Posted
Gain insight into possible permutations of domain names to indicate suspicious activity and further analysis
For this week’s Playbook Fridays post, we’re mixing things up a little. Instead of directing you on how to set-up a specific Playbook, we’re going to help you take advantage of an App we built which is set up on top of preconfigured Playbooks.
Introduction
In Star Wars: A New Hope, Luke, Han, and Chewy are faced with the daunting task of rescuing Leia from a holding cell in the Death Star. In comparison to the Death Star, their forces are minimal and their tech is limited to the door-opening capabilities of the valiant astromech droid R2-D2. Yes, C-3PO was there but you have to admit he was totally worthless and nearly led our heroes to a disgusting demise in the dianoga-laden disposal.
Despite being overmatched in terms of numbers and technology, Luke and Han are able to traverse multiple layers of security and exfiltrate the Princess by stealing armor and impersonating Stormtroopers. Enter the First Look Vulnerability, wherein an entire security function can be undermined by the immediate trust that we place in things that simply look familiar to us. Upon initial inspection by other Death Star personnel, Luke and Han look like all the other Stormtroopers, which is why their plan was ultimately successful. A more thorough inspection of them would have revealed neither possesses appropriate Stormtrooper knowledge and neither of their biometrics match those belonging to known troopers — notably one of them was a little short. They also possess marksmanship skills far out of proportion to your average Stormtrooper.
This same paradigm plays out daily in the cyber security world. In comparison to their targets, malicious APT groups are often overmatched in terms of sheer numbers and the technology that they have at their disposal. Large organizations often have hundreds of individuals and millions of dollars in technology dedicated to cyber security whereas an APT may have three hackers and a paltry budget dedicated to compromising those same organizations. To facilitate their malicious efforts, APTs will often take the same approach as Luke and Han: exploit the First Look Vulnerability to gain insider access.
To exploit this vulnerability, bad guys leverage domains that spoof those belonging to their targets or organizations that their target would otherwise trust. In fact, spoofed domains were an essential part of many of the large-scale APT breaches from the past three years. Notably, Chinese APT actors leveraged such domains to breach healthcare and government organizations, ultimately compromising personal information for millions of individuals. Domains such as prennera[.]com and logitech-usa[.]com (Wekby report) initially appear to be legitimate, but in fact are not and can be leveraged in a range of malicious functions from delivery to command and control. Russian APT group Fancy Bear used multiple spoofed domains like misdepatrment[.]com, actblues[.]com, and wada-arna[.]org in operations targeting organizations like the DNC, DCCC, and WADA in 2016. Criminal groups like Carbanak also have used spoofed domains like baskin-robbin[.]com and buffalo-wildwings[.]com for cybercrime. However they are used, they are often successful because these domains exploit the implicit trust we have in the familiar.
The Domain Spinning Workbench
So what? Yeah, bad guys use sneaky domains, what can we do about it? Well, a lot, as it turns out. First and foremost, these domain squats have to be identified. There are a variety of tools, including DNStwist and URLCrazy, that can help an organization identify those domains that spoof or typosquat their own or the organizations that they most frequently work with.
We’ve incorporated those tools into a set of apps and playbooks that can be used in ThreatConnect via our Domain Spinning Workbench. This workbench allows users to input a domain of interest and then returns all of the identified spoofed domains from one of the domain spinning tools, along with relevant WHOIS and DNS information, and then allows users to import any notable domains or registration email addresses into ThreatConnect for further research.
Configuring and Using the Workbench
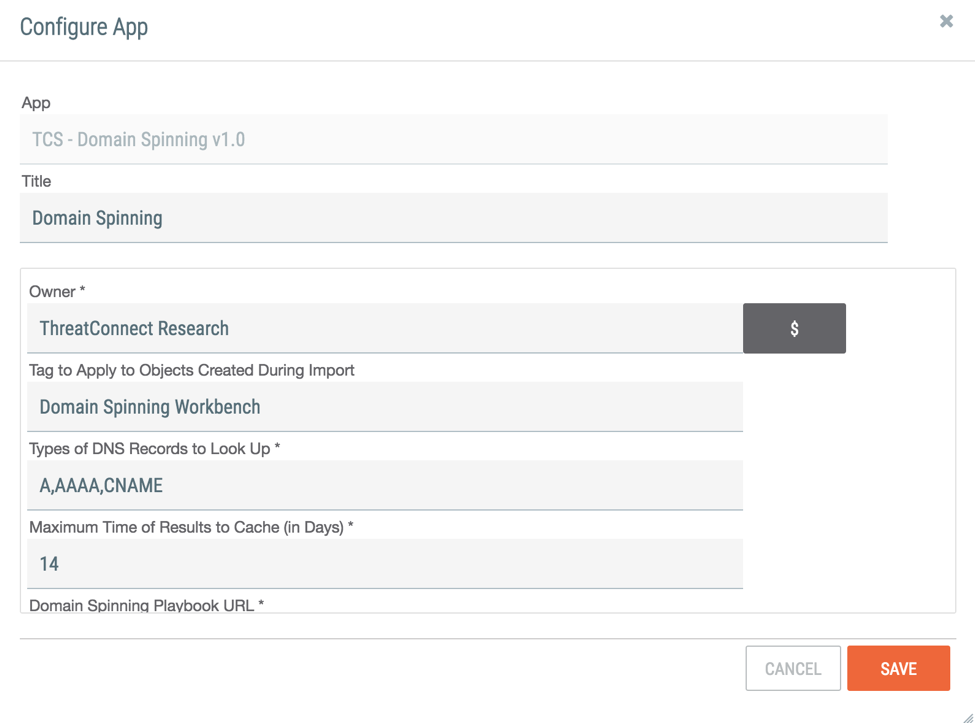
To use the workbench, we’ll start by configuring the Space App. Here in the configuration panel for the app, we can specify things like what Tag to apply to any imported domains or email addresses.
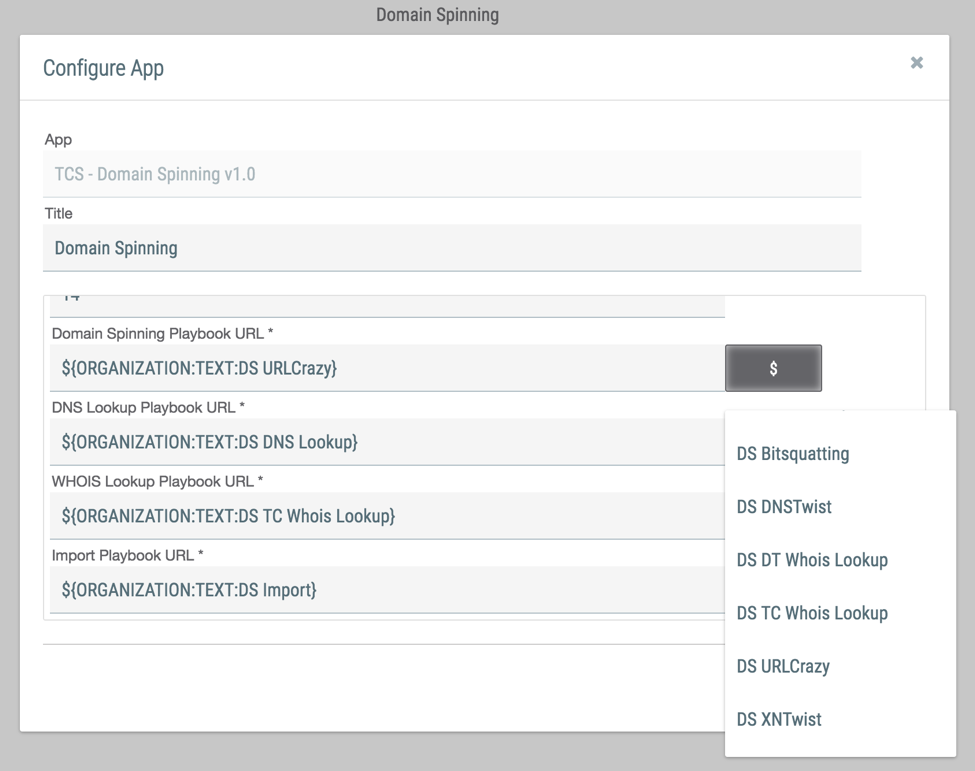
Further down in the configuration panel is where we can select which specific playbooks to use in the workbench. For example, for the Domain Spinning Playbook, we can choose DNSTwist, URLCrazy, Bitsquatting, or XNTwist. Depending on what type of spoofed domains we’re looking for, we might change which playbook we use. We can also specify which playbook we want to use to conduct the WHOIS lookups for the identified domains.
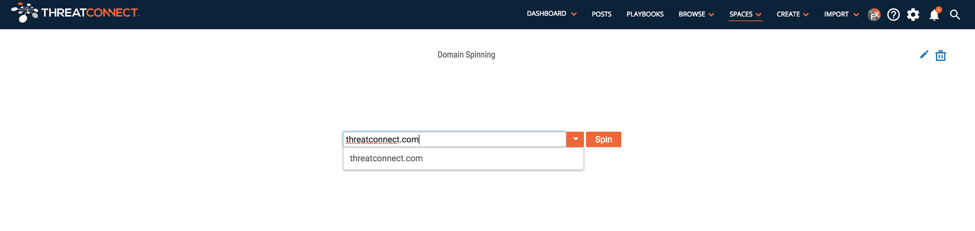
After configuring the workbench, we can use it to spin an input domain. In our case, we’re going to use our own domain to see what suspicious, ThreatConnect-spoofing domains show up.
Using the Results
As the app is running, the number of domains remaining to process is shown. During this time, the workbench is gathering results from several of the playbooks specified in the previous configuration panel. Notably, the spoofed domains are being identified and the WHOIS information for them is being pulled into the workbench.
After the playbooks have completed, the workbench returns the results. In this case, over 1700 domains possibly spoofing ours are identified. This includes both registered and unregistered domains; however, the registered domains show up first and the unregistered domains will follow and are called out as not registered. The workbench provides the WHOIS and DNS for the original, provided domain to compare against the results. This can help identify those domains that your organization has already registered.
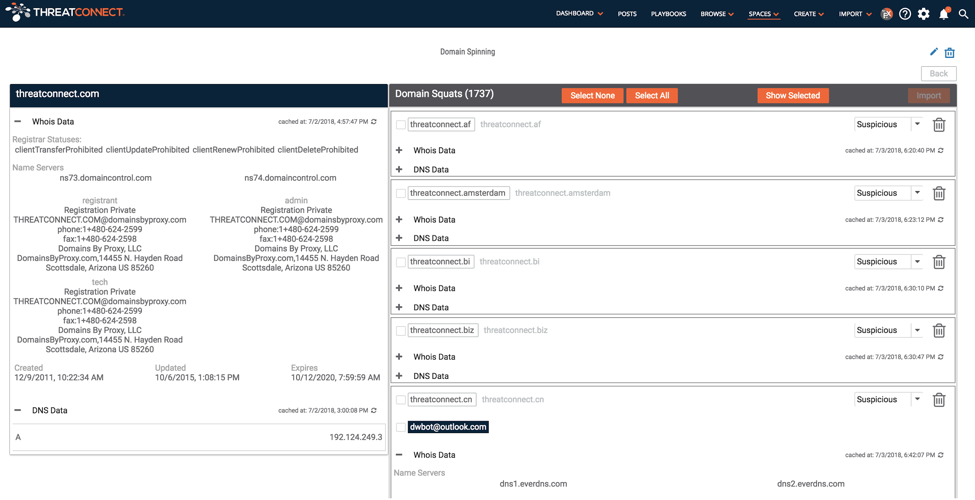
When available, the workbench calls out the registrant email address and provides an option to import it into the ThreatConnect platform. For each identified domains there are also drop down sections for the WHOIS and DNS data that may help identify those domains that stick out based on who registered them or where they are hosted.
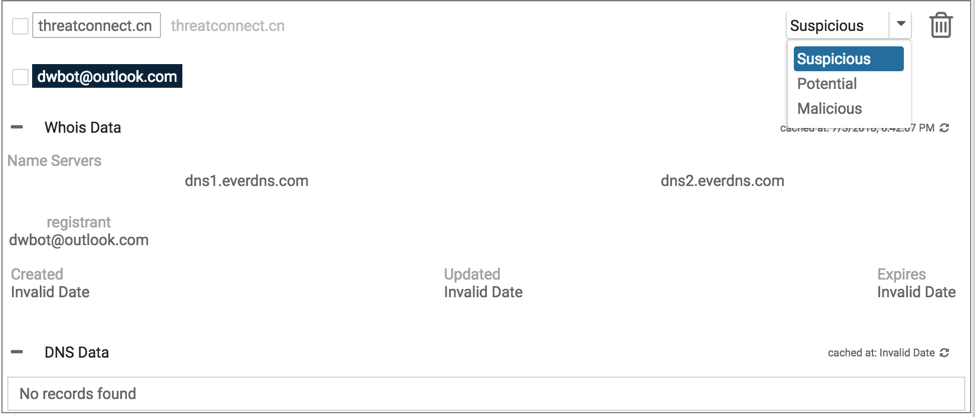
When importing from the workbench, you can choose to specify the given domain and/or registrant email address as suspicious, potential, or malicious.
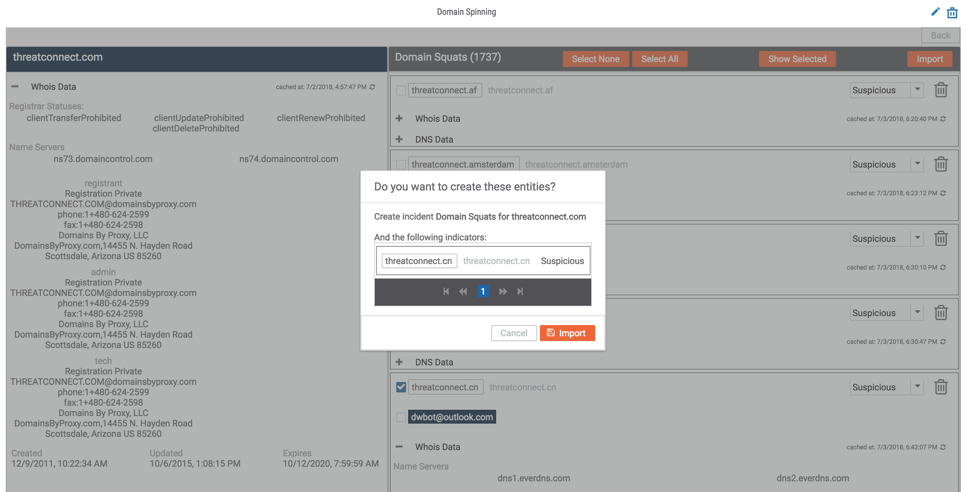
By importing the domains that we’re concerned about into ThreatConnect, we can then use ThreatConnect’s various investigative capabilities to build out our understanding of the domains, the activity associated with it, and the actor(s) behind it. Below, we’re using our DomainTools Spaces App to further review the WHOIS information and identify other intelligence related to the dwbot@outlook[.]com registrant.
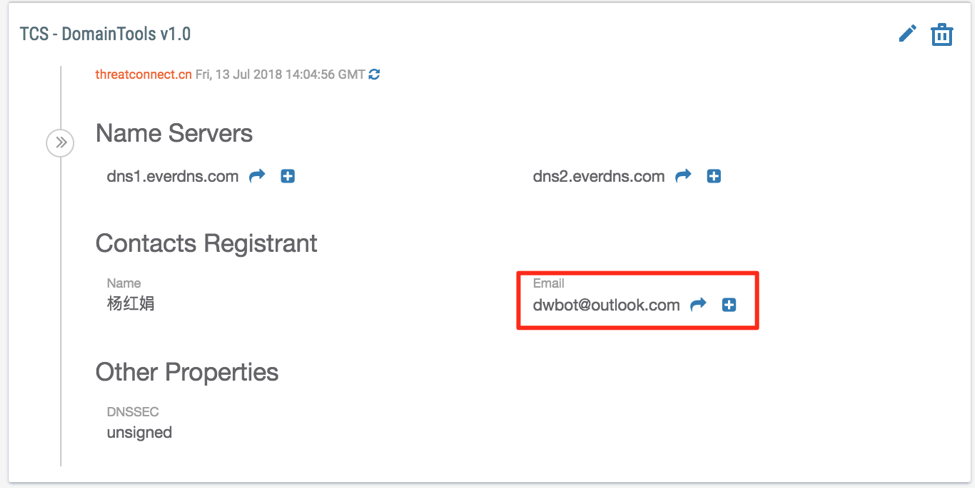
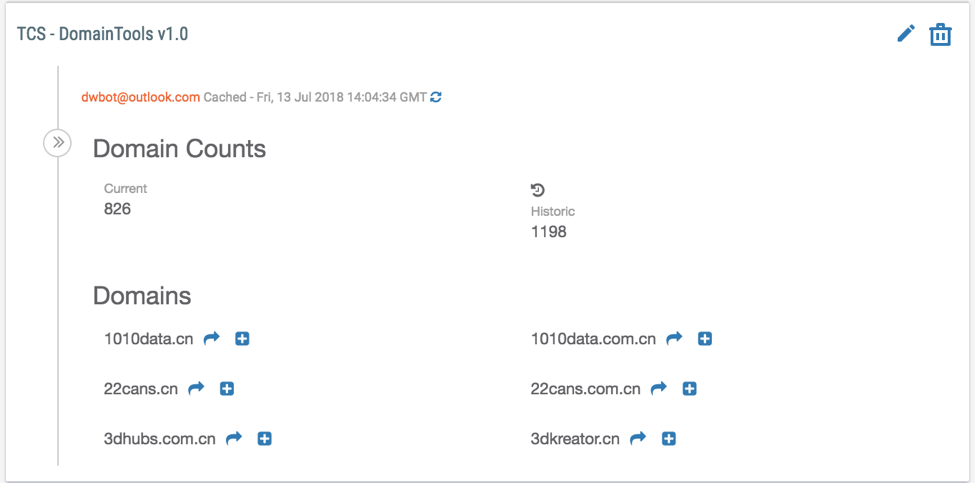
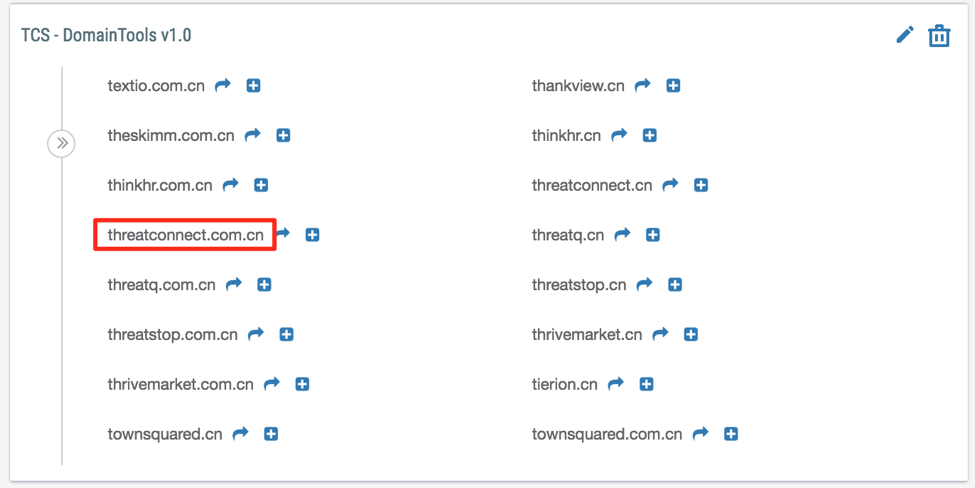
By clicking on the arrow next to the email address, we see that dwbot@outlook[.]com has registered about 1200 domains, likely indicating they are a mass registrant. However, amongst the registered domains, we find another notable domain for us threatconnect[.]com[.]cn and several hundred other spoofed domains. Based on such consistencies, an organization might then want to proactively monitor for new domains registered by the identified registrant or actor that may be relevant to their organization.
So What Can You Do With This Information?
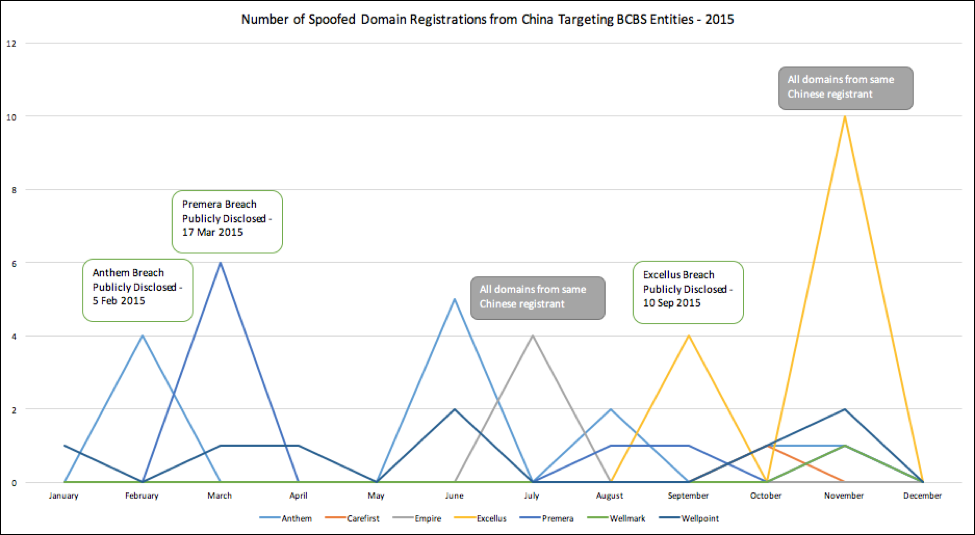
Knowledge of a single registration targeting your organization is helpful, but identifying trends in these registrations over a period of time can potentially identify APT activity targeting your organization. From a strategic perspective, knowledge of these domain squats may inform higher level analysis of adversary motivations against the organization or even an industry. For example, with the information we acquired via the Workbench, we took a look at spoofed and typosquatted domain registrations from Chinese registrants targeting Blue Cross Blue Shield entities Anthem, CareFirst, Empire, Excellus, Premera, Wellmark, and Wellpoint in 2015. The graph below shows the number of those domains that were registered by month against each of the specific BCBS entities.
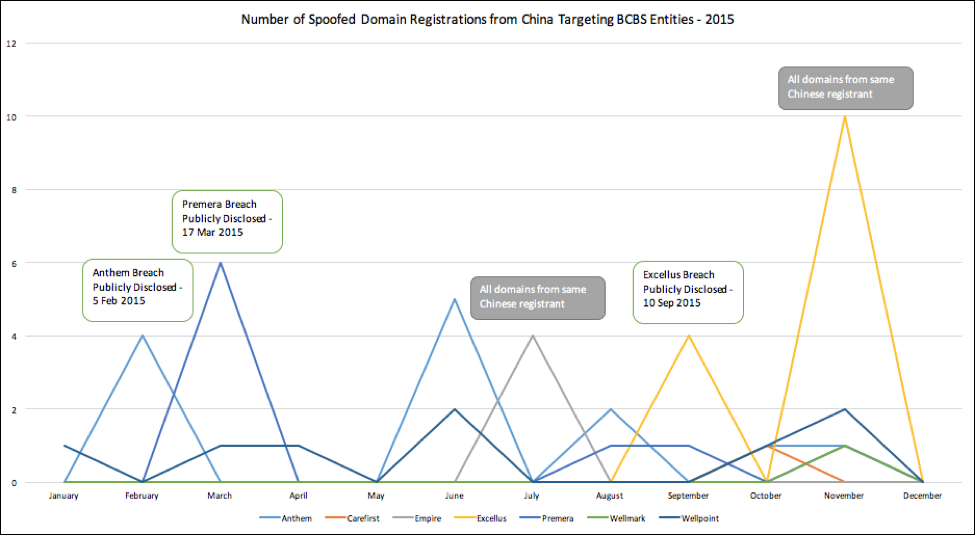
There are some pretty clear spikes in activity, three which line up exactly with the public disclosure of breaches targeting those companies. More specifically, in these instances, registrants in China began registering the domains that caused the spike less than two days after the breaches were publicly announced. These registrations typically came from Chinese mass registrants and do not otherwise directly indicate malicious activity; however, this could be an indicator for Chinese APT activity attempting to redo its infrastructure for future efforts against those organizations after their previous attacks had been detected. Three of the other spikes didn’t line up with any notable events, but in two of the cases all of the domains were registered by a single Chinese registrant.
From a threat intelligence perspective, the presence or registration of such domains does not indicate that malicious activity has taken place. However, these registrations and the context associated with them should be further investigated, analyzed, and memorialized to ensure that the organization is properly defended against any potential threats that may be attempting to exploit the First Look Vulnerability. This is where having a threat intelligence platform, like ThreatConnect, becomes integral.
Leveraging ThreatConnect’s Analyze function, we were able to quickly determine whether we had any additional intelligence on the BCBS spoofing domains or their associated WHOIS information. The results indicated that the email address yuming@yinsibaohu.aliyun[.]com, a mass registrant, was previously used to register domains used in the Chinese Scanbox framework and by Chinese APT TG-3390. However, this Yuming email address has registered over two million domains, making that connection an insufficient indicator of malicious activity.
From here, we imported the domains that were associated with the spikes identified above into an Incident in ThreatConnect. Investigating each of these domains using ThreatConnect’s passive DNS capabilities, we identified two additional subdomains that were active during late 2015/early 2016, www.payment-ca.antyhem[.]com and e.xcellusbcbs[.]com. These subdomains clearly represent an attempt to target BCBS entities and potentially those individuals seeking to procure their services; however, no additional information was identified indicating that they hosted malicious files.
So while these registrations may not currently signify any specific malicious activity against BCBS, ThreatConnect’s Track function can be used to keep tabs of those domains or registrants that stood out most from this analysis. This would ultimately alert the user whenever additional information becomes available on the domains or when the individual registers additional domains. ThreatConnect will also identify whenever the hosting information for domains included in our incident change. This may help identify when a domain resolves to an new IP that is used in operations.
Conclusion
If leveraged on a daily basis, an organization can use the Domain Spinning Workbench to identify spoofed domains as they are registered and before they are used in attacks against them. From a tactical perspective, how an organization deals with such domains when they are identified depends entirely on that organization and its own motivations. However, there are variety of options in handling spoofed or typosquatted domains, including but not limited to: monitoring, blocking, sinkholing, takedowns, and purchasing. Each one of these would ultimately have different implications for the organization so it’s important to thoroughly consider such options when operationalizing this intelligence.
Organizations should leverage all intelligence available to them to identify and defend against their highest priority threats. Getting back to our Star Wars reference, our heroes aren’t in any danger until they are challenged on their knowledge of the Death Star. Had Empire personnel appropriately leveraged their technological advantage, biometric scanners or vocal comparison tests may have given them the intelligence necessary to challenge Luke and Han’s First Look Vulnerability exploit and ultimately quash the Rebellion.
Get More Information
If this is something that interests you and you’re a current ThreatConnect user, check-out the article from our Knowledge Base that will walk through all of these steps in greater detail. Click here to navigate to the ThreatConnect Knowledge Base.