Posted
Famous Chollima is a North Korean state-sponsored cyber threat actor tracked as active since at least 2018. Their primary objective is to infiltrate organizations by posing as legitimate remote IT workers, thereby generating income for the North Korean regime and conducting cyber espionage activities. They are also known by aliases such as:
- NickelTapestry
- PurpleBravo
- TenaciousPungsan
- UNC5267
- VoidDokkaebi
- WaterPlum
- BadClone
Instead of launching attacks from the outside like typical cybercriminals, this group infiltrates companies by posing as legitimate employees. They secure remote IT roles by submitting fraudulent identities, doctored resumes, and counterfeit qualifications, allowing them to slip into secure systems under the radar.
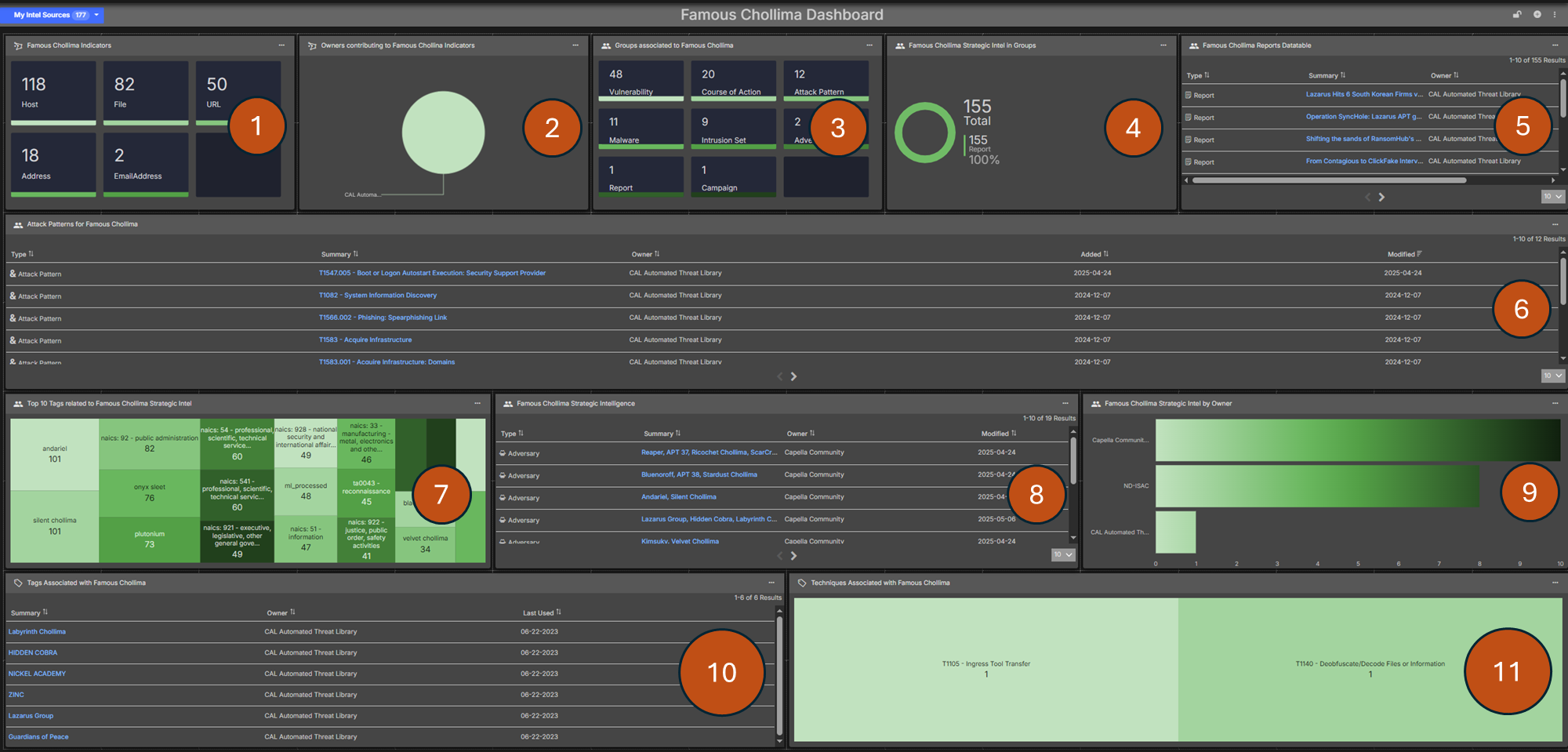
The Famous Chollima Threat Dashboard in ThreatConnect provides security teams with real-time intelligence on the Famous Chollima. This dashboard aggregates data from multiple sources, enabling analysts to detect, monitor, and respond to Famous Chollima-related threats proactively.
Key Benefits:
- Centralized Intelligence: Compiles Famous Chollimag-specific indicators of compromise (IOCs), tactics, techniques, and procedures (TTPs) from open-source intelligence, threat feeds, and internal telemetry.
- Real-Time Threat Tracking: Offers continuous updates on Famous Chollima’s attack infrastructure, victimology trends, and newly observed techniques.
- Incident Response Acceleration: Facilitates rapid threat triage and response by providing enriched intelligence and contextual analysis.
- Customizable Reporting & Visualization: Delivers interactive charts, campaign timelines, and executive-ready reports tailored to the Famous Chollima threat landscape.
- For customers interconnected to defensive technologies — Automated Correlation: Utilizes ThreatConnect’s automation engine to correlate Famous Chollima-related IOCs with existing intelligence across adversary profiles, intrusion sets, and emerging threats—assisting in prioritization and risk mitigation.
By leveraging the Famous Chollima Threat Dashboard, security teams can enhance their threat intelligence capabilities, reduce response times, and strengthen their organization’s resilience against ransomware attacks.
Note: In order to realize the full value of this dashboard, customers may require integration with premium or commercial threat intelligence sources such as those provided by Mandiant, Recorded Future, or CrowdStrike
Lead Contributor – Roland David Czintos , Customer Success Engineer
Dashboard Components:
The following is a summary of key components of the dashboard.
- All indicators added after January 2024 associated with Famous Chollima.`
- Breakdown of OwnerNames for the indicators extracted in Component 1.
- Groups (vulnerabilities, malware, campaigns, etc.) associated with Famous Chollima.
- All reports tied to Famous Chollima, including those with Chollima, Silent Chollima, or other aliases in the summary (displayed as a count in a card).
- A data table with the report titles from Component 4.
- All attack patterns tied to Famous Chollima, used in the MITRE ATT&CK framework to guide defense against Famous Chollima attack patterns.
- The most popular tags seen across the group objects related to Famous Chollima.
- All threat actors in the threat intelligence platform with aliases related to Chollima.
- Breakdown of OwnerNames for the threat actors found in Component 8.
- All tags seen across threat actors with Famous Chollima in their name.
- Techniques associated with Famous Chollima.
To gain access to the Famous Chollima Threat Dashboard, please reach out to your Customer Success team or email us at customersuccess@threatconnect.com.
Further Resources
For more detailed information and resources on Famous Chollima, please refer to the following:
| Resource | Description | Link |
| TrendMicro | Trend Micro, a global cybersecurity leader, helps make the world safe for exchanging digital information. Fueled by decades of security expertise, global threat research, and continuous innovation, our cybersecurity platform protects 500,000+ organizations and 250+ million individuals across clouds, networks, devices, and endpoints. | TrendMicro Article |
| CrowdStrike | CrowdStrike secures the most critical areas of risk – endpoints and cloud workloads, identity, and data – to keep customers ahead of today’s adversaries and stop breaches. | CrowdStrike Case Study |
We urge all organizations to remain vigilant and proactive in their cybersecurity efforts. By implementing these recommendations, you can significantly reduce your risk and protect your critical assets.