Posted
ThreatConnect has released a new GreyNoise Playbook App. GreyNoise helps analysts quickly understand which alerts don’t matter by providing context on noisy IP addresses across the internet. With this playbook app, you can look up IP addresses to validate if they are involved in any mass scanning or exploit activity, to more effectively triage alerts.
As part of the enrichment process when you query GreyNoise, there are several conclusions you might be able to draw about an offending IP address in your SIEM alert:
- Reduce the priority of the alert if GreyNoise labels the IP address “benign” or a common business service in the RIOT (Rule It OuT) data set
- Increase the priority of the alert if GreyNoise labels the IP address “unknown” or “malicious”, as these IPs are known, opportunistic scanners
- Increase the priority of the alert if GreyNoise doesn’t return a value, meaning that these IP addresses are NOT opportunistic scanners, and are more likely to be targeted activity
In other words, this integration can tell you what IPs not to worry about and what IPs are worth looking into deeper.
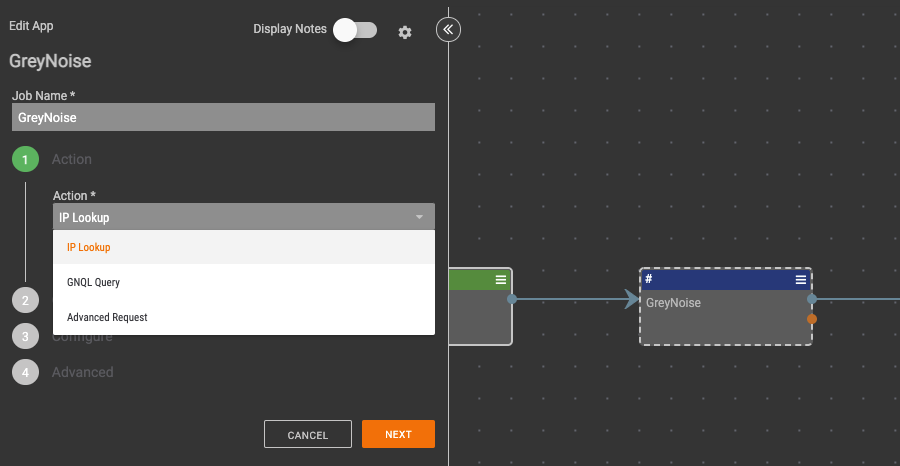
This integration consists of a single Playbook app that will allow these actions:
- IP Lookup – Submit a single IP address to GreyNoise to validate whether or not it’s part of mass automated activity.
- GNQL Query – Perform a custom query using the GreyNoise Query Language to retrieve IP addresses that match specified criteria.
- Advanced Request
GreyNoise Playbook App
Through this integration, the following capabilities are now available:
- Use GreyNoise to Corroborate Alerts
- As part of your analysis, utilize information from GreyNoise to aid and corroborate intelligence analysis or validate the accuracy and severity of security alerts. By verifying this information, you can feel confident to make informed decisions.
- Aggregate Enrichment
- As part of your security process, you may want to aggregate available enrichment and analysis from various outside sources into one location – the ThreatConnect Platform. As a result, you have a more holistic understanding of potential threats to make the most informed decision as part of your analytic, investigative, and remediation actions.
- Perform All-Source Analysis and Reduce False Positives
- As part of your analysis, corroborate or dispute the output from other tools and services to perform an all-source analysis that analyzes threat information from multiple sources, and identifies IP addresses that have been incorrectly labeled as malicious Because operations feed intelligence in a continuous loop, your Security Operations Center (SOC) and Incident Response (IR) teams can leverage the work from the Threat Intelligence team during their investigations.
With the GreyNoise playbook app, you can quickly query for noisy IPs and create remediation plans to protect your network. If you’re a ThreatConnect customer, please reach out to your dedicated Customer Success Team for more information on utilizing the GreyNoise App. If you’re not yet a customer and are interested in ThreatConnect and this integration, please contact us at sales@threatconnect.com.
