Posted
When it comes to using threat intelligence to aid in the investigation of alerts or phishing, it’s essential to have the right feeds (whether OSINT or paid). We often get asked, “can I just dump feeds right into my SOAR platform?” This is an evolution of a question that’s been going on for some time:
- Can’t I just dump IoCs into a spreadsheet?

- Can’t I just dump IoCs into my SIEM?
- Can’t I just dump IoCs into my SOAR?
Simply dumping IoCs into something and hoping they’ll provide answers when you need them is a recipe for disaster. It’s kind of like driving a car while suffering from narcolepsy and amnesia. Confused? Let’s explain.
Driving Without Threat Intelligence
Imagine you’re driving your car down a tidy suburban street. The sun is shining, the motor is humming, and you’re driving past a stop sign that’s partially overgrown by your neighbor’s prize-winning azaleas. The car in front of you has a bumper sticker that says “Student Driver – Stay Alert!” A jet passes low overhead. You’re on your way to the grocery store.
Just like when investigating an alert, staying on top of a network, or triaging a phish, you need situational awareness. Not just of what’s immediately in front of you, but what’s coming next and what came before.
 Unfortunately, you suffer from severe narcolepsy and amnesia. Every few seconds you fall asleep at the wheel and then wake up with no memory of where you are or what you’re doing.
Unfortunately, you suffer from severe narcolepsy and amnesia. Every few seconds you fall asleep at the wheel and then wake up with no memory of where you are or what you’re doing.
Don’t worry! You’re smart. So you look around. Your car is moving, you check the street signs to establish where you are, you check your GPS to see where you’re going (the grocery store), you see and recognize a stop sign and the azaleas.
This is what it’s like to receive an alert with no context and no insight: a world without threat intelligence management. All of that understanding needs to be created on the fly.
But then it happens again.
You wake up, only this time you don’t see the stop sign: you just see a metal pole reaching up into some azalea leaves. Was there a stop sign there? You can’t tell and can’t remember. You drive through. Cars around you slam on their brakes.
This is why it’s critical to know what came before. That email attachment might look innocuous based on what’s in front of you, but like the hidden stop sign there could be valuable insights buried in prior investigations (like maybe the file also appeared in conjunction with some known adversary infrastructure).
 Eventually, after an hour of near-misses and cognitively exhausting, constant readjustments to your surroundings, you finally make it to the grocery store.
Eventually, after an hour of near-misses and cognitively exhausting, constant readjustments to your surroundings, you finally make it to the grocery store.
Of course, that’s not how your brain works. You have persistence of memory and pattern recognition: you know the stop sign doesn’t disappear just because it goes behind a bush. You’re able to drive with an understanding of your place on the road and with an eye towards your destination.
Your Brain Doesn’t Do Feed Management
That brings us to our original statement: driving with narcolepsy and amnesia is exactly what it’s like to investigate an alert or a phishing attempt without proper threat intelligence management. If you constantly need to pull in context for every observable and treat every alert like you’re seeing it for the first time, it will take you forever to get where you’re going and you’ll put others at risk on your way there. Every indicator is like the stop sign: sometimes it’s obscured, sometimes there’s a clear course of action, but the only way to know what to do is to have that context.
Having proper threat intel management is like knowing where you are and where you’re going. You don’t need to recognize the stop sign hidden in the bushes: your brain saw it, knew it was there, and you can take appropriate action as you proceed. If you spend too much time on irrelevant information, it becomes a distraction.
Dumping feeds somewhere isn’t the answer, either. It’s total sensory overload: if you’re driving, you need to know what’s relevant (signage, other cars, pedestrians). You don’t need to know how many leaves are on the azalea bush, or what that bumper sticker says, or where that airplane overhead is going. None of that is relevant to your mission as hand: your drive and your safety.
On Relevancy
This idea of relevancy brings us to another important point when it comes to comparing and contrasting threat intel management with feed management.
The thing about relevancy is that it’s very personal and it can change constantly; what’s relevant to you could be completely irrelevant to someone else. Or what’s relevant to you today could be low in your hierarchy of care tomorrow. Feed management doesn’t support the idea of ever-changing relevancy and ensuring you have the intelligence that matters the most to your mission at hand in front of you.
Going back to the driving analogy: having intelligence about your drive is important, but the specific intel is important at different times. If you’re parked in the garage, the fact that your garage door is down matters a heck of a lot more to you when you fire up your car to ensure you don’t make a very expensive mistake. It may not be so important to you when you’re 2 hours away from home going 65 mph on the highway and the thing you’re thinking about the most is which exit you should take and what the speed limit is considering you just passed a police officer.
Let’s take driving out of this and get into why this difference is so important when considering bringing intelligence feeds or other data sources into your SOAR.
Feed Management vs Threat Intel Management
Moving beyond metaphor and onto brass tacks, the differences can be summed up in four key areas:
- Data Structure
- Ongoing Enrichment
- Native Intelligence Creation
- Customization
Let’s dig into each with regards to ‘feed management’ and ‘threat intel management’:
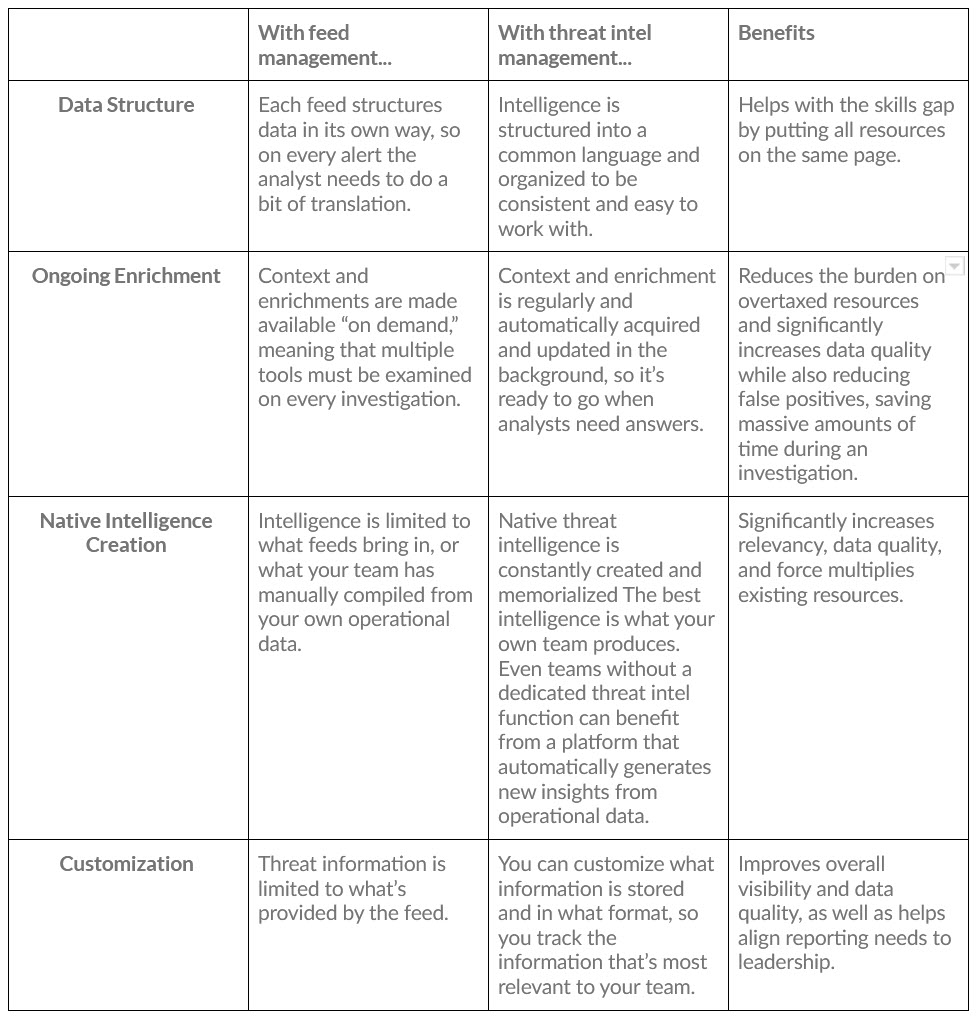
In a nutshell, the biggest difference between feed management and threat intel management is this:
When an analyst encounters a potential threat, feed management requires contextual understanding of the feed and further investigation via enrichment tools of every threat. With threat intel management, that context is provided by the platform itself. A SOAR with proper threat intel management should also help you uncover new native intelligence.
This significantly increases the quality of data, helps you maximize what you get from your tools, saves time, and provides analysts with additional direction during an investigation, ultimately decreasing frustration across the board.
In other words, you can drive to the grocery store without needing to relearn how to drive every few feet (or meters)!
To learn more about ThreatConnect and how we’re the only SOAR platform with native threat management capabilities, please contact sales@threatconnect.com.
