Posted
ThreatConnect Playbook Actions: Be More Efficient and Gain Control with Automated Actions
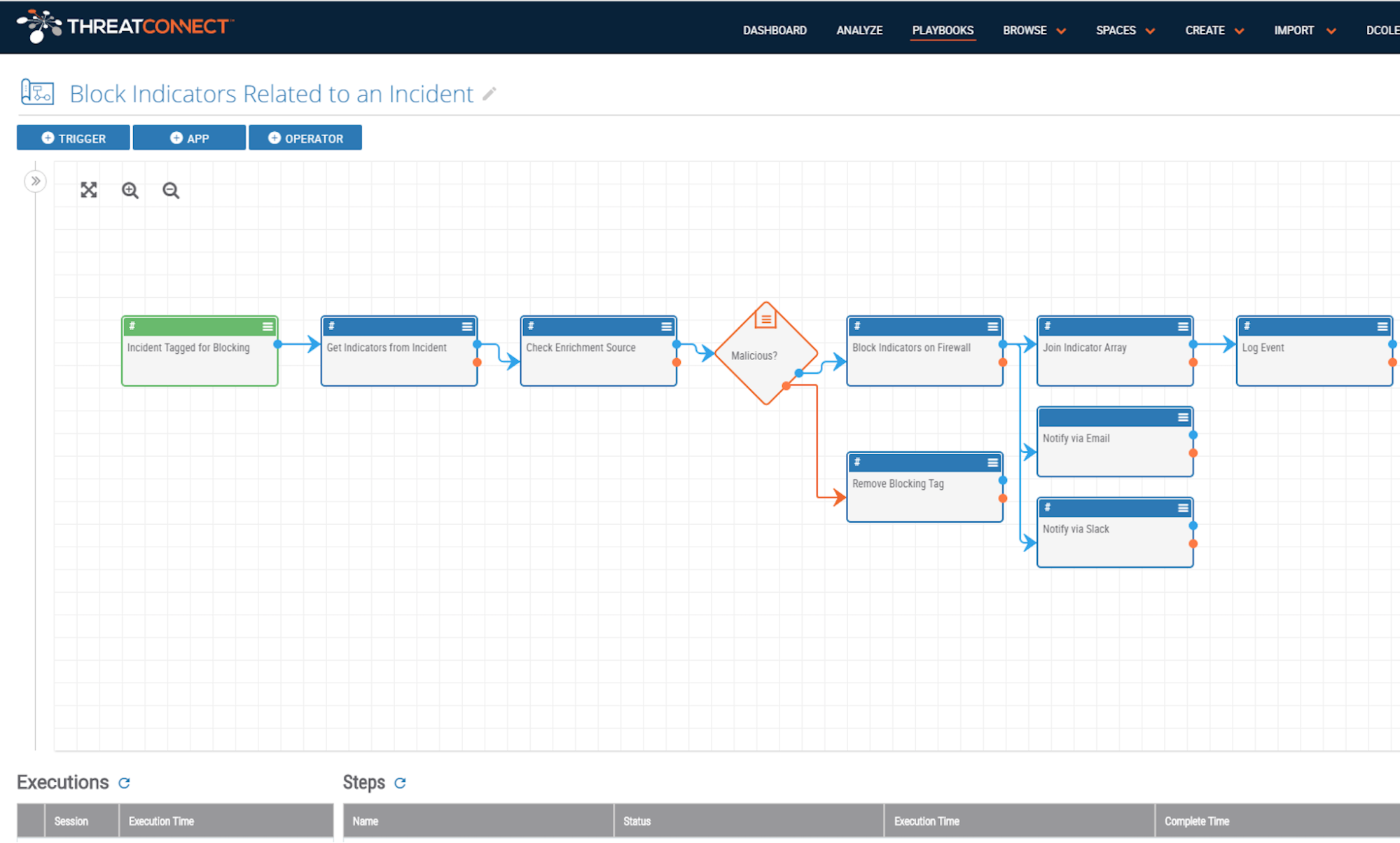
ThreatConnect’s Playbooks feature automates almost any cybersecurity task using an easy drag-and-drop interface – no coding needed. ThreatConnect uses Triggers (e.g., a new IP address Indicator, a phishing email sent to an inbox) to pass data to apps, which perform a variety of functions, including: data enrichment, malware analysis, and blocking actions.
Run Playbooks Directly from Your Threat Intelligence
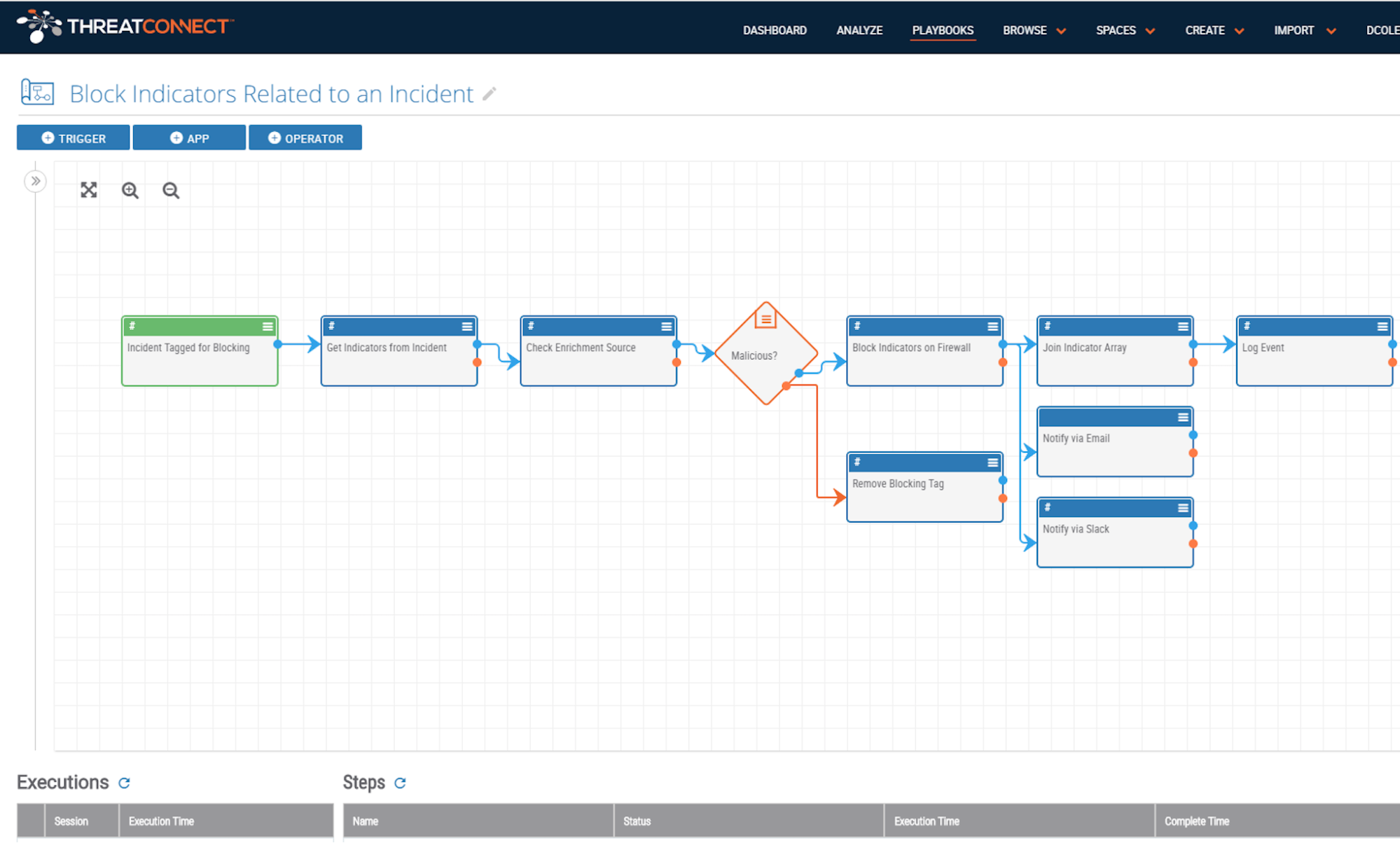
Take this one step further with Playbook Actions, which let users create Playbooks that can be kicked off directly from Indicators (Host, Address, etc.) and Groups (Incidents, Tasks, etc.) in the Platform. This gives users unprecedented control to put powerful new functionality directly into the Platform without coding or installing new updates.
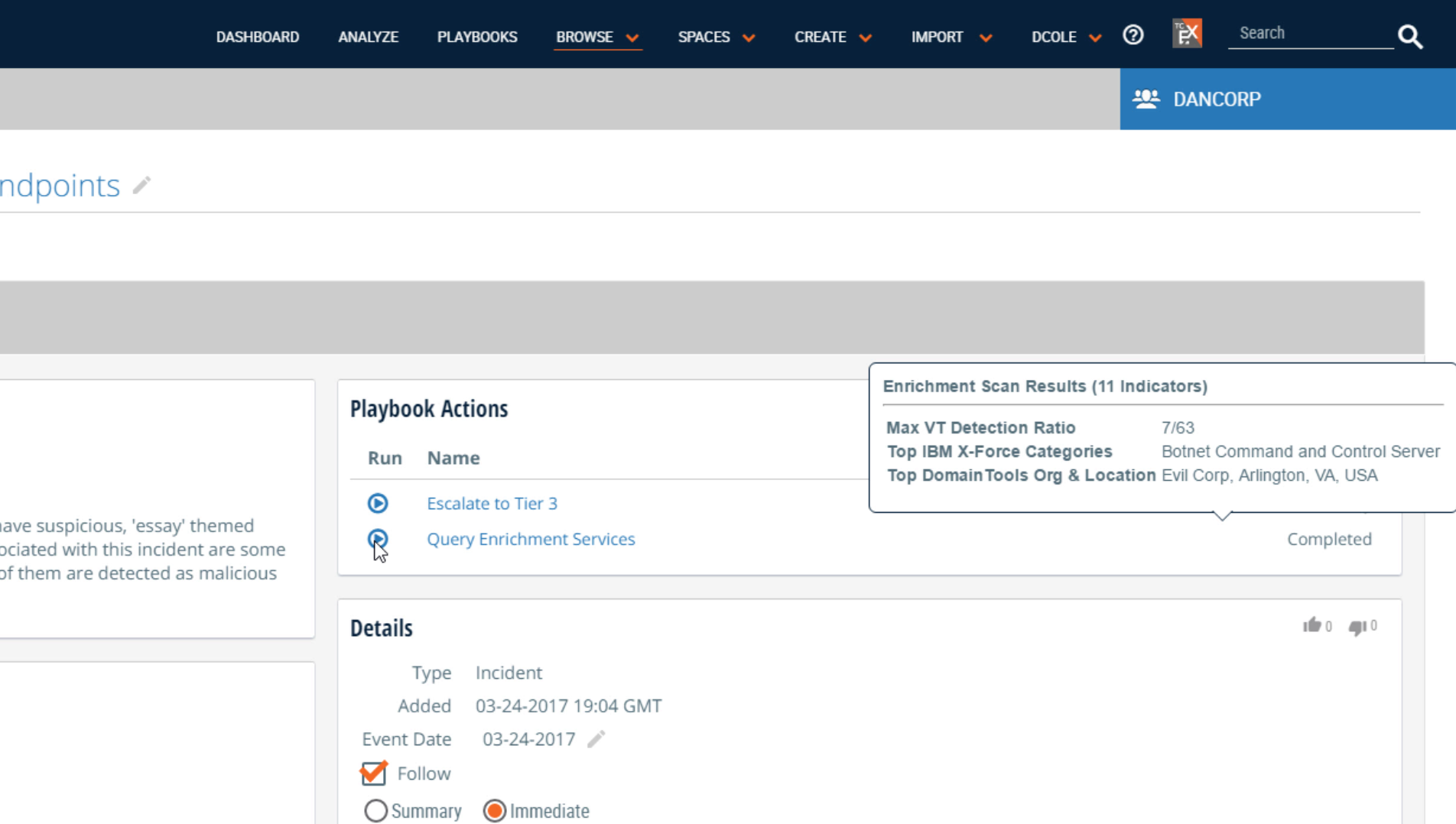
Intel-driven responses that used to take 10+ steps can now be completed in one. That’s a tenfold decrease in potential errors and a tenfold increase in efficiency! Want to block all IPs tied to an incident? One click. Want to add dozens of fields of enrichment data to an indicator? One click. Want to notify your team of a critical alert? One click.
To see Playbooks Actions in, well, action, check out this video: