Posted
APT28 is a Russian state-sponsored threat actor with a long history of sophisticated cyber operations targeting governments, defense contractors, and critical infrastructure sectors across the globe. According to a CISA advisory released on May 21, 2025 this group has been exploiting known vulnerabilities in routers and other network devices to gain persistent access to sensitive environments.
APT28 is also known by aliases such as:
- Fancy Bear
- Forest Blizzard
- STRONTIUM, and
- Sofacy
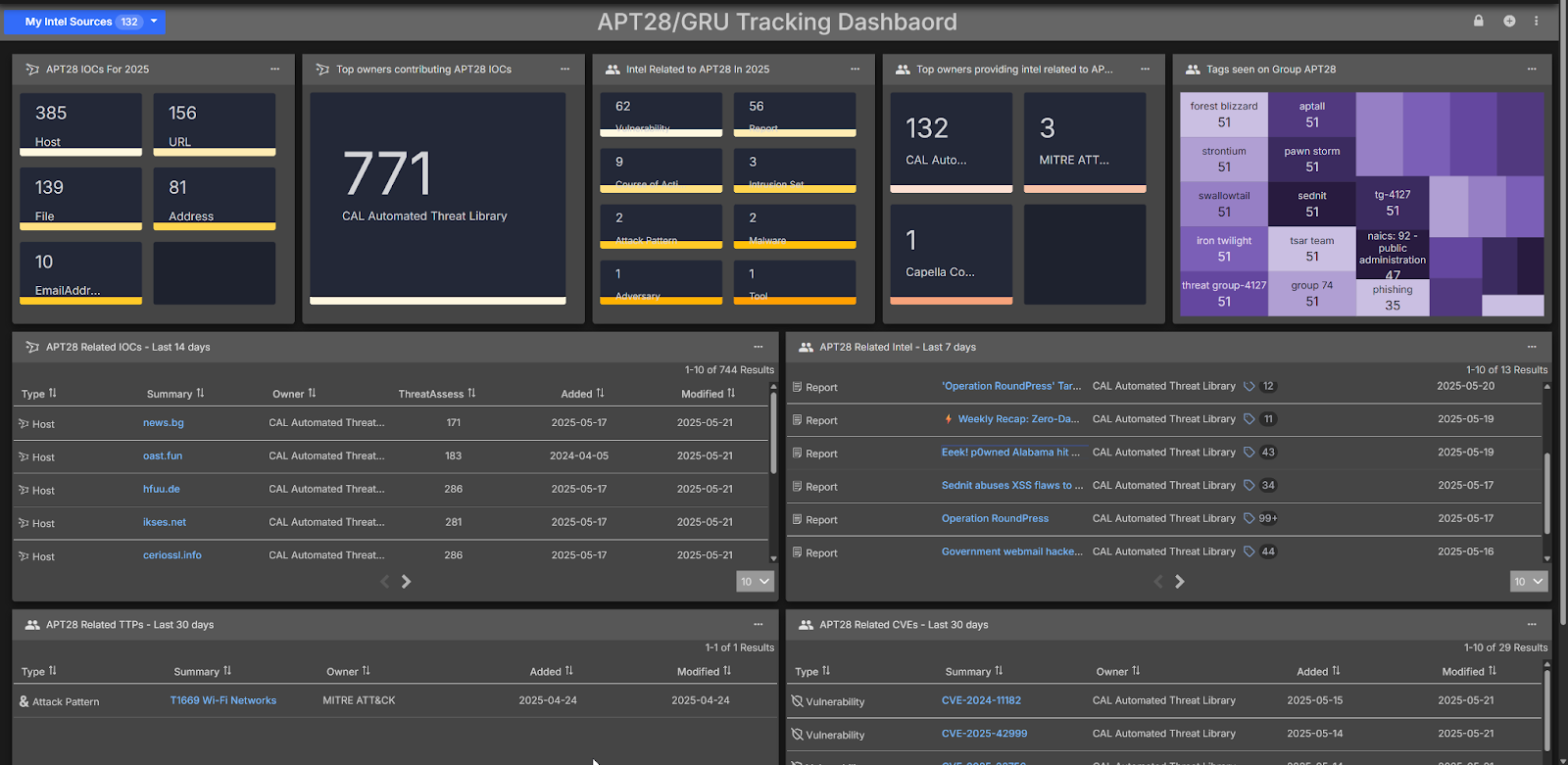
To support your organization in combating this persistent threat, ThreatConnect now offers an APT28 Threat Dashboard, purpose-built to deliver targeted insights, visibility, and response capabilities tailored to this high-profile actor.
Key Benefits:
- Centralized Intelligence: Compiles APT28-specific indicators of compromise (IOCs), tactics, techniques, and procedures (TTPs) from open-source intelligence, threat feeds, and internal telemetry.
- Real-Time Threat Tracking: Offers continuous updates on APT28’s attack infrastructure, victimology trends, and newly observed techniques.
- Incident Response Acceleration: Facilitates rapid threat triage and response by providing enriched intelligence and contextual analysis.
- Customizable Reporting & Visualization: Delivers interactive charts, campaign timelines, and executive-ready reports tailored to the APT28 threat landscape.
- For customers interconnected to defensive technologies — Automated Correlation: Utilizes ThreatConnect’s automation engine to correlate APT28-related IOCs with existing intelligence across adversary profiles, intrusion sets, and emerging threats, assisting in prioritization and risk mitigation.
By leveraging the APT28 Threat Dashboard, security teams can enhance their threat intelligence capabilities, reduce response times, and strengthen their organization’s resilience against ransomware attacks.
Lead Contributor – Emmet Wray , Director – Customer Success Engineering
To gain access to the APT28 Threat Dashboard, please reach out to your Customer Success team or email us at customersuccess@threatconnect.com.
Further Resources
For more detailed information and resources on VanHelsingRaaS, please refer to the following:
| Resource | Description | Link |
| Cybersecurity and Infrastructure Security Agency (CISA) | A U.S. federal agency under the Department of Homeland Security (DHS), it serves as the national coordinator for critical infrastructure security and resilience. | CISA Article |
| Microsoft | A global technology company headquartered in Redmond, Washington, is one of the world’s largest and most influential companies. | Microsoft Article |
| Federal Bureau of Investigation | The Federal Bureau of Investigation (FBI), National Security Agency (NSA), US Cyber Command, and international partners are releasing this joint Cybersecurity Advisory (CSA) to warn of Russian state-sponsored cyber actors’ use of compromised Ubiquiti EdgeRouters (EdgeRouters) to facilitate malicious cyber operations worldwide. | FBI Article |
We urge all organizations to remain vigilant and proactive in their cybersecurity efforts. By implementing these recommendations, you can significantly reduce your risk and protect your critical assets.