levels to better manage and use their valuable time.
Threat Intelligence teams are able to harness the power of threat intelligence by curating and developing a single source of truth, or a system of record, for aggregating and normalizing threat intelligence. They also are able to ensure that any intelligence they collect is being used correctly and effectively by the SecOps team.
How Can ThreatConnect Help?
ThreatConnect’s Security Orchestration and Automation Response (SOAR) platform has a revolutionary intelligence-driven approach to SOAR because our Threat Intelligence Platform (TIP) is baked right in. This approach delivers clear benefits:
- Reduces dwell time and time to respond to decrease the overall impact of an incident
- Increases staff productivity through templated workflows
- Creates a feedback loop that improves situational awareness and decision making
ThreatConnect provides knowledge of current and emerging threats, which enables analysts to examine strategic and operational intelligence from sources outside of their organization and match it with existing log sources. In the platform, analysts are able to create cases for the most critical events so teams can triage using a repeatable process leveraging automated enrichment with 3rd party services to identify threats quickly.
Lower-level tasks like alerting and blocking should also have relevant threat intel. You can automate detection and prevention tasks. Using multi-sourced, validated threat intel helps to ensure that your organization is alerting and blocking the right things. By eliminating false positives and using validated intelligence, you are increasing the accuracy of the actions taken. This accuracy leads to employee confidence and improves speed and precision.
Another helpful feature in the platform is our ThreatAssess scoring and Collective Analytics Layer (CAL) which helps to aggregate and normalize threat intelligence to help analysts figure out how to treat a piece of intelligence. This significantly shortens the time it takes to determine if you are dealing with a real incident that requires action by the response team. Make more confident decisions and reduce the time it takes to respond to critical alerts.
Event prioritization is critical to a SOC’s ability to overcome the exponential increase in data and alerts. An intelligence-driven approach to SOAR, however, is the smarter approach to determining when and how a task should be done. Intelligence allows the process to be adaptive to the changing environment and ultimately allows you to strategically plan for a better, more effective program.
