Posted
Learn How to Research Ransomware in ThreatConnect
We recently recorded a video to show what members of our Research Team do on a daily basis within the ThreatConnect platform to perform cyber threat analysis, research threats, conduct investigations, create new intelligence, and more. Our hope is that this video will help to educate viewers on the different processes and tactics that our team uses so that they can implement them and better protect their own organizations.
This video covers two main topics:
- How to research Ransomware in ThreatConnect
- How to brief others on the threats most relevant to your organization
How to Research Ransomware
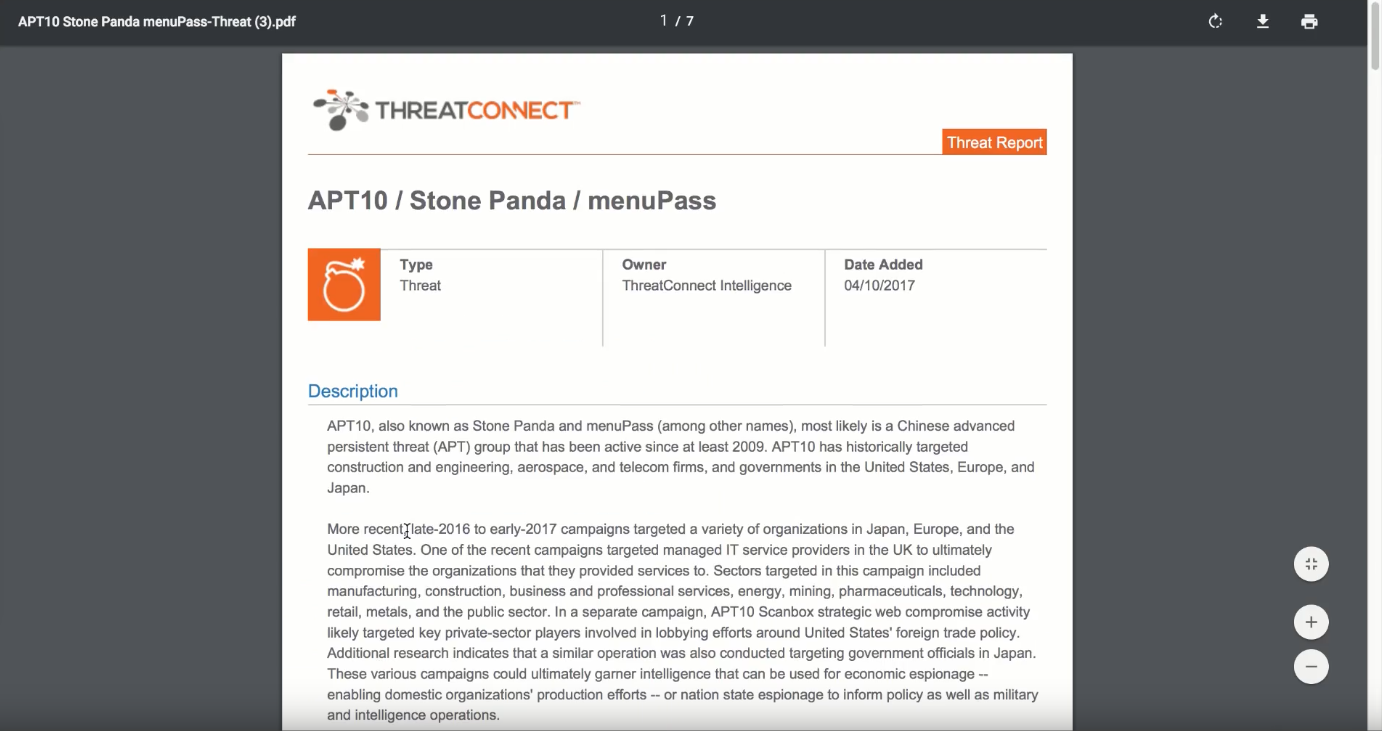
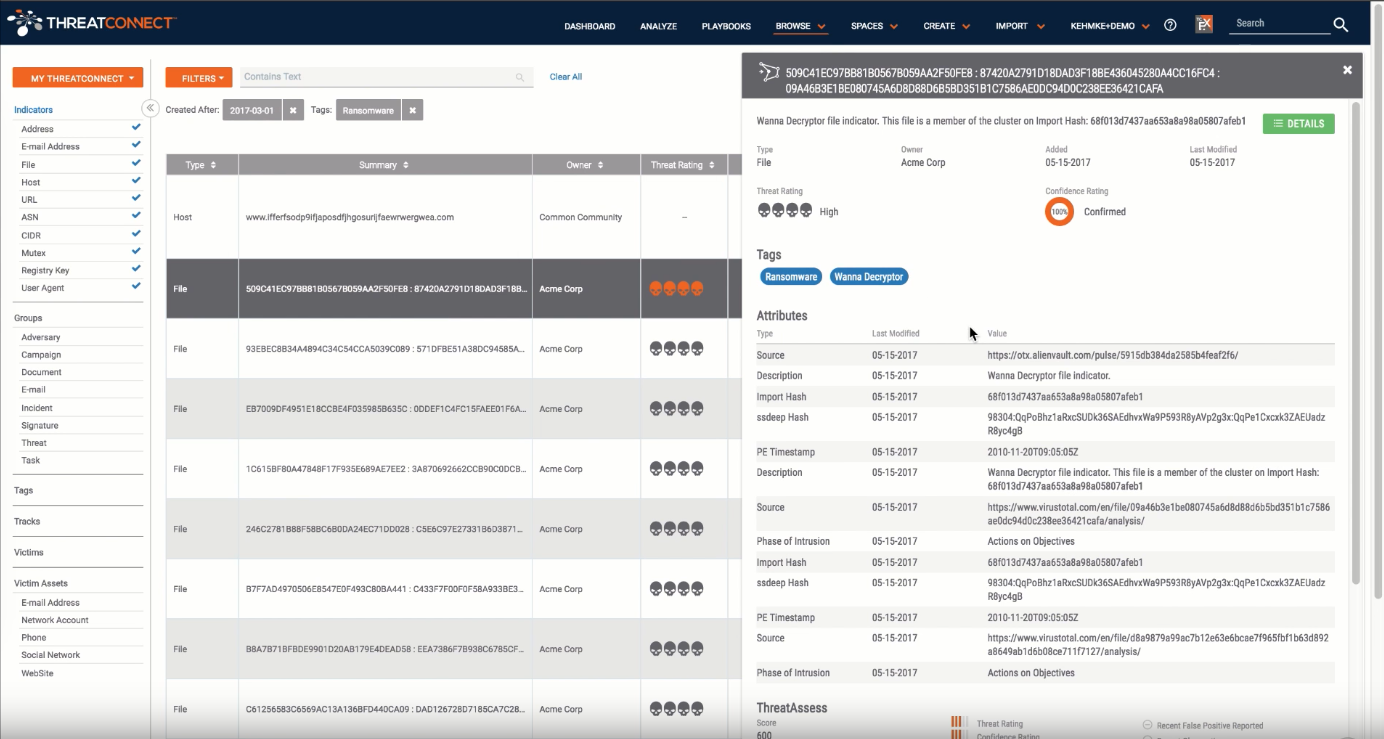
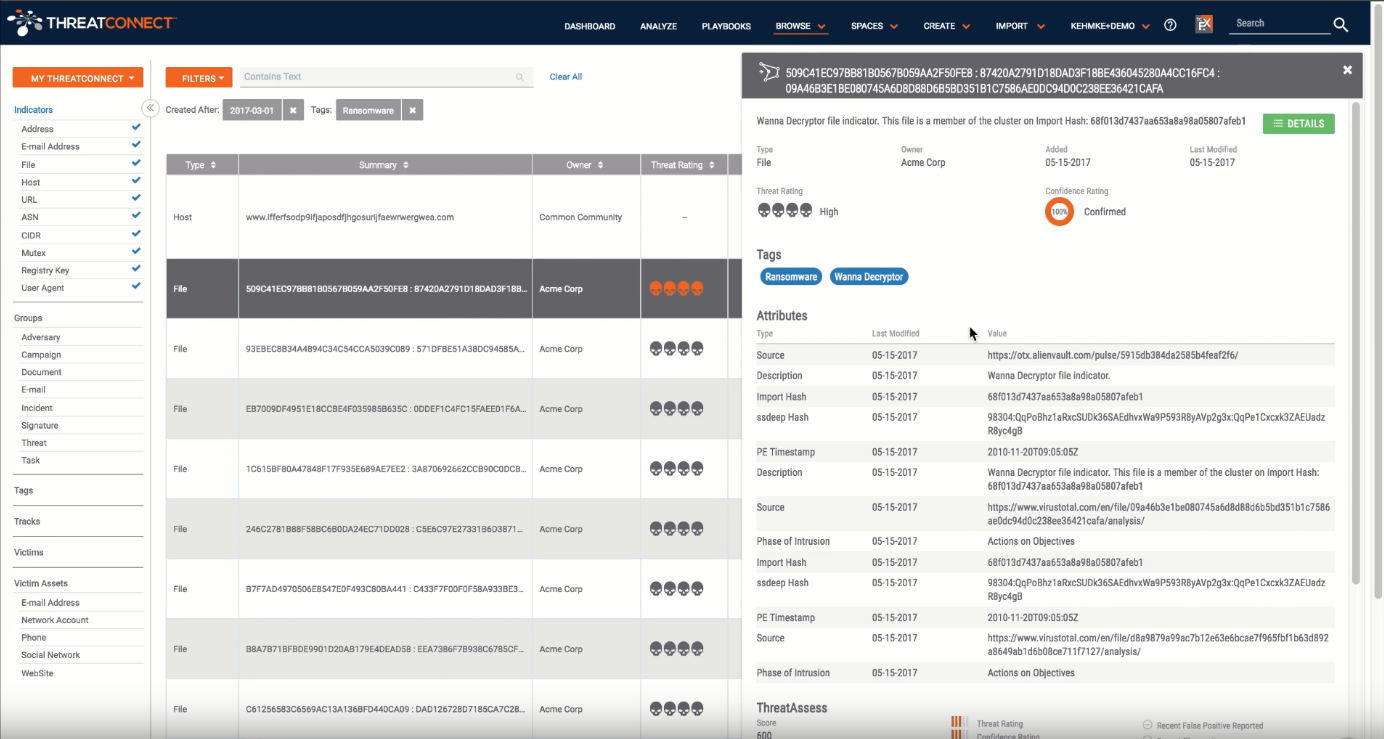
Ransomware has been the talk of the town since the recent WannaCry ransomware infections broke out earlier this month which makes it top of mind for a lot of organizations. In this video you can follow along with one of our Senior Threat Intelligence Researchers as he details how to search for recent findings in the ThreatConnect platform that have been identified as ransomware. You will learn how to quickly conduct advanced searches and view detailed information about each indicator. The more information that is available to you, the more quickly you can determine whether an indicator warrants further investigation or whether it is relevant for your particular organization.
How to Brief Others on the Threats Most Relevant to your Organization
From a strategic perspective, it is important to be able to quickly and effectively brief others in your organization on the threats that are the most relevant to you. Say you are most interested in Chinese nation-state threat actors that commonly use spearphishing and ransomware tactics to target organizations in the banking and finance industries. All of this information can be searched for in the Browse function of ThreatConnect making it easy for you to find the information that is the most pertinent to your organization. Anything of interest that you find can be packaged up in an easily digestible PDF report for sharing.