Posted
Getting Started with Threat Intelligence: A Guide for the ONG Community
How ONG institutions can get started with ThreatConnect to gain context about threats
The utilities vertical, specifically oil and gas (ONG) is a complicated one, especially when it comes to information security. Each company has multiple endpoints that they need to protect – and many of those endpoints are very different and must be protected in specific ways. These can range from things like corporate laptops all the way up to industrial control systems or SCADA (supervisory control and data acquisition) systems. Information security analysts at these organizations must understand the policies and controls of each of the endpoints, how they are affected by different vectors, and which threats are targeting them. Understandably, this can be both difficult and time-consuming.
Relevance is Key
Because analysts have such a variety of endpoints to protect, understanding what information is relevant to the organization is critical. Depending on the organization, analysts consume indicators (pieces of information about threats) from a number of different locations and sources.
The ThreatConnect Platform provides an easy way to find relevant threats and gain more context, such as attack patterns or previous victims. We will walk through how ONG organizations can get started in the Platform.
Getting Started with Threat Intelligence: How to Find Out What’s Relevant to You
Step 1: Create a System of Record
One of the main challenges in the utilities vertical is a fairly common one: collecting, normalizing, and enriching threat intelligence sources. Utilities have unique assets to protect, so analysts may not be able to use common sources. They need to figure out what sources are worth their time and effort.
In order to evaluate the sources, you need to put them all into one place. In ThreatConnect, you can ingest data from 100+ open source feeds, our premium feed partners, or any other accessible source.
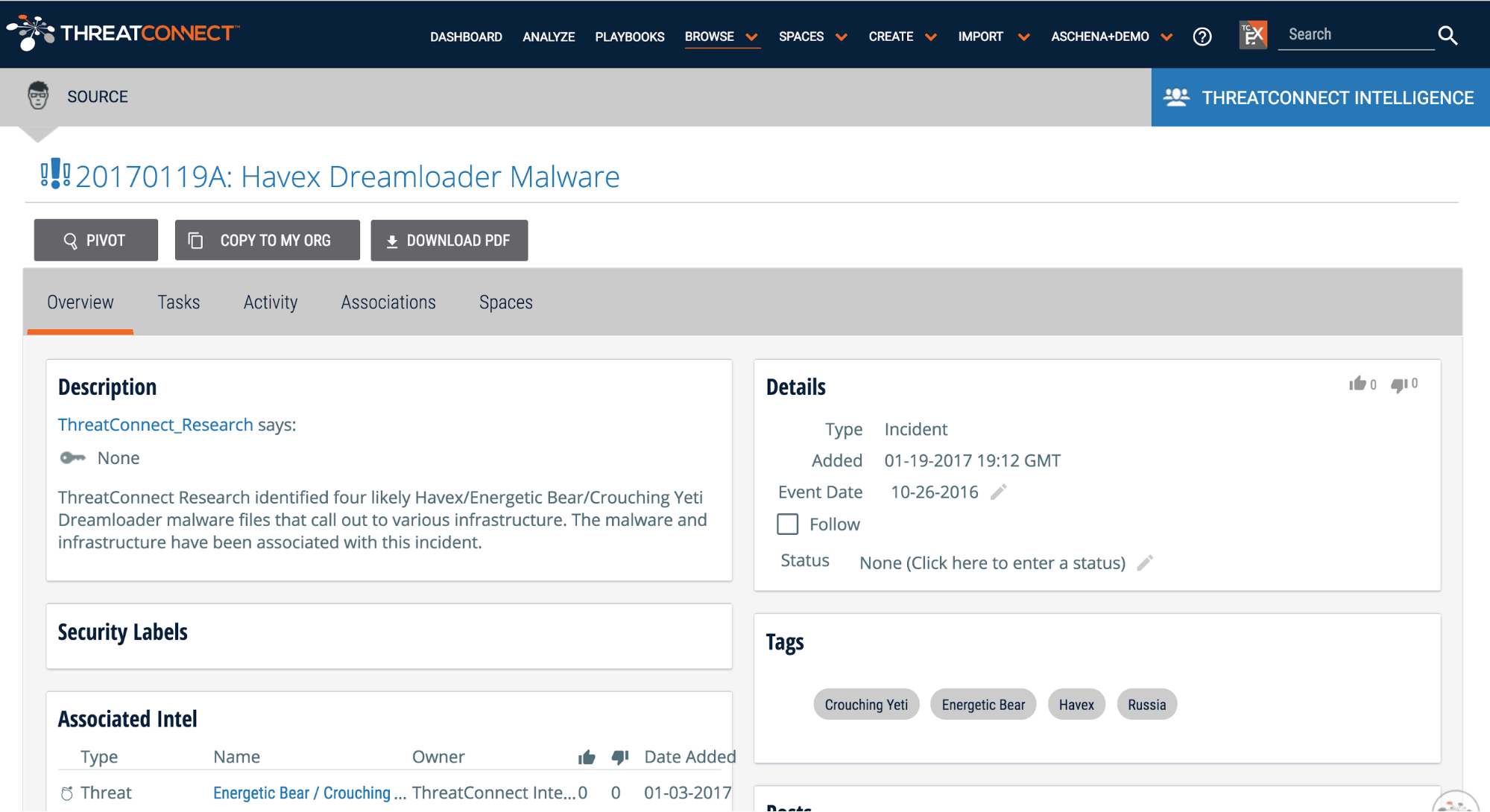
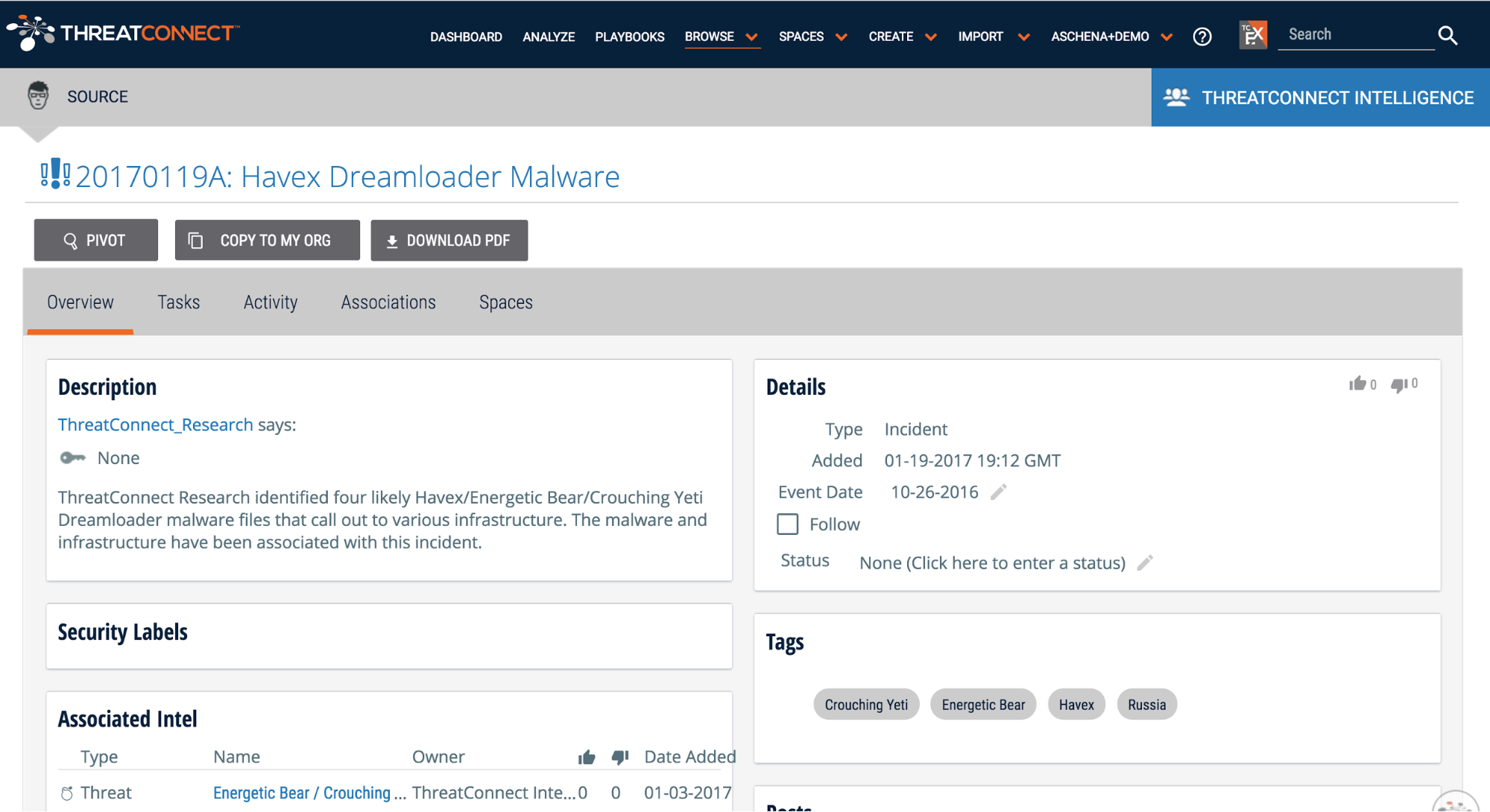
The best place to start is to look at utilities-specific data in threat intelligence sources that are already in the ThreatConnect Platform. Once you’ve logged into your ThreatConnect account, click on the Browse tab. You can choose to look at specific indicators (host, address, file, etc.) or group types (campaign, incident, threat, etc.). When you spot something of interest, click on the indicator or group to see a quick overview of details such as background, Platform ratings, and more.
You can export these indicators into a CSV file and add them to your existing tools. Or, if you’d like to export indicators to your tools automatically, you can request to use ThreatConnect’s API. To do this, contact our sales team at sales@threatconnect.com.
Recommended Sources:
- ThreatConnect Intelligence Source
- Ransomware feeds
○ Abuse.ch Ransomware Tracker
○ Malware Domain Blocklist
○ PhishTank Source
Step 2: Understanding What Intel is Relevant
Now you know how to look for data in the ThreatConnect Platform. However, as we all know, indicators (and even threat intelligence) are not one size fits all. Some feeds are noisy and have a lot of false positives, while some are valuable and full of relevant threat intelligence. There’s even more ways to find pertinent information: utilities-specific tags.
Tags are how ThreatConnect categorizes data in the Platform, and range from specific industries to country of origin to malware families and more. As ThreatConnect users – including our own Research Team – hunt, analyze, and create threat intelligence in the Platform, specific tags are applied to enable easy searching. You can also search for Tags using the ThreatConnect Browse screen. Once you can categorize and view the data, it is much easier to recognize trends, and view historical knowledge or observations in your network.
Recommended Tags:
And when you search for utilities tags, you can choose to view indicators or incidents that have had the tag added. We recommend looking at incidents, where you can easily dive in to see how indicators relate to each other, observe adversary attack patterns, and more.
Recommended Incidents:
- 20170119A: Havex Dreamloader Malware
- 20160602A: IRONGATE ICS-focused Malware
- 20170113B: Malicious File Communicates with tetraco.netne[.]net
Step 3: Leverage Peer Knowledge
Communities are one of the best places to get vertical-specific data in the Platform. Communities in ThreatConnect are run by organizations that want to share, collaborate, and ask questions about threat intelligence or users with specific interests or assets. There are two Utilities Communities in ThreatConnect – the ONG Community and the EnergySec Community. Members of these communities can access the data being shared. Also you can aggregate industry specific information from ISACs or STIX/TAXII feeds. Upon joining, follow a Community to receive immediate or summary alerts of incidents or comments that get posted. This is an excellent way to get started with threat intel.
Recommended Communities:
- ONG Community
- EnergySec Community
Bottom Line
No matter your organization’s stage of maturity, it boils down to the same issue – information security is a resource challenge. It’s difficult to figure out what data is relevant to you and your organization. Creating threat intelligence and defining what poses the most risk is a time consuming and resource-intensive process. ThreatConnect helps simplify information security tasks and processes by making it easier to find relevant threat intelligence for the utilities community.
But that is just the beginning. Not only can utility organizations search ThreatConnect for ONG-specific threat data and threat intelligence, but can also begin to use that information in their security program. ThreatConnect allows you to integrate your disparate tools, automate your manual processes with orchestrated playbooks, and ultimately make your team more efficient. Whether you are just getting started with threat intelligence or are a Fortune 500 oil company, ThreatConnect can help your team save time and identify threats faster.
This is our second post in a series directed toward specific verticals. In case you missed it, check out our guide for retailers here.