Posted
Gartner recently released the latest version of their 2023 Market Guide for Security Threat Intelligence Products and Services. We’re honored to be named a Representative Vendor, but equally excited by the insights and advice offered in the Gartner report.
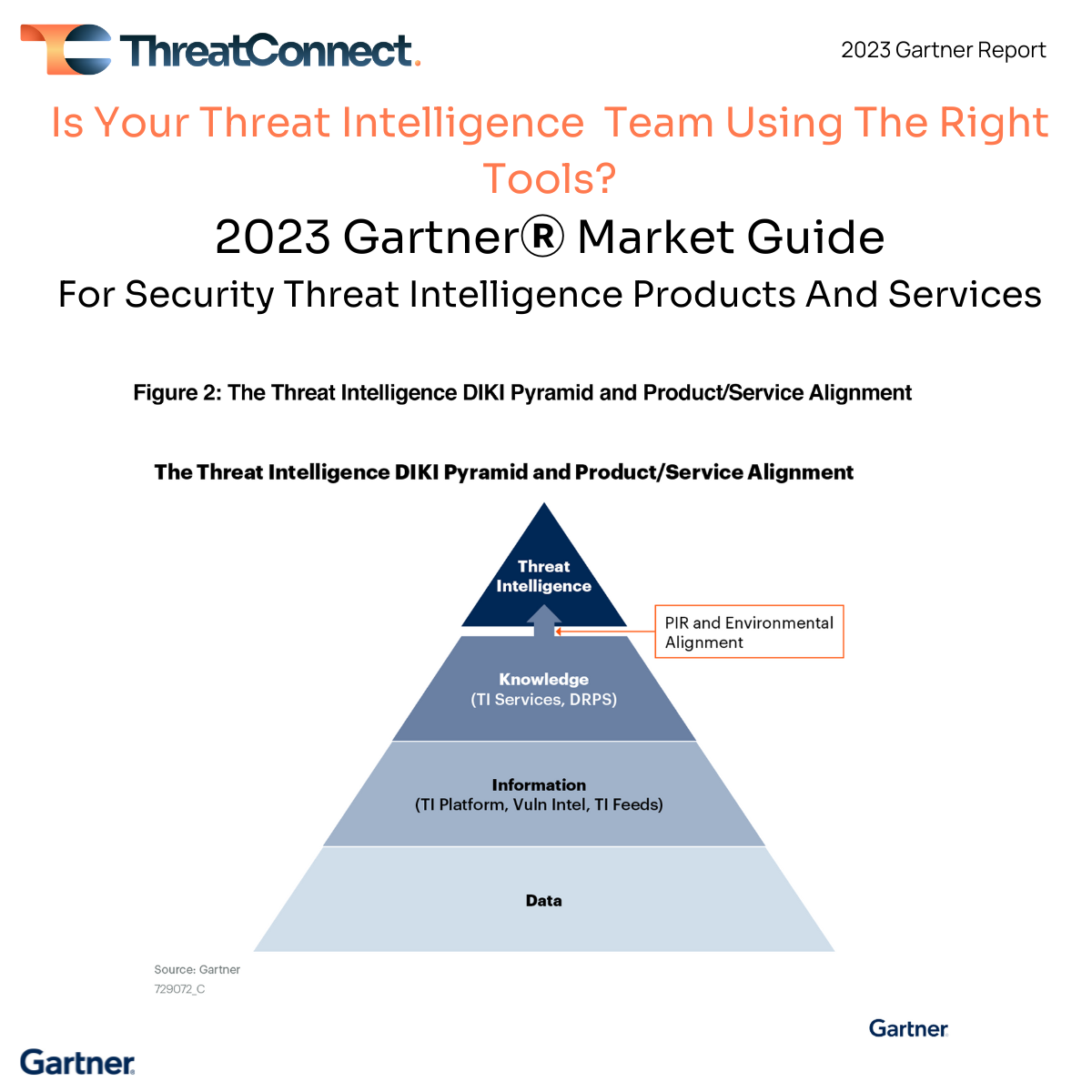
I find the Key Findings and Recommendations to be a great summary of the challenges we hear in the market, and whole heartedly agree with the recommendations. I commend the authors for calling out these specific points that we believe need to be recognized and addressed by organizations, whether they are just starting out on their threat intelligence journey or are in the maturation phases. The failure to produce priority intelligence requirements can have a significant impact on the success of a threat intelligence function and team, keeping them from being the heroes of security operations. Gartner had a number of recommendations and observations:
- “Although a larger variety of organizations are choosing threat intelligence (TI) services and products to enrich their security programs, many haven’t formalized these programs, resulting in a lack of defined requirements, diminished actionability, and an overall lack of long-term program defensibility.”
- “The core of any TI program is priority intelligence requirements (PIRs), used to identify where the organization will focus intelligence efforts and what tools are required to achieve it.”
- “They are overwhelmed with data because they have not defined what they really need to focus on and care about. Security and risk management leaders must demand that PIRs be defined for their organizations before any TI product purchases are made.”
- “Even today, a key issue is actionability. Security and risk management leaders must understand knowing is not enough, and they must be able to take action. Keeping PIRs in mind will be enormously helpful because you will not lose the end goal and can make sure that you are addressing the PIRs, no matter what you do.”
Another point worth highlighting is the distinction between platforms and services. Threat intelligence products, aka the technology, are not the same as threat intelligence services. I was pleased to see this distinction specifically addressed in Figure 3: Market Overlap Between Threat Intelligence, DRPS, and EASM — Part 1 in the report.
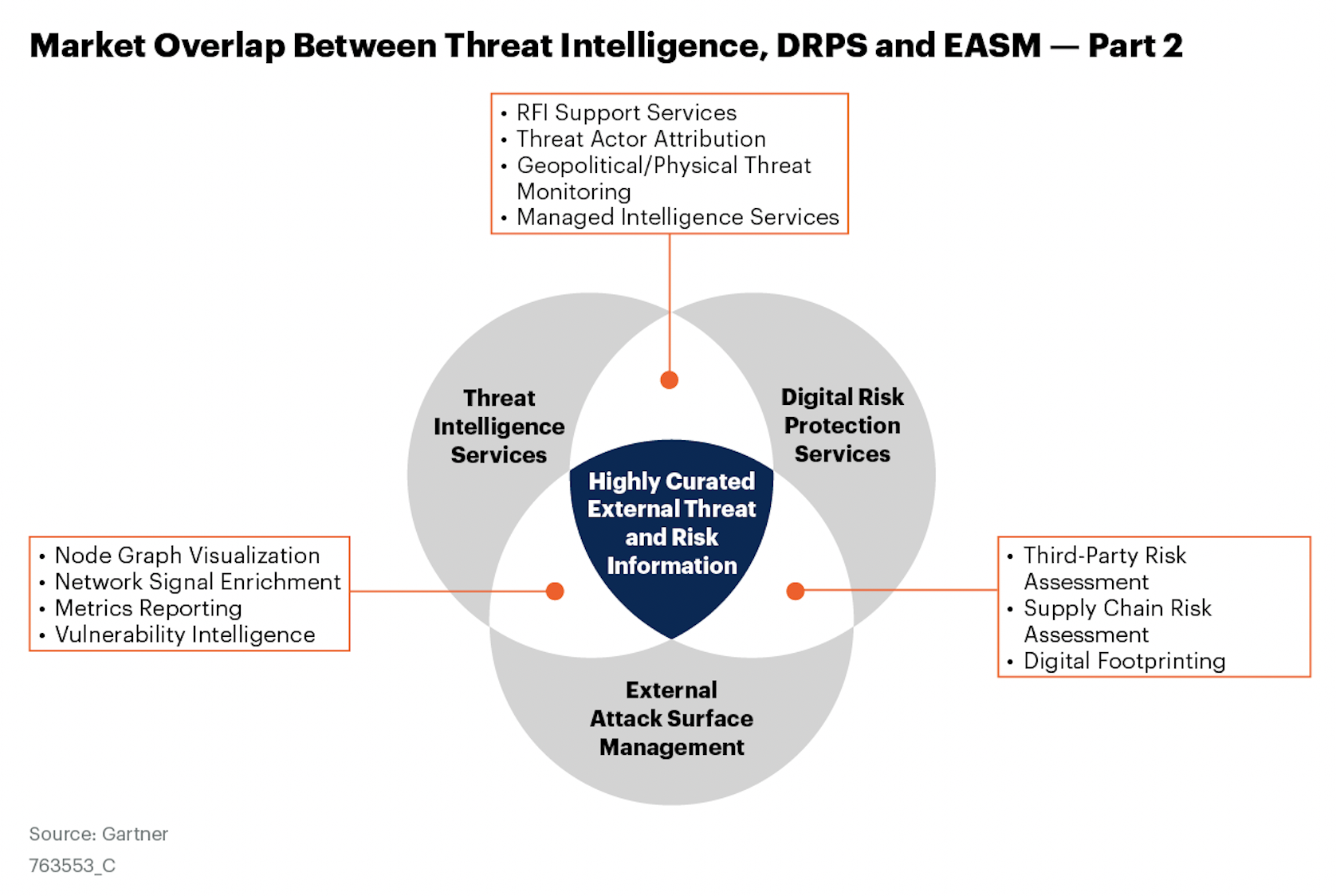
This is critical to understand from a buyer’s perspective because a threat intel platform (TIP) is what allows you to manage and operationalize threat intelligence, and is necessary when there are multiple intel data sources being consumed – commercial or paid intel (aka the services), open source intel (OSINT), intel shared between trusted partners like ISACs, and internally produced intelligence like from a SOC or incident response team. Even Gartner calls out that “There is not a single TI source, whether open-source, commercial off-the-shelf or government-created, in the market today, which has visibility into everything.” We agree! It’s why we believe that a diversity of threat intelligence sources aggregated into a single source of high-fidelity threat intelligence is the only way to identify, prevent, detect, and respond to the adversaries targeting your organization.
Finally, I commend the authors on ending the report by making the linkage between threat intelligence and cyber risk quantification – “Promote cohesion among intelligence services by correlating across your external threat data for better risk quantification and prioritization.” ThreatConnect also has a cyber risk quantification (CRQ) solution – Risk Quantifier – that easily integrates into ThreatConnect’s TIP to bridge the gap between intel and cyber risk.
Want to learn more? Reach out to us to get a customized demo and learn how ThreatConnect’s Platform can help you aggregate, normalize, and act on data.
—
Gartner, Market Guide for Security Threat Intelligence Products and Services, Jonathan Nunez, Ruggero Contu, Mitchell Schneider, 4 May 2023.
This graphic was published by Gartner, Inc. as part of a larger research document and should be evaluated in the context of the entire document. The Gartner document is available upon request from ThreatConnect.
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose