Posted
Howdy, and welcome to the ThreatConnect Research Roundup, a collection of recent findings by our Research Team and items from open source publications that have resulted in Observations of related indicators across ThreatConnect’s CAL™ (Collective Analytics Layer).
Note: Viewing the pages linked in this blog post requires a ThreatConnect account.
In this edition, we cover:
- Strontium
- APT34
- RedDelta PlugX
- Emotet
Roundup Highlight: Microsoft Strontium Sinkhole Domain Sibling
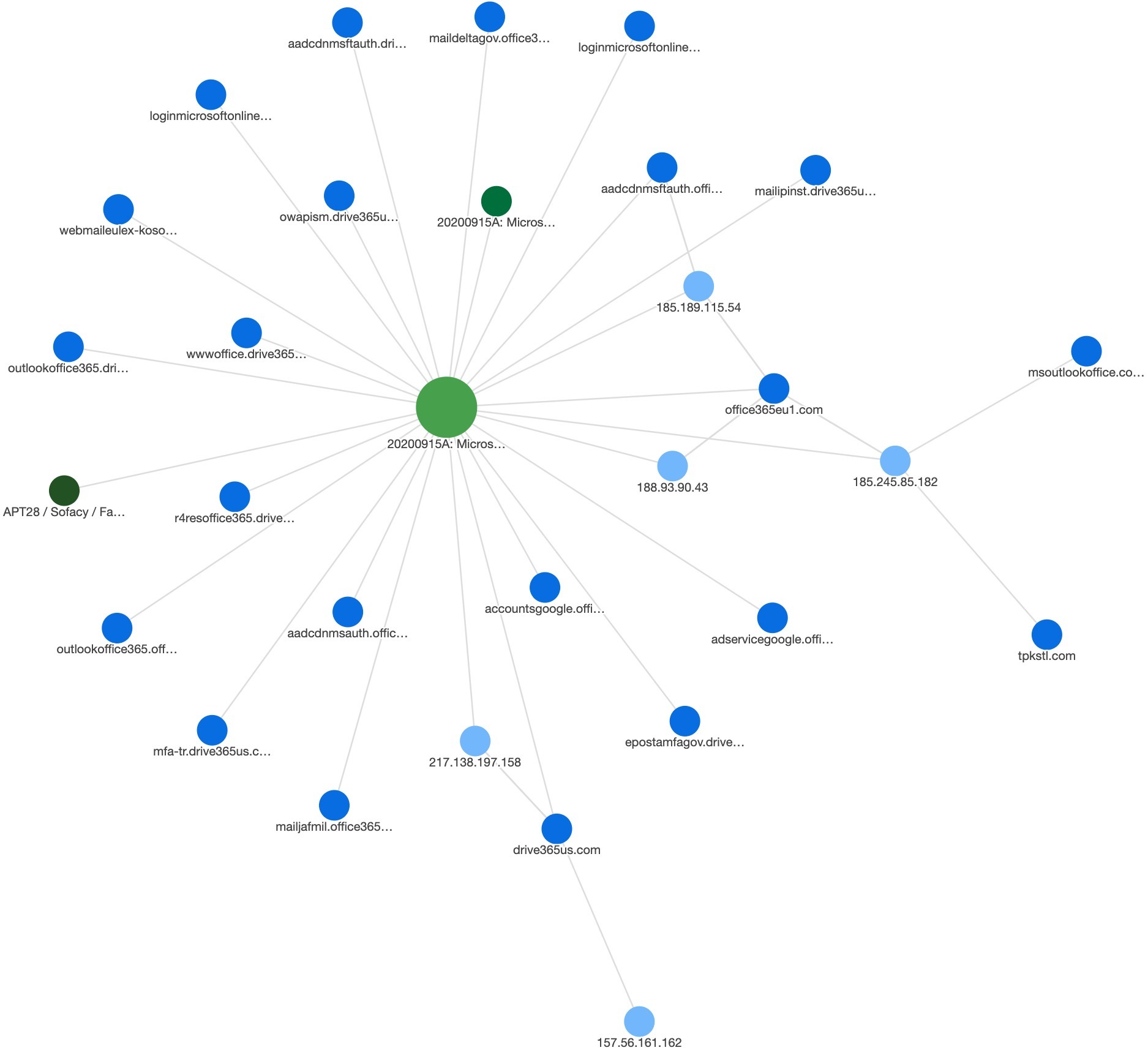
20200915A: Microsoft Strontium Sinkhole Domain Sibling
Our highlight in this Roundup in Incident 20200915A: Microsoft Strontium Sinkhole Domain Sibling. ThreatConnect Research reviewed the domain drive365us[.]com — a domain registered through BAcloud on June 10 2020 and previously hosted at 217.138.197[.]158 — which began resolving to a Microsoft sinkhole previously used for Strontium / Fancy Bear / APT28 infrastructure in mid September 2020.
On June 15 2020, a Let’s Encrypt SSL certificate was created for drive365us[.]com and wildcard subdomains. The following subdomains have been observed for the domain and may indicate that government organizations in Turkey and Kosovo were targeted with this infrastructure or otherwise spoofed in the operations:
aadcdnmsftauth.drive365us[.]com
epostamfagov.drive365us[.]com
loginmicrosoftonline.drive365us[.]com
mailipinst.drive365us[.]com
mfa-tr.drive365us[.]com
outlookoffice365.drive365us[.]com
owapism.drive365us[.]com
r4resoffice365.drive365us[.]com
webmaileulex-kosovo.drive365us[.]com
wwwoffice.drive365us[.]com
It’s important to note that since a wildcard subdomain SSL certificate was in use, the identified subdomain resolution may not have been intentionally created by the actor and instead the result of a third party’s browsing or scanning.
Searching other domains for some of the possibly unique subdomain string “aadcdnmsftauth”, we identified another domain probably related to Strontium — office365eu1[.]com. This domain was registered through Njalla on December 3 2019 and is currently hosted at 185.189.115[.]54, with previous resolutions at 188.93.90[.]43 and 185.245.85[.]182. Identified subdomains include the following and may indicate additional targets in Georgia and Jordan:
aadcdnmsauth.office365eu1[.]com
aadcdnmsftauth.office365eu1[.]com
accountsgoogle.office365eu1[.]com
adservicegoogle.office365eu1[.]com
loginmicrosoftonline.office365eu1[.]com
maildeltagov.office365eu1[.]com
mailjafmil.office365eu1[.]com
outlookoffice365.office365eu1[.]com
Similar to drive365us[.]com, Let’s Encrypt SSL certificates for wildcard subdomains have been created for office365eu1[.]com, so the aforementioned subdomains are not definitively indicative of the actor’s operations.
ThreatConnect Research Team Intelligence: Items recently created or updated in the ThreatConnect Common Community by our Research Team.
- 20200913A: Possible APT34 Domains ThreatConnect Research identified possible APT34 domains registered in September 2020 that have non-definitive WHOIS consistencies with previously identified APT34 infrastructure.
- 20200915B: File Matching YARA Rule Associated to RedDelta PlugX ThreatConnect Research identified a RedDelta PlugX binary and extracted Command and Control locations from the embedded configuration.
- 20200909B: File Matching YARA Rule Associated to RedDelta PlugX ThreatConnect Research identified a RedDelta PlugX binary and extracted Command and Control locations from the embedded configuration.
Technical Blogs and Reports Incidents with Active and Observed Indicators: Incidents associated to one or more Indicators with an Active status and at least one global Observation across the ThreatConnect community. These analytics are provided by ThreatConnect’s CAL™ (Collective Analytics Layer).
- Emotet C2 Deltas from 2020/09/16 as of 06:00EDT or 10:00UTC (Source: https://paste.cryptolaemus.com/emotet/2020/09/16/emotet-C2-Deltas-1000-0600_09-16-20.html)
- Daily Emotet IoCs and Notes for 09/14/20 (Source: https://paste.cryptolaemus.com/emotet/2020/09/14/emotet-malware-IoCs_09-14-20.html)
- Threat Roundup for September 4 to September 11 (Source: https://blog.talosintelligence.com/2020/09/threat-roundup-0904-0911.html)
- Emotet C2 Deltas from 2020/09/11 as of 16:00EDT or 20:00UTC (Source: https://paste.cryptolaemus.com/emotet/2020/09/11/emotet-C2-Deltas-2000-1600_09-11-20.html)
To receive ThreatConnect notifications about any of the above, remember to check the “Follow Item” box on that item’s Details page.
