Posted
ThreatConnect has partnered with Okta, a leader in the Identity and Access Management (IAM) space, to deliver a Playbook App for joint customers. This App allows you to automate processes during an internal security investigation when it’s critical to quickly get user information or suspend users involved with a security incident. Let’s dive in.
The following use cases are made possible with ThreatConnect Playbooks:
- Get User account information, including Groups and Applications the user has access to. This information can be used for making automated decisions about the next steps to take in the investigation as well as helping you to have all the information you need without having to collect it manually.
- During a security investigation, it’s often necessary to suspend a user’s account for some time while the investigation takes place, and you can confirm that the account is not compromised. This action can be automated as part of a Workflow or Playbook. Later in the process, the account can be Unsuspended, and the Password can be reset automatically.
This Playbook App contains the following actions:
- Get User
- Get User Applications
- Get User Groups
- Reset Password
- Suspend User
- Unsuspend Use
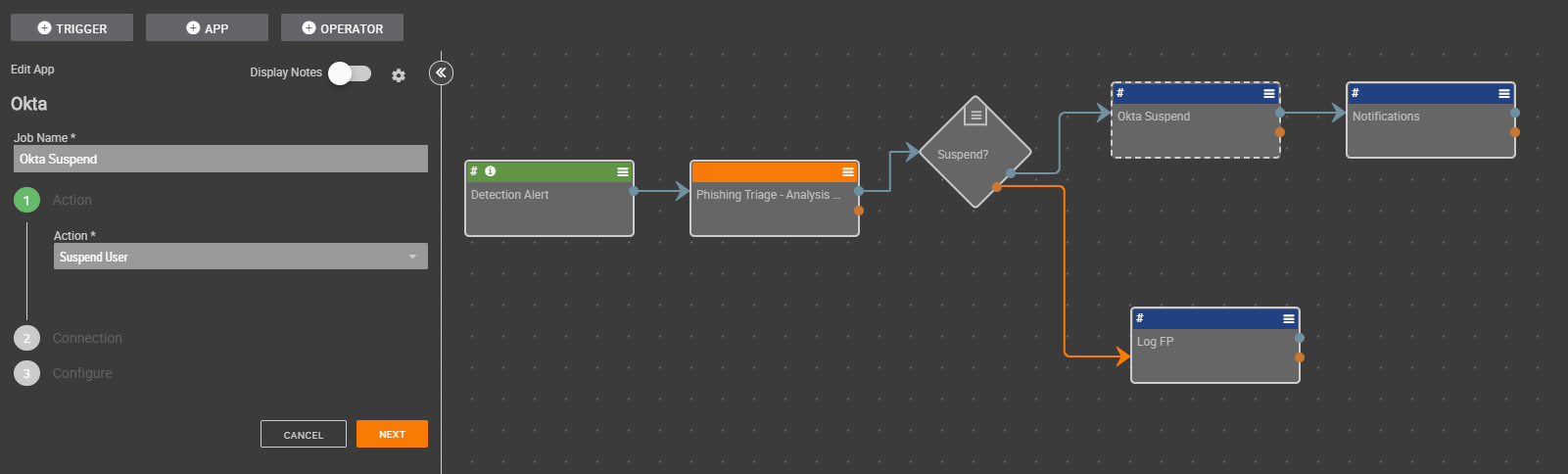
Together, ThreatConnect and Okta help you to automate IAM actions, saving you time and bandwidth during an internal security investigation. If you’re a ThreatConnect customer, please reach out to your dedicated Customer Success Team for more information on utilizing the Okta Playbook App. If you’re not yet a customer and are interested in ThreatConnect and this integration, contact us at sales@threatconnect.com.
