Why Speed Fails Defenders
Analysts burn out because half of what they investigate is noise — false positive, duplicates, and stale signals. Instead of focusing on volume and speed, focus on true risk reduction.
62% of SOC alerts are disregarded outright because teams can’t prioritize effectively.
55% of teams admit they’ve missed critical alerts due to ineffective prioritization.
84% of security professionals report feeling burned out from alert volume and workload.
The Three Questions That Matter
Instead of asking “how fast did we close this alert?” defenders should ask:
- Was the decision correct, or did we accelerate a mistake?
- Does this alert carry enough context to prove it’s real?
- Did acting (or not acting) reduce measurable risk to the business?
When these questions drive triage, alerts become part of defense — not just a box-checking exercise.
A New Definition of “Done”
- Automation takes manual review off the table, so analysts stop copy-pasting and start investigating
- Prioritization reflects adversary campaigns and modeled financial impact.
- Executives see triage as ROI — risk reduced, not tickets closed.
- Analysts focus on decisions that matter, not on proving speed.
Align Alert Triage with Risk Reduction Impact
Our approach shifts alert triage from activity metrics to outcome metrics through three capabilities:
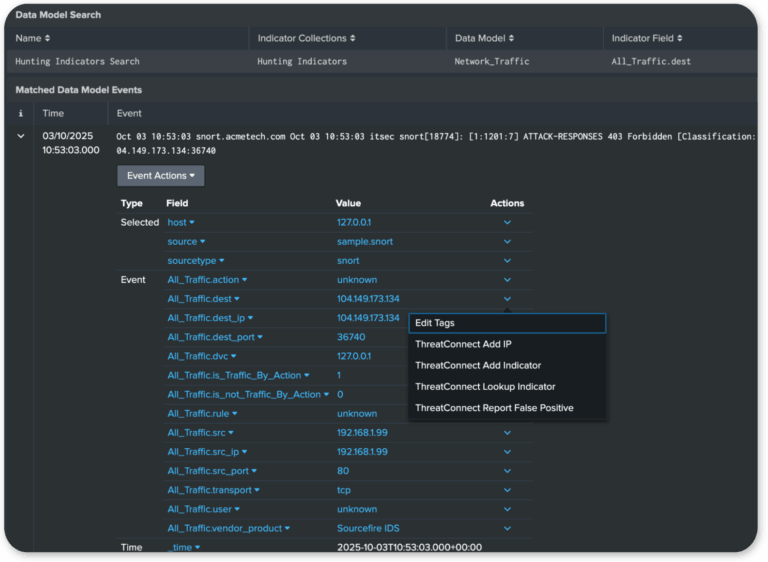
Contextualize
Automatically enrich and score alerts with so real threats stand out, deduplicate repeats, and suppress known false positives so analysts begin with clarity, not chaos.
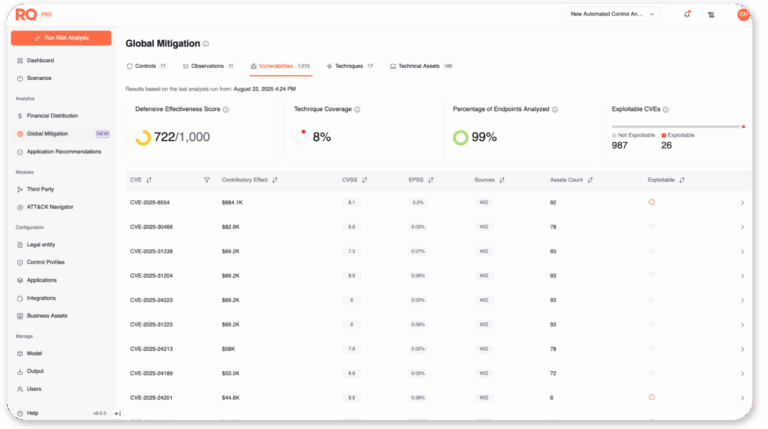
Prioritize
Score high-priority alerts based on exploit likelihood and modeled business impact, ensuring analysts spend time on what can hurt most.
Act & Adapt
Push enriched alerts into triage workflows, automate escalations and reporting, and capture analyst feedback so the system learns and improves over time.
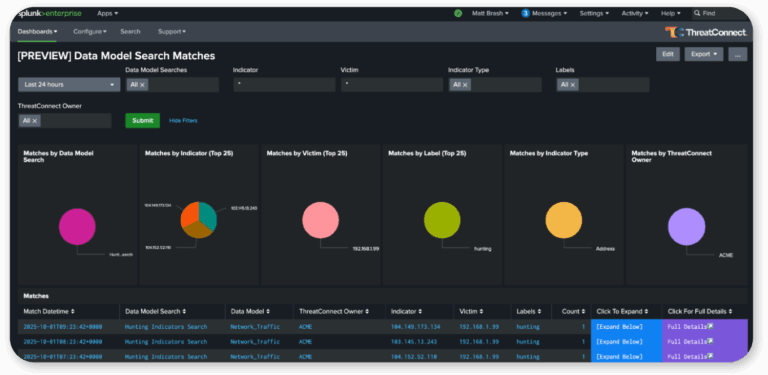
Getting Started
- Push high-fidelity intel to the SIEM – Reduce false positives at the source by enriching IoCs and TTPs with threat scores before they generate alerts. “Fewer, higher-quality alerts means less analyst fatigue.”
- Deliver context in the workflow – Overlay campaign and actor context directly in Splunk, Sentinel, QRadar, and other tools. “No more copy-pasting between tools.”
- Automate escalations – Playbooks handle deduplication and ticket creation in ServiceNow/Jira. “Analysts spend less time updating tickets and more time investigating.”
Grow With Us
- Prioritize by financial risk
Layer in risk quantification so alerts are ranked by modeled business impact. “Which alerts could actually cost you millions if ignored?” - Continuously measure and learn
Track decision accuracy, false positives avoided, duplicates suppressed, and MTTR. Feed analyst feedback into playbooks. “Are you reducing noise week over week—and proving risk reduction?”
Only in ThreatConnect
Cut false positives at the source
Automatically suppress duplicates and irrelevant alerts, reducing noise and analyst fatigue before an investigation even begins.
Automate triage workflows
Pre-built playbooks streamline enrichment, escalation, and reporting so analysts don’t waste time on manual copy-paste.
Context where you work
Overlays bring actor, campaign, and asset context directly into Splunk, Sentinel, QRadar, and ServiceNow. No swivel-chairing, no integrations required.
Tie alerts to real business impact
Connect alerts to modeled financial loss, shifting triage success from “tickets closed” to “risk reduced.” Executives finally see ROI, not just activity metrics.
Close the feedback loop
Analyst decisions captured at the point of action feed back into playbooks, so every triage cycle gets smarter.
Powered by the Intel Hub
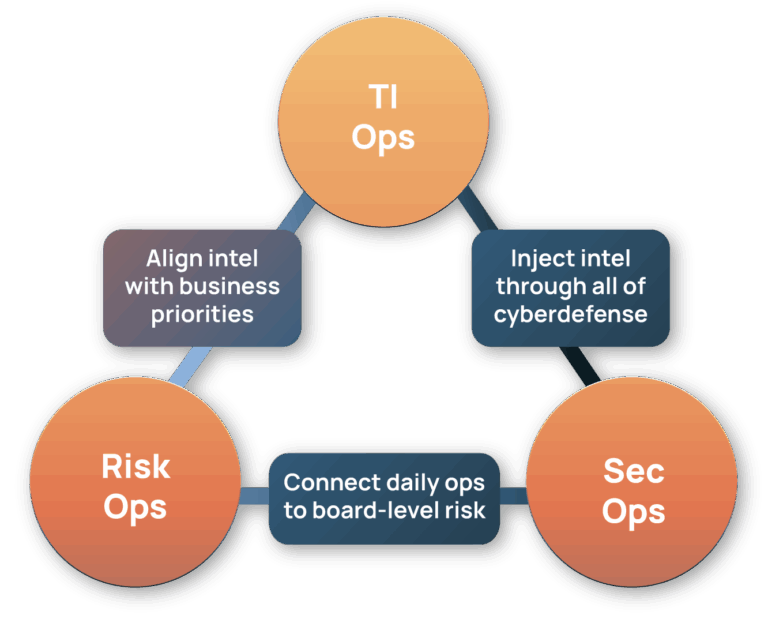
TI Ops
Enrich and structure alerts with ATT&CK mapping and ground-truth insights from our global analyst network.
Polarity
Deliver context overlays into workflows without switching tools.
Risk Quantifier
Prioritize alerts by modeled financial impact.