Posted
Today’s post continues an ongoing series on Polarity Integrations. Data tells a story, Polarity helps you see it with Augmented Reality overlaying contextual information from the applications you use every day, no glasses or goggles required. With over 100 powerful integrations, Polarity’s open-source Integrations Library arms you with the right data at the right time to make informed decisions and take action with speed. This example showcases our powerful integration with Rapid7’s AttackerKB.
What is Rapid7’s AttackerKB?
When a new vulnerability prompts discussion on Twitter or hits media outlets, it can be difficult for security teams to wade through all of the hype to determine risk and priority. How pervasive is the vulnerability? Is the expected shelf life long enough that it’s worth developing an exploit for? Is it worth dropping everything to patch or mitigate? Does an adversary or threat actor have a desire or motive to exploit the opportunity? Or is it actually… not useful or interesting?
Security researchers and hackers are almost always the first to shed light on the specific conditions and characteristics that make a vulnerability not just exploitable, but actually useful to attackers. AttackerKB was built to capture, highlight, and expand that knowledge for the whole security community.
What does the Polarity – AttackerKB integration do?
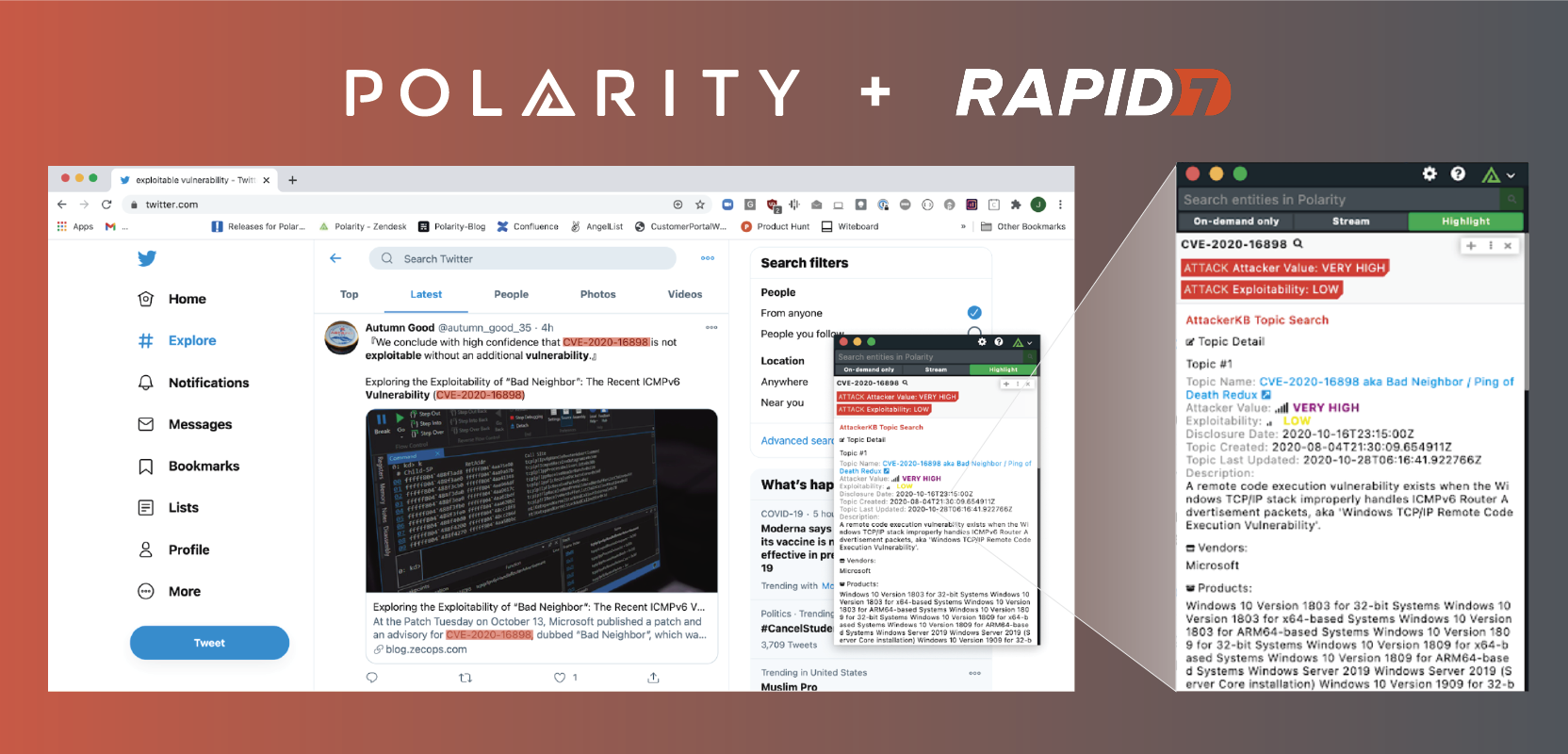
The Polarity- AttackerKB integration looks up CVE’s in AttackerKBs Topic API, immediately making the Polarity analyst aware of how an attacker views the vulnerability and the exploitability of the vulnerability. Then the analyst can pivot into more details to view information on the topics and learn what lead the AttackerKB community to those conclusions.
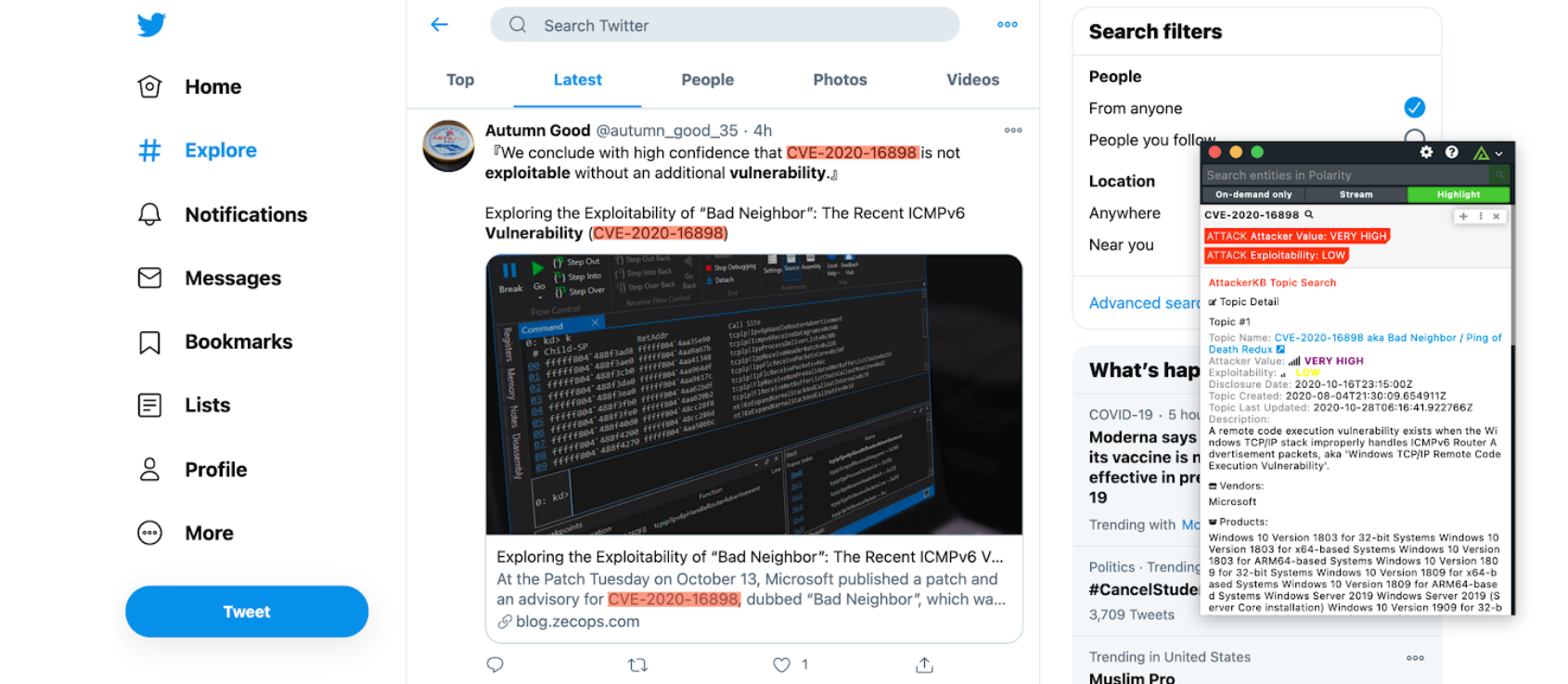
In this image, notice a CVE is highlighted in the screen on the left. On the right, you can see that Polarity’s computer vision recognized the text on screen, and in real-time while the analyst is working, it has provided contextual information for the highlighted CVE in the Overlay Window. This contextual information has been pulled from AttackerKB through the Polarity-AttackerKB Integration.
What Next?
Integrate with Polarity
Data tells a story, Polarity helps you see it with Augmented Reality. With more than 100 integrations, Polarity works well with the products our customers use every day. Connect your product to Polarity through our open-source integration program.