Posted
How any size retailer can get started with ThreatConnect to gain context about threats
Are you a retailer? Just getting started with threat intelligence? Then you are going to want to read this — our first post in a series directed toward specific business verticals.
Retail is a vast ecosystem that connects merchants to suppliers, manufacturers, and distributors; and financial processing systems to banks through processors. This ecosystem creates a diverse landscape that requires visibility across many systems and exposes them to a wide range of threats (R-CISC, 2016). These threats range from point-of-sale attacks (point-of-sale malware, e-commerce payment systems) to crimeware (ransomware, distributed denial of service). According to Verizon, in 2016 retailers were most affected by web-app attacks, point-of-sale intrusions, and payment skimmers. What does this show? While these industry threats continue to be advanced and persistent, adversaries are consistent in leveraging similar tactics, techniques, and procedures (TTPs).

Outside of joining retail specific collaboration communities like the Retail Cybersecurity Intelligence Sharing Center (R-CISC) and the National Retail Federation Industry Sharing and Analysis Organization (NRF ISAO), what else can a retailer do to get more data and context on threats – both seen and unseen? Enter ThreatConnect. Whether a merchant the size of Jurassic World, Los Pollos Hermanos, or Bluth’s Banana Stand, ThreatConnect provides an easy way of answering questions regarding threats and the context around them. In order to follow along with us, you’ll need access to ThreatConnect.
Getting Started with Threat Intelligence: How to Find Out What’s Relevant to You
Browse
The best way to find retail-specific data is to look at threat intelligence sources that are already in the ThreatConnect Platform. Once you click ‘Browse’, you can choose which data sources or communities interest you.You can choose to look at specific indicators (host, address, file, etc.) or group types (campaign, incident, threat, etc.). When you see something of interest, click on the indicator or group to see a quick overview of the details and if is worth investigating. If the data proves helpful, you can export the indicators, with the associated context, into a CSV file to be added to existing defensive solutions.
Recommended Sources:
- ThreatConnect Intelligence Source*
- R-CISC Source*
- Ransomware feeds
- Abuse.ch Ransomeware Tracker
- Malware Domain Blocklist
*Please note that these sources are only available in the ThreatConnect Product Suite. To get access to these sources, contact us here.
Tags
Now you know how to look for data in the ThreatConnect Platform. Still feel like you don’t know where to get started? Here’s another way: retail-specific tags. Tags are how ThreatConnect categorizes data in the Platform. These tags range from specific industries and nation-states to CVEs and specific threats. As ThreatConnect users, including our own Research Team, hunt, analyze, and create threat intelligence in the Platform, specific tags are applied to enable easy searching. You can also search for Tags using the ThreatConnect Browse Screen.
Recommended Tags:
Once you search for retail-related tags, you can choose to view indicators or incidents that have had the tag added. We recommend looking at incidents, where you can easily dive in to see how indicators relate to each other, adversary attack patterns, and more.
Recommended Incidents:
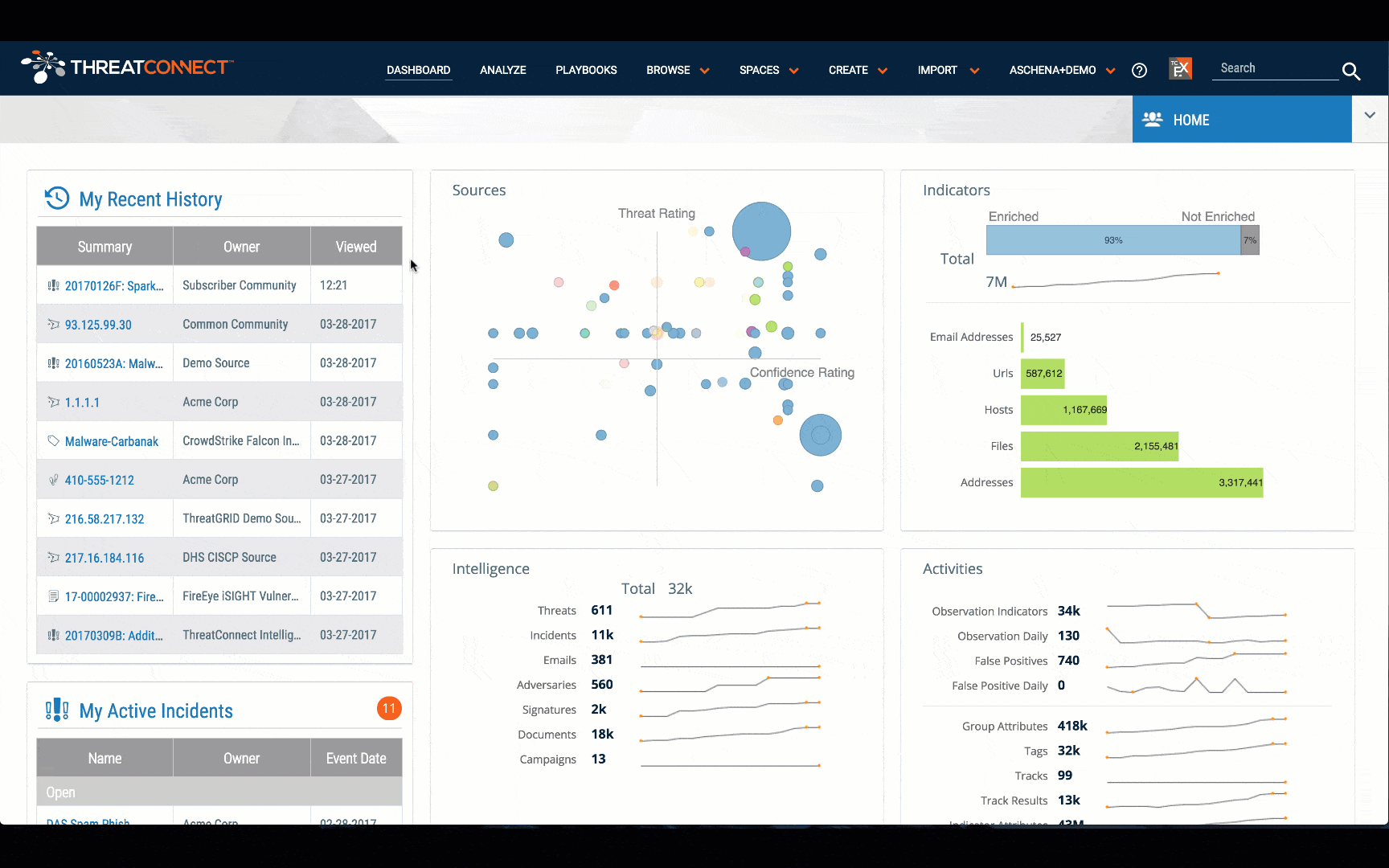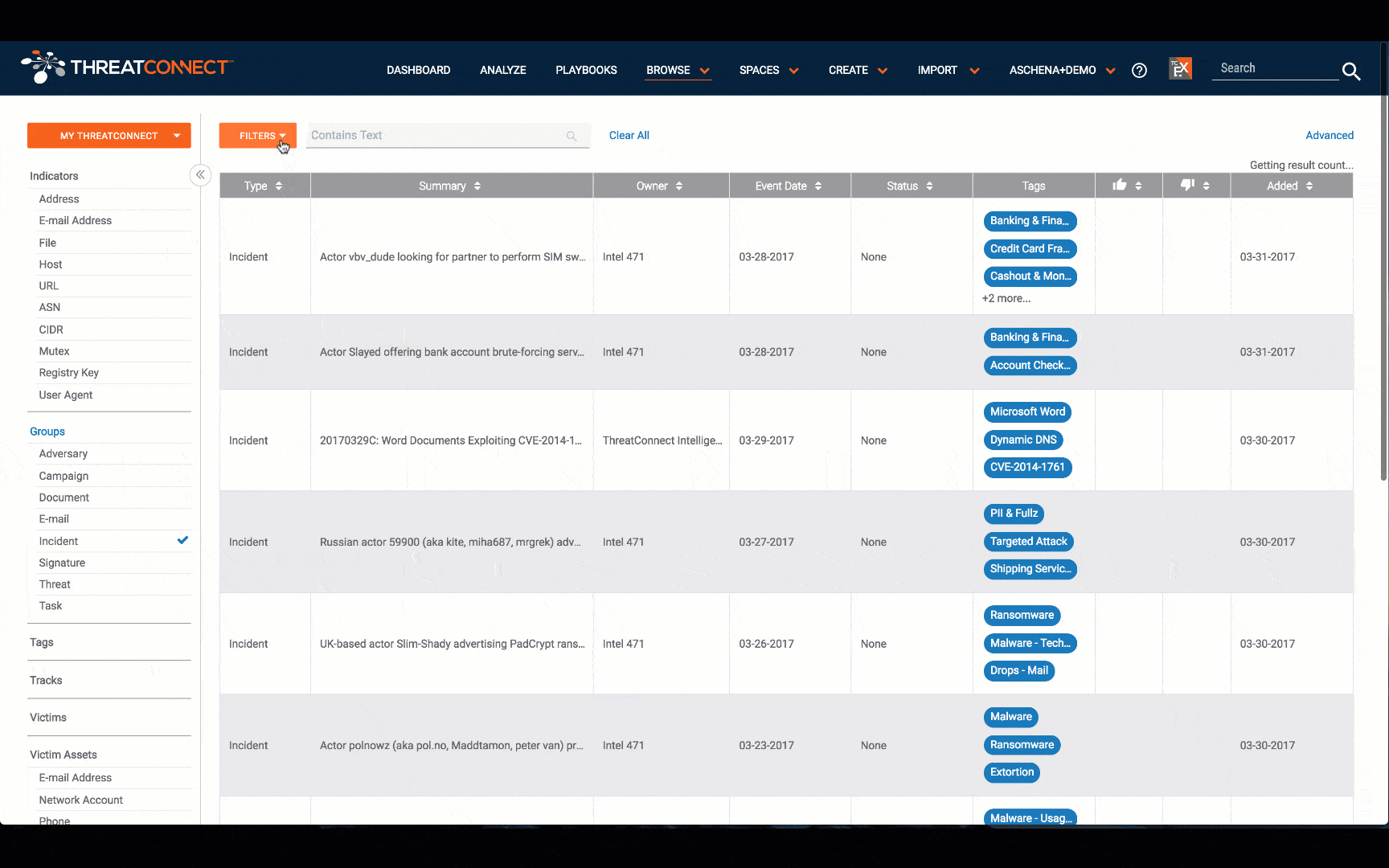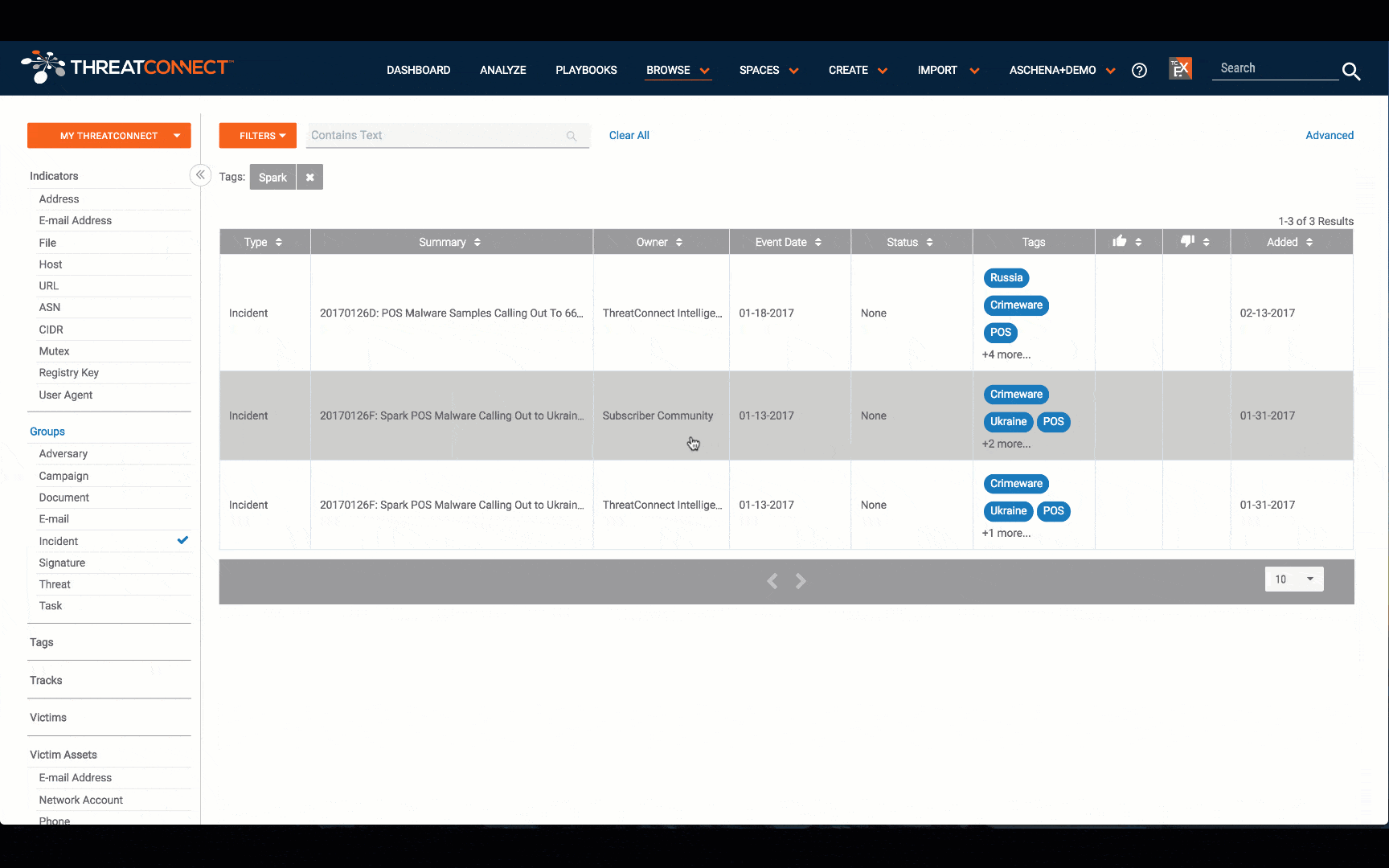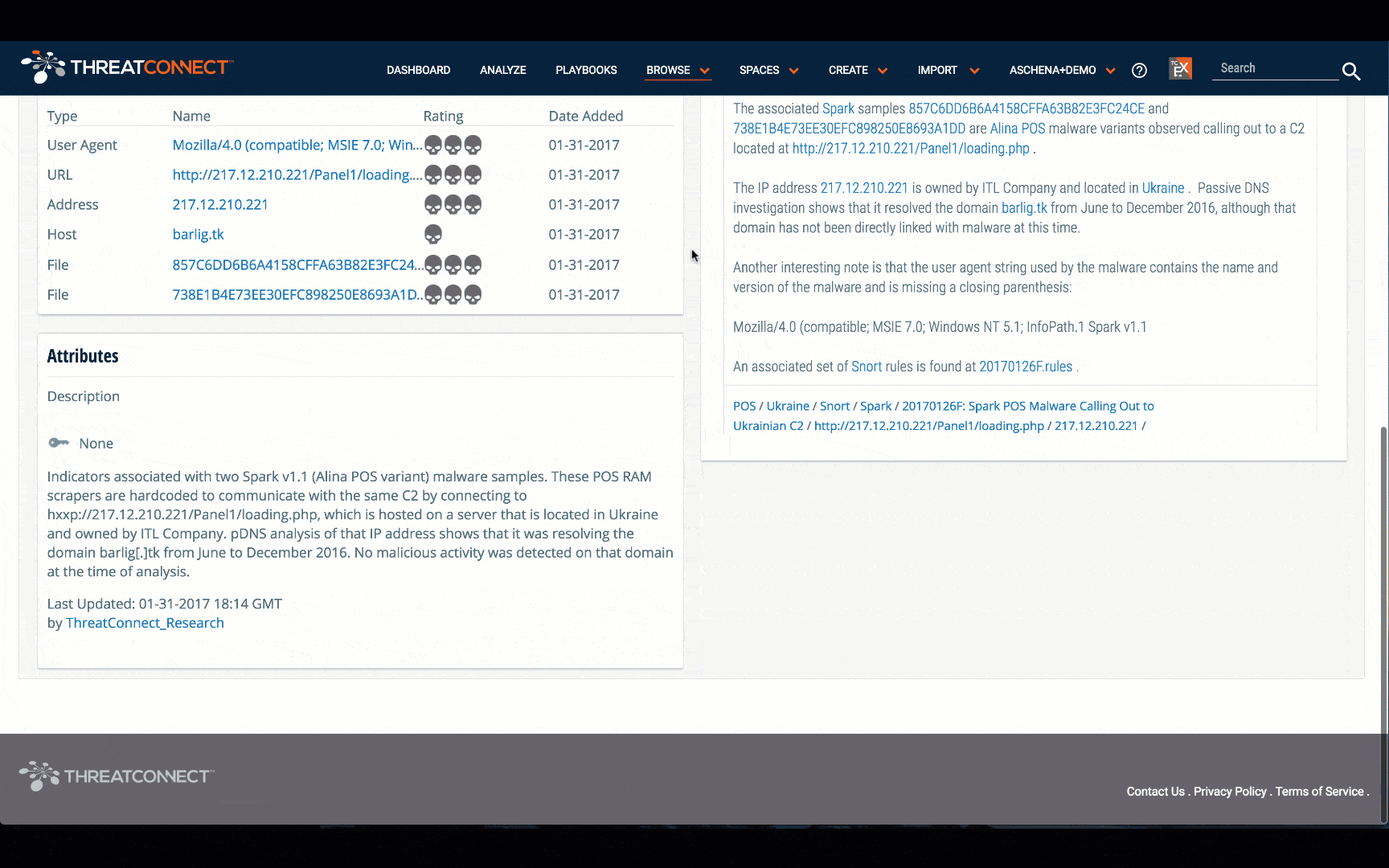
- 20170126F: Spark POS Malware Calling Out to Ukrainian C2
- 20170126D: POS Malware Samples Calling Out To 666approved[.]ru and approved666[.]pro
- 20161012C: Additional Infrastructure Related to Javascript Skimmer on NRSC Website
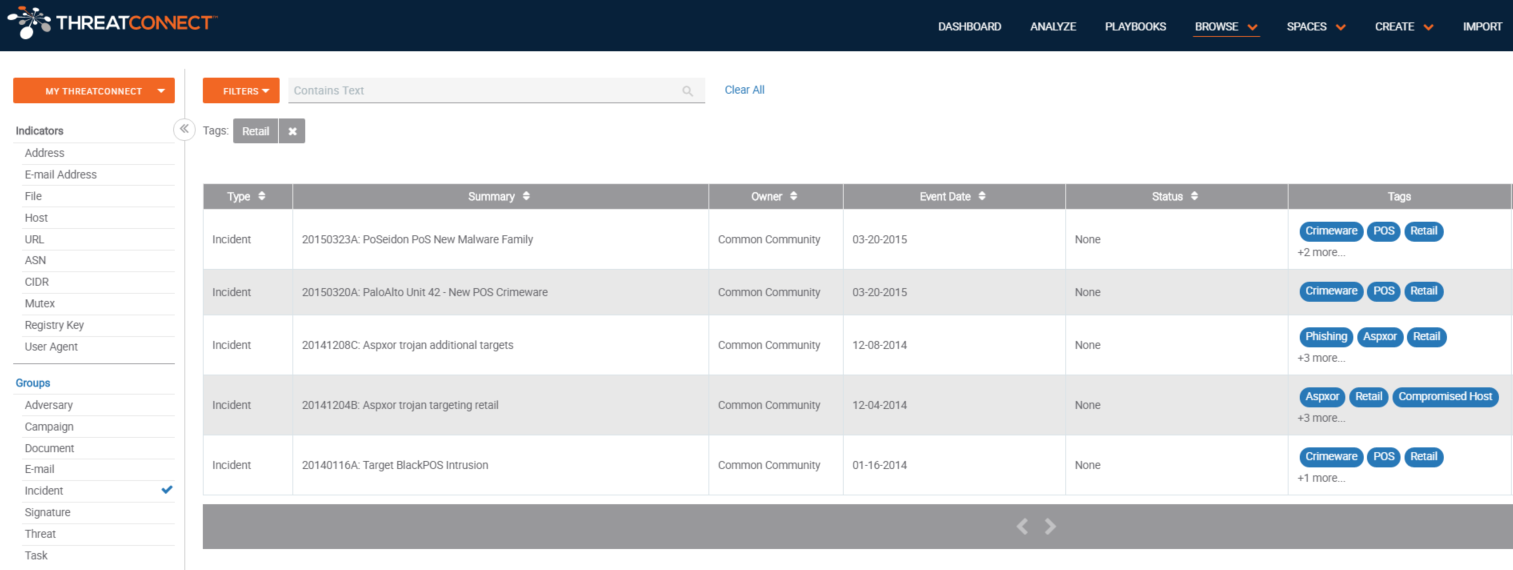
Communities
Communities are one of the best places to get vertical-specific data in the Platform. Communities in ThreatConnect are run by organizations that want to share, collaborate, and ask questions about threat intelligence or users with specific interests or assets. There are three Retail Communities in ThreatConnect – R-CISC Community, NRF Retail ISAO Community, and the Retail Industry Community. Members of R-CISC or of the NRF can join their communities and access the data being shared. Upon joining, follow a community to receive immediate or summary alerts of incidents or comments that get posted. This is an excellent way to get started with threat intel.
ThreatAssess and CAL™
Another great way to get more information about retail-specific threats is through ThreatConnect’s in-platform analytics. ThreatAssess is a score that represents the overall impact an indicator may have to an organization. ThreatAssess is derived from factors such false positives, whether it has been observed before, and whether it has been contributed from a single source or multiple. CAL™, or the Collective Analytics Layer, provides insight into what your peers are seeing on their network. When you are viewing the indicators mentioned above, you are able to see data such as: how many times it has been viewed by ThreatConnect users, how many times it has been marked false positive, or how many times it has been observed in other ThreatConnect user’s networks.
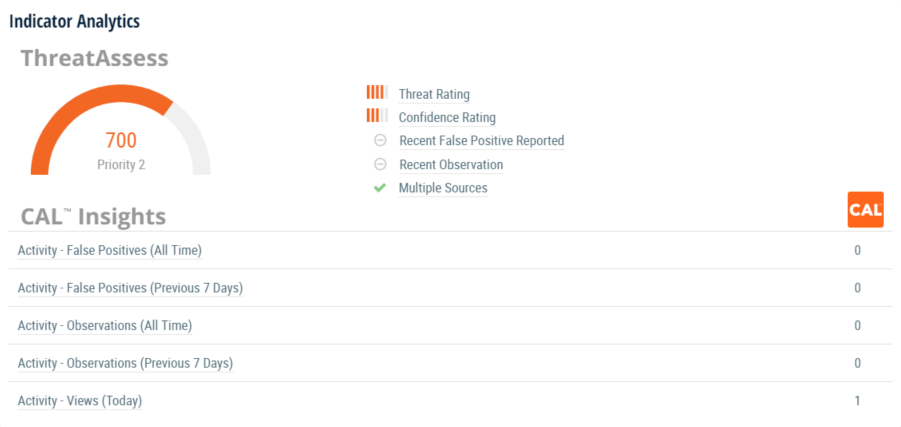
That’s lovely, but what can I do with this data?
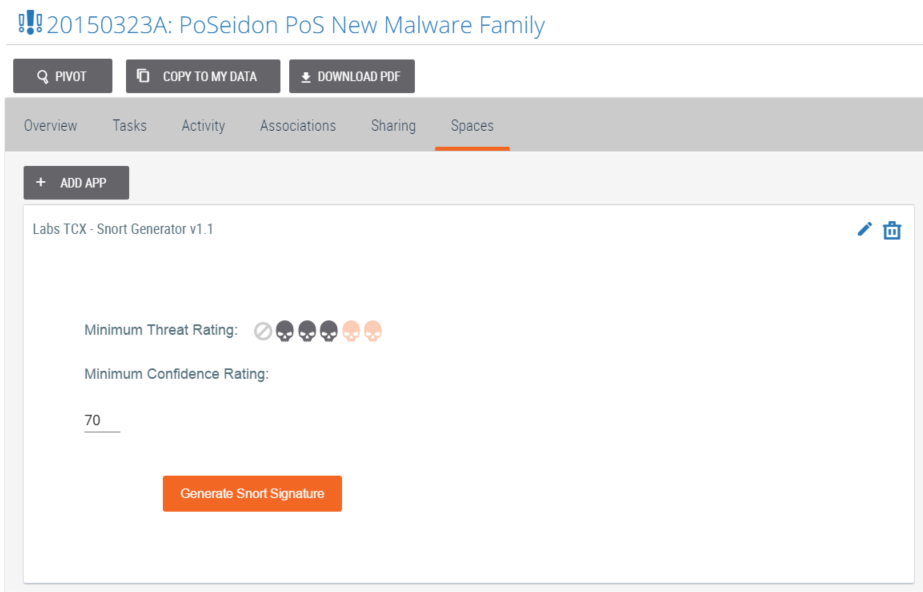
Snort Rules Downloads
It’s one thing to find relevant intel; it’s another to use it effectively. This is where ThreatConnect’s ‘Snort Generator’ app comes in handy. Once a ‘Browse’ search for the ‘Retail’ tag, and an incident is found, dive into the details of that incident. By clicking on the ‘Spaces’ tab for that incident, choose apps that can add additional context for the indicators associated with the incident. Once the Snort Generator App is downloaded, Snort signatures can be generated for the associated indicators and then exported and applied for network defense.
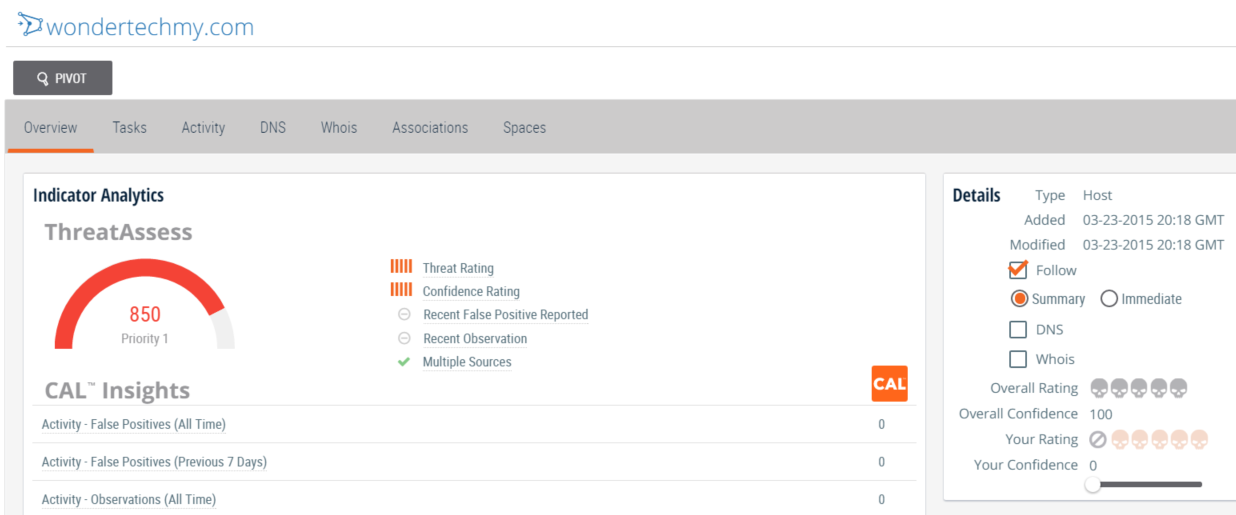
Track Indicators of Interest
As with communities, indicators can also be followed. Why would one do that when alert fatigue already exists? Following an indicator of interest in ThreatConnect, for example, a host, will send an immediate or summary of email alerts if that host calls out to a new IP address or changes its DNS resolution. This helps track adversaries and get ahead of the threat.
Investigation Links
‘Investigation Links’ bring multiple, third party enrichment services and solutions together on a specific indicator to receive additional context, which saves a lot of time. Analysts are able to more efficiently determine the criticality of an indicator.
Simplifying the Complex
In The Hitchhiker’s Guide to the Galaxy, Douglas Adams writes “Space is big. Really big. You just won’t believe how vastly, hugely, mindboggling big it is.” Similarities can be drawn to the continual complexity of the cybersecurity universe, from the copious amounts of threat data and lack of context, to the number of adversaries and evolving TTPs leading to new vulnerabilities. It’s difficult to figure out what data is relevant to you and your organization.
A security analyst can be effective without a platform to investigate threat data, but not as efficient. ThreatConnect helps simplify the intricacies of cybersecurity by making it easier to find relevant threat intelligence for retailers.
But that is just the tip of the iceberg. Not only can retailers search ThreatConnect for retail-specific threat data and threat intelligence, but can begin to use that information in their security program. ThreatConnect allows you to take actions like creating automated playbooks, analysis or remediation of any relevant threat data, and sending relevant data to your security tools using ThreatConnect’s API. Whether you are a small shop just starting with threat intelligence or a large retail corporation looking to grow your security program, ThreatConnect can help.

