Posted
The map I wish I had in the SOC
I remember a Thursday night at a previous SOC position in FinTech. The alert queue spiked during a credential stuffing incident, and our team had to scramble to keep up with the influx of alerts. We had a SIEM, a SOAR, and a handful of open-source IOCs we continuously retrieved via Google and other search engines. Each analyst grabbed a ticket and went hunting alone, starting their own process from scratch. We could isolate hosts, block domains, and re-image servers, but it was difficult to see the whole picture as we sorted through mountains of data and noise. Speed was the metric that mattered. I knew we were missing critical patterns, but I couldn’t see them or communicate what I thought we might be missing. We were moving fast, but we were still relatively blind.
Back then, our obstacle wasn’t just the attackers; it was the lack of structure. Our workflows and systems were not supporting each other, creating additional friction. We had no shared language. One teammate would call something a credential dump; another would describe a suspicious PowerShell script. Both were correct, but neither description connected to a consistent technique or pattern. Our triage lived in chat threads, ticket notes, and half-finished handoff docs. Behavior was rarely carried from one incident to the next. We spent hours digging through logs for clues we had already seen in previous incidents, but had no way to link them. Looking back, we weren’t struggling because the attacks were sophisticated; we were struggling because our system wasn’t leveraging pre-established standards and enrichment that would have focused our attention and communications.
Finding True North in Adversary Behavior
Now, I’m a different type of analyst. I research and help design products that help scale SOC and CTI teams via the Collective Analytic Layer (CAL) at Dataminr. CAL is a global intelligence engine with a mission to transform insights into action, embedded throughout ThreatConnect and Polarity to aid analysts throughout the CTI lifecycle. Now, I can see exactly what was missing in that SOC: A shared intelligence layer that would help our data speak the same language. We needed a living memory, something that linked indicators, patterns, and past activities together, rather than leaving us to reconstruct everything manually. These problems hit home for me as I watched MITRE ATT&CKcon 6.0. Red Canary highlighted that out of nearly 400 ATT&CK techniques, a small group of approximately 30 were “forever techniques” that account for the majority of detections. Novel attacks happen, but they’re rare. Most adversaries rely on the same behavioral building blocks repeatedly. That single insight reframed my years in the SOC. We could have been using established tools and practices to make our work so much easier.
ATT&CK as the Compass, CAL as the GPS
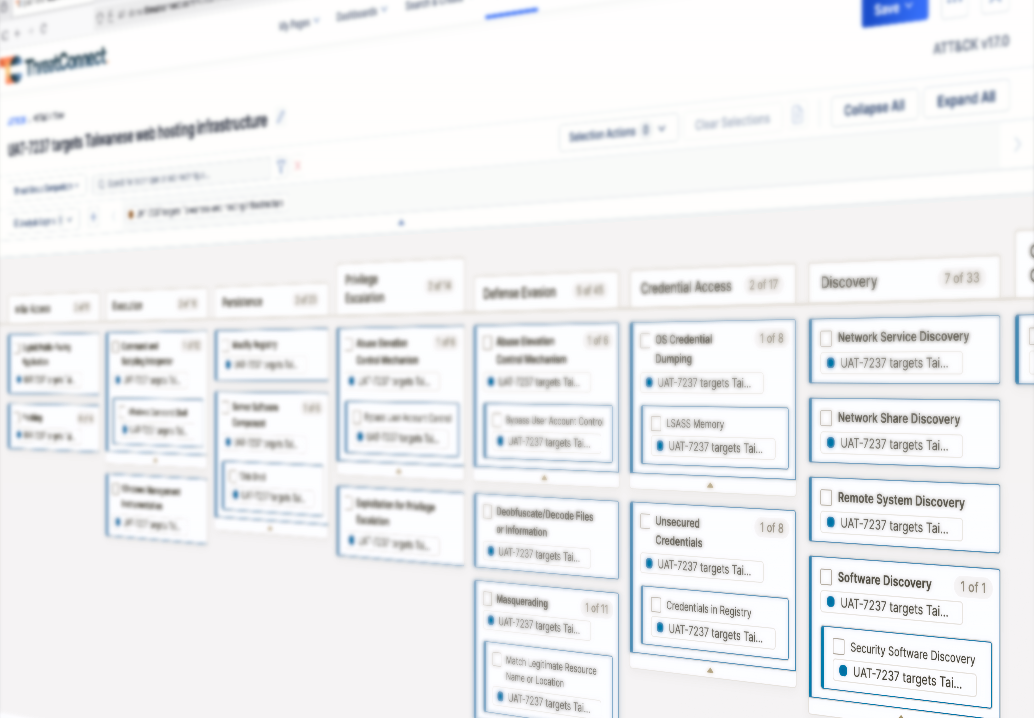
CAL has updated to leverage the latest MITRE ATT&CK Enterprise version 18. This version brings a more transparent structure for describing adversary behavior. Refining tactic categories and grounding updates in what defenders can actually observe across systems provides analysts with a more accurate shared language. The split of “Defense Evasion” into Stealth and Impair Defenses, for example, helps teams distinguish whether an adversary is hiding or actively degrading protections. This was something that used to blur together in my old SOC work. New sub-techniques, such as Python startup hooks, software discovery, and time-based evasion, continue the trend of modeling behaviors in a way that allows analysts to map back to telemetry, not just attacker intention reliably.
CAL takes that clarity and makes it operational. Instead of ATT&CK coverage living in slide decks or internal wikis, CAL applies it automatically to incoming news about breaches and attacks, connecting adversaries to behaviors, and placing isolated artifacts into a broader narrative. ThreatConnect enables quick visualization through ATT&CK visualization and adversary dashboards, which display trends and anomalies, providing a clear view of potential threats. Analysts can quickly apply ATT&CK tags to indicators, ensuring their communication remains aligned with the specific context of investigations.
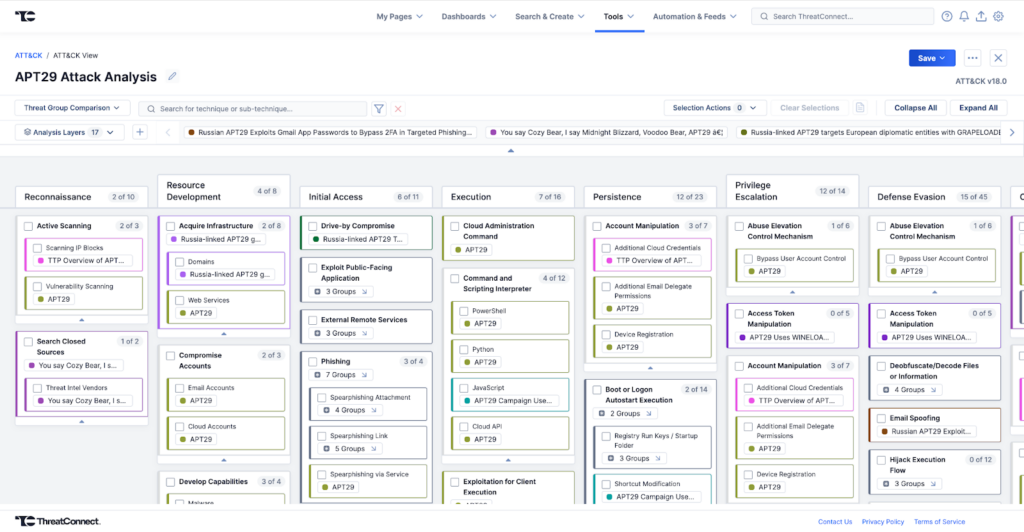
In Polarity, analysts can utilize the CAL Integration to quickly reference MITRE ATT&CK Techniques while reviewing reports or conducting investigations.
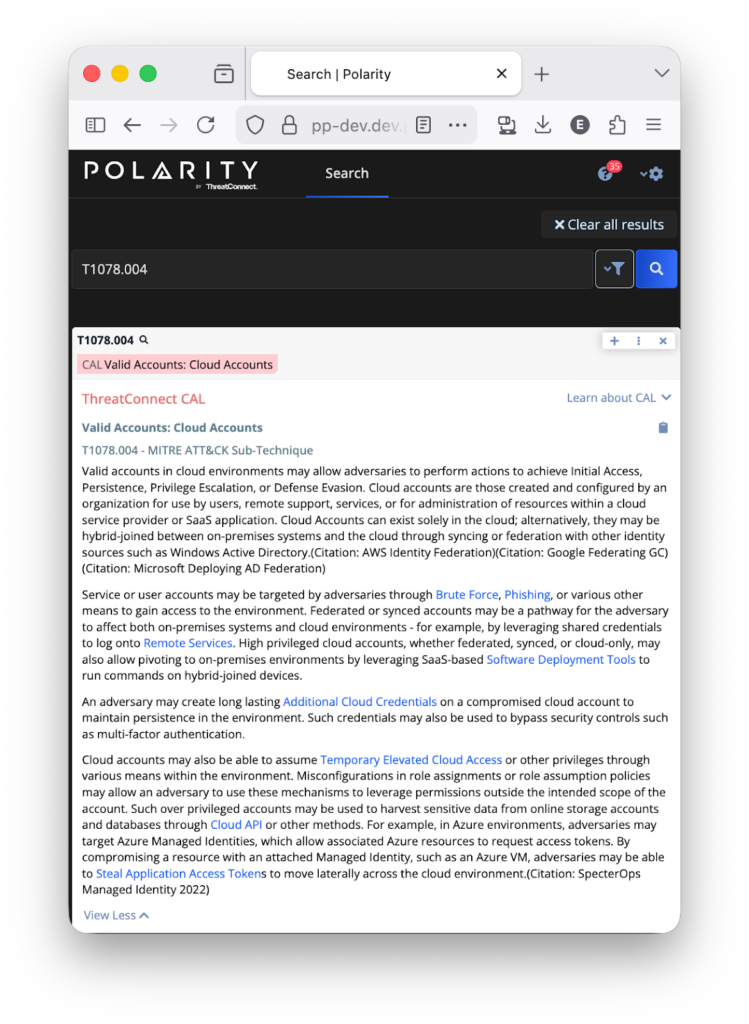
While ATT&CK Enterprise focuses on traditional systems, MITRE ATLAS focuses on AI-enabled ones. AI is increasingly embedded in automation, decision support, and internal workflows. That means adversaries now attempt to poison models, manipulate prompts, and exploit integration points in AI pipelines. ATLAS documents these real-world and simulated attacks, forming a knowledge base for AI red teaming and defensive planning. Importantly, ATLAS aligns with ATT&CK. This alignment enables CAL to correlate AI-targeted behaviors with traditional techniques, providing analysts with a unified understanding of both. With CAL’s latest 3.14 release, analysts will get more automation to help them extract and leverage ATLAS tactics and techniques.
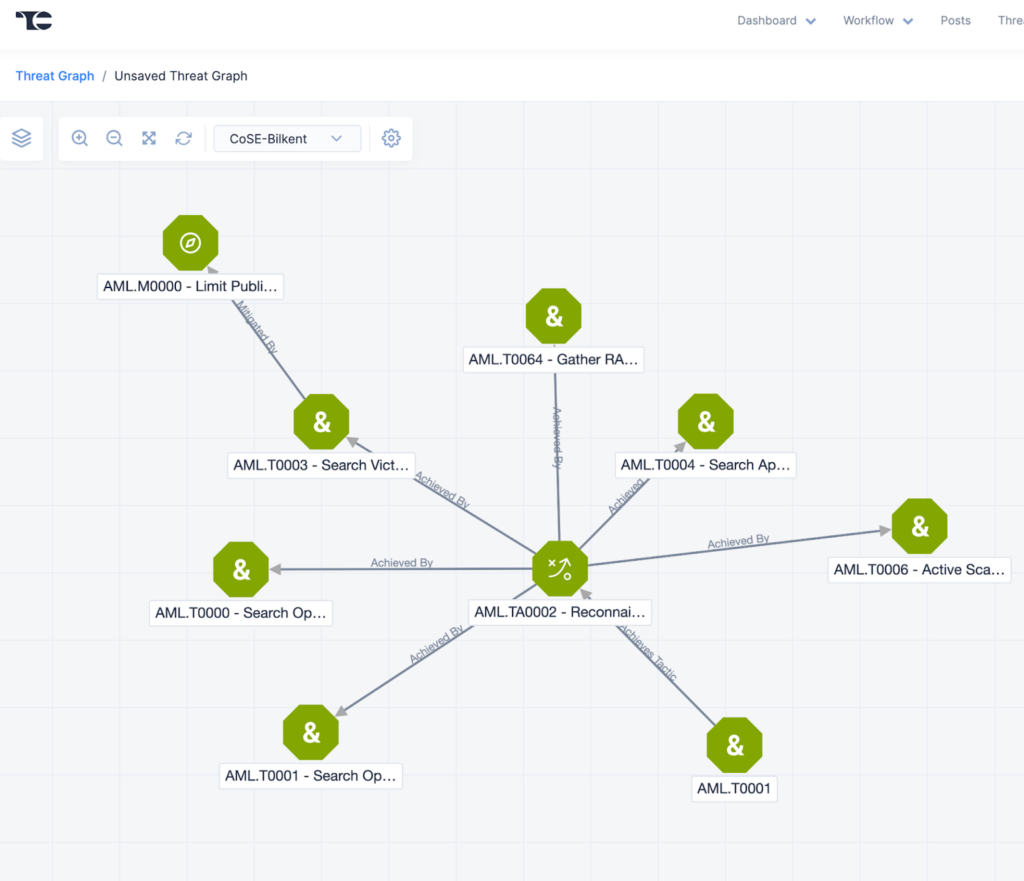
When Indicators Stopped Being Uncharted Territory
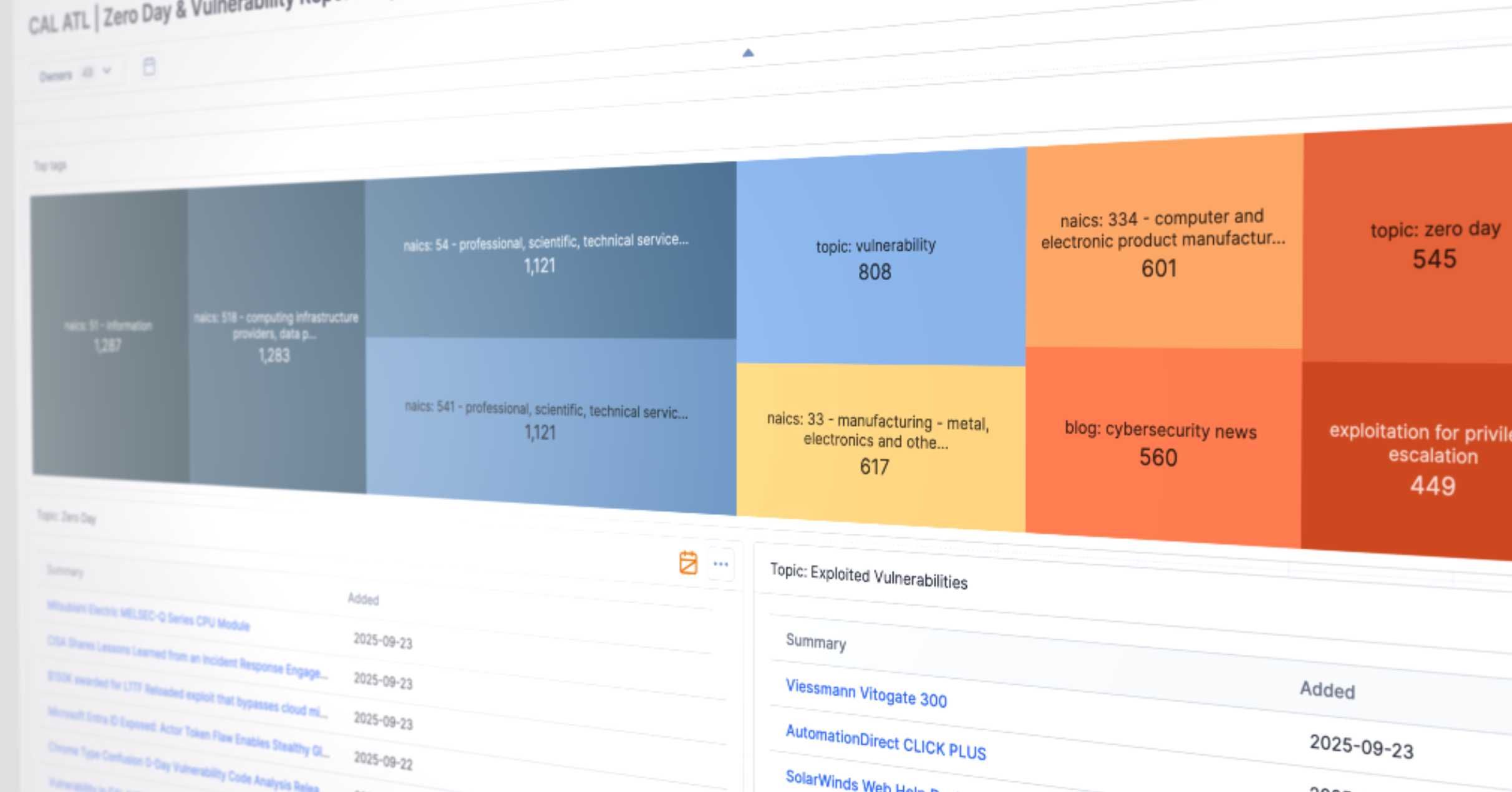
Indicator investigations in my old SOC felt like detective work of scattered feeds, inconsistent metadata, and hours spent deciding whether an IP, hash, or domain was worth our time. CAL Enrichment changes that by unifying intelligence from OSINT, proprietary feeds, analytics, and community signals into a single, unified view. Analysts instantly see observations, scoring, impressions, false positive reports, feed visibility, known-good status, classifiers, and behavioral metadata all in one place. CAL’s classifier ecosystem is powered by analytics, heuristics, and machine-learning models, adding another layer that labels indicators with threat-relevant categories to help analysts quickly understand behavior and intent. Even routine details, such as ASN mappings, cloud provider ranges, file metadata, or hash relationships, are automatically resolved, eliminating ambiguity and allowing analysts to focus on what matters.
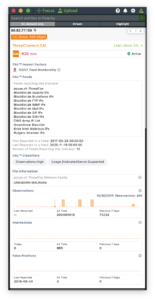
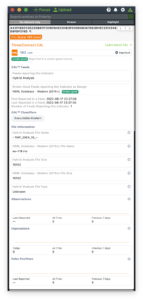
CAL Would Have Saved Us So Many Wrong Turns
Had we had access to CAL in ThreatConnect or Polarity, those long, chaotic nights would have been far more manageable. Alerts could be quickly mapped to ATT&CK techniques, linked to past incidents, enriched with global intelligence, and placed in broader behavioral patterns. Within five minutes, we would know not only what triggered it, but also why it mattered, whether the indicator had been seen elsewhere, its reputation, and what typically follows based on real-world behavior.
CAL removes the isolation we faced. Polarity lookups and ThreatConnect intel make research that once took hours available in seconds. Automated feed visibility, false-positive reporting, classifier context, and community signals provide instant clarity. Domains are instantly flagged for DGA patterns, hashes are linked to file families, and IPs are quickly identified as benign or suspicious. Behaviorally, scripts tied to T1059.003 no longer stand alone—CAL connects them to kill chain activity we previously missed. Shared technique tags align IR, CTI, and SOC workflows, while prevalence data highlights the behaviors that adversaries use most frequently.
Finally, a Map That Leads to Answers
This matters because defenders don’t just need more information; they need empowerment through reliable best practices. Looking back, much of the stress in my old SOC role came not from the threats themselves, but from the lack of structure around them. CAL provides the collective memory we were missing, while ATT&CK v18 and ATLAS supply a shared grammar that prepares teams for everything from today’s intrusion techniques to tomorrow’s AI-driven attacks. Together, embedded throughout ThreatConnect and Polarity, they transform SOC alerts from isolated events into meaningful stories, providing analysts with a more straightforward, more confident path from detection to action.