Posted
ThreatConnect has built 3 new Apps to work seamlessly with Amazon GuardDuty. Amazon GuardDuty is a threat detection service that continuously monitors for malicious activity and unauthorized behavior in your AWS accounts, workloads, and data stored in Amazon S3. With these Apps, any known IP addresses (good and bad) can be set up for monitoring and alerting. This integration consists of 3 different Apps – each with a different job:
- Playbook App – allows you to take actions on Threat Intel Sets and Findings
- Service App – allows you to ingest Findings from GuardDuty on a schedule and trigger a Playbook for each
- Job App – allows you to add and remove Indicators on Threat Intel Sets on a schedule
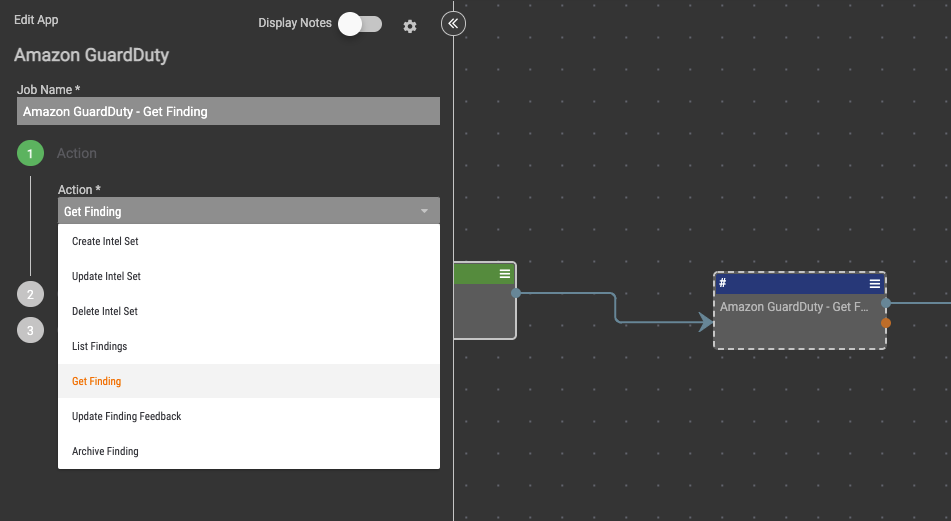 Amazon GuardDuty Playbook App
Amazon GuardDuty Playbook App
The following actions are available in the Playbook App:
- Create Intel Set – Creates a new Intel Set which the user will determine whether the Intel Set Type is Threat Intel Set or Trusted IP Set
- Update Intel Set – Updates the Intel Set specified by its Intel Set ID
- Delete Intel Set – Deletes a Threat Intel Set
- List Findings – Lists Amazon GuardDuty findings for a detector ID
- Get Finding – Describes Amazon GuardDuty findings specified by finding IDs
- Update Finding Feedback – Marks the specified GuardDuty findings as useful or not useful and optionally add comment
- Archive Finding – Archives a finding by its Threat Intel Set ID.
Together, ThreatConnect and Amazon GuardDuty help security teams monitor for malicious activity and protect their AWS accounts and data. If you’re a ThreatConnect customer, please reach out to your dedicated Customer Success Team for more information on deploying the Amazon GuardDuty Apps. If you’re not yet a customer and are interested in ThreatConnect and this integration, please contact us at sales@threatconnect.com.

