Posted
This Playbook streamlines a process for reporting to a threat intel team without asking the reporting party to rework any existing infrastructure, or go too far out of their way to make findings accessible. This also works regardless of who the reporting party is; whether that is a SOC, customer, or industry partner.
The most viable source of intelligence for any organization is going to be based upon intelligence driven by other teams coexisting with the same workspace. This process is extremely important as it drives the communication across all security team and personnel. This type of internal intelligence along with premium and OSINT feeds provides a completed picture for a threat intelligence analyst.
While many teams have an idea of what applications and appliances they would like to integrate with, only extremely mature threat intel teams have working processes for how communication is received and how confirmation is sent to reporting parties. Even mature teams have some manual steps within a process that this Playbook would help automate.
Overall this Playbook provides a simple and professional way or gathering data reported from invested parties outside of the threat intel team, making collaboration a simple and easy task. The Playbook:
- Saves time by automating the process
- Provides a uniform process for parties reporting to the threat intel team
- Gives the threat intel team a uniform structure in which to work new reports
How It Works
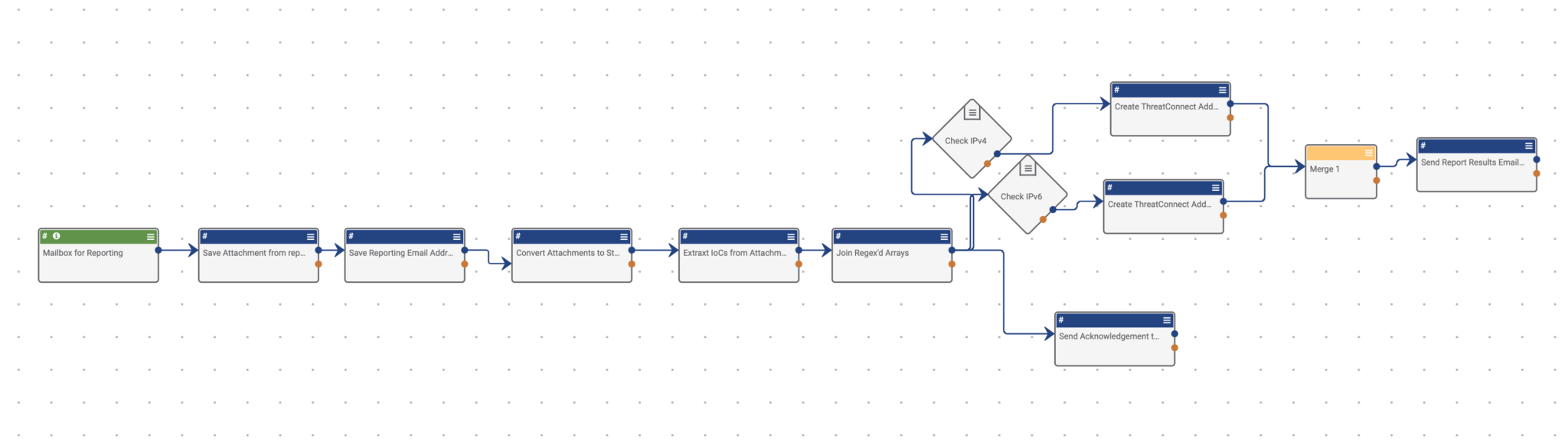
This Playbook is triggered when an email is sent to a mailbox created within ThreatConnect. This mailbox can be added to an existing distribution list that is used for reporting data to the threat intel team.
An email with an attached report is sent to the mailbox setup within the trigger of the playbook. This can also be done with the body of an email through minimal alterations with the Playbook.
This Playbook does not directly use any integrations; However, you can use the integrations to enrich data after the Playbook is run.
After receiving the email, the Playbook uses the “Create ThreatConnect Document” app to save the attachment as a Document to maintain a historical record of the report. Then the “Create ThreatConnect Attribute” app is used to provide the from field of the email header as an attribute to maintain a record of whom sent the report. Following this, we convert the binary to a string (Binary to String app), then use the “Regex Extract app” to extract IOCs. For this, the regex queries found for all indicator types can be found under the system settings.
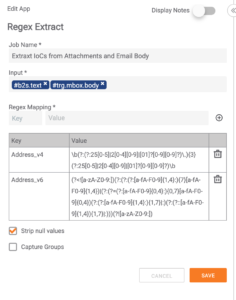
Once the IOCs have been extracted into a string array, the playbook converts the string arrays to strings using the “join Array app”. Now that the IOCs are in strings — respective to their IOC type — a system of “If/Else” statements are constructed to validate the IOC outputs consist of data. The if/else statements only pass logic where the IOC strings only do not equal “null”. This process allows any IOC types that do not exist within the original report to drop and take no further system resources.
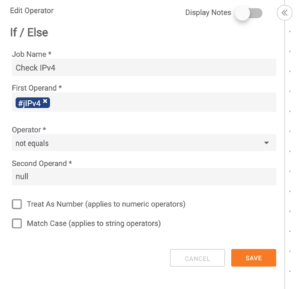
Concurrently with this process, the Playbook sends a reply back to the original reporting email acknowledging the email was received. Once the logic has passed the if/else statements, proving the IOC strings consist of data, the original string arrays from the Regex Extract app are used to create ThreatConnect Indicators, respective of their IOC types. Once the IOCs have been created, the logic flows into a merge statement with all the string arrays of the create (indicator type) apps’ outputs and feeds this output into a send email app to alert the reporting party of the Indicators being created within ThreatConnect.