If Traditional Approaches Worked, Why Do We See:
180% YoY spike in attackers exploiting vulnerabilities.
75% surge in cyberattacks in just one year.
84% of security pros worry about missing threats because of data overload.
Only 28% of teams use threat intel to inform budgets and priorities.
Introducing the Intel Hub
Don’t Just Gather Intel – Decide What Deserves Action
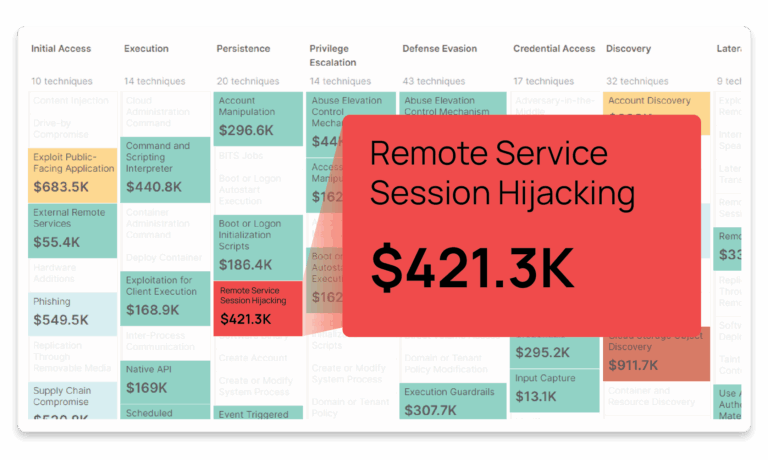
Pinpoint Your Financial Exposures
Based on your unique assets and company profile, the Intel Hub identifies the ATT&CK techniques and vulnerabilities that represent the highest financial risk to your organization.
Surface Targeted Intelligence
AI sends insights relevant to those high risks to our threat intelligence platform (TIP) for investigation and prioritization.
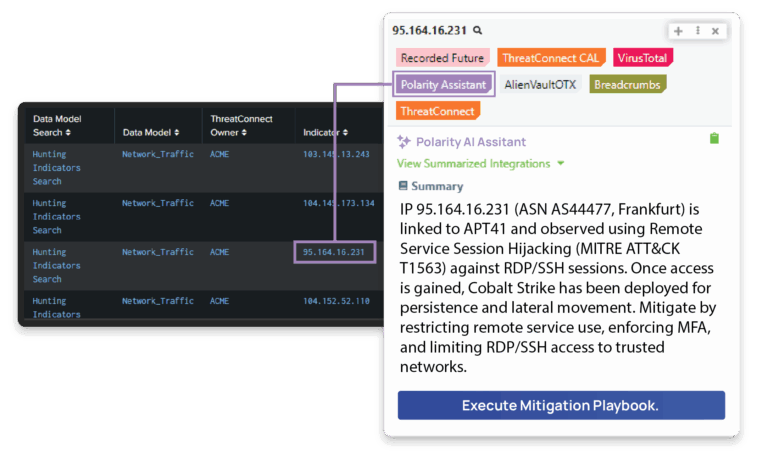
Take Action to Eliminate Exposures
Operational teams receive intel on high-risk threats without leaving their favorite tools, with automated mitigation playbooks ready to go.
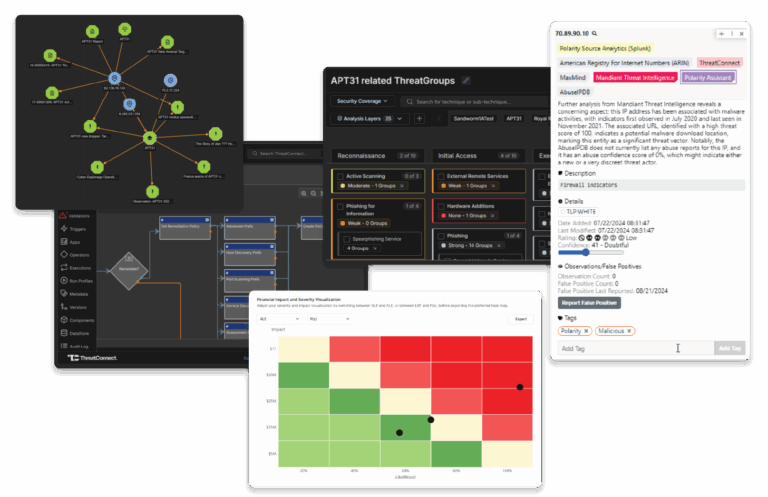
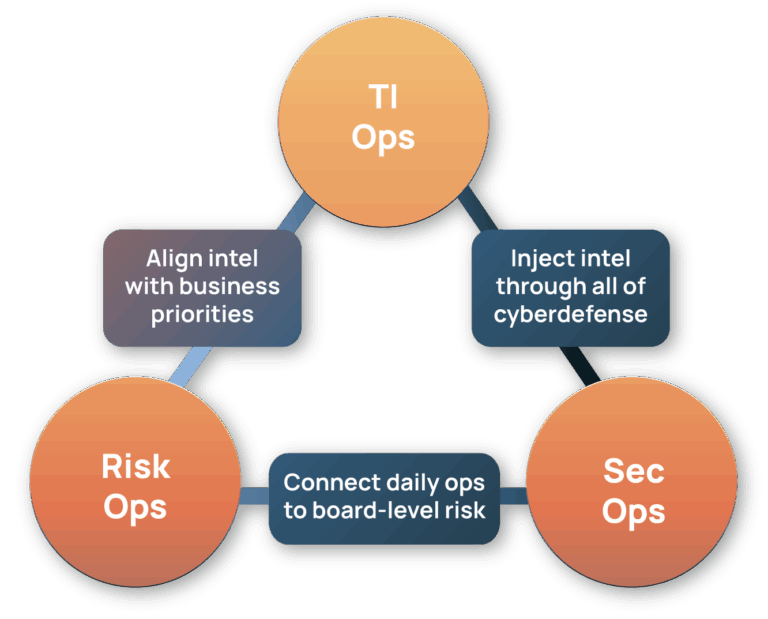
The Only Platform Built for Threat and Risk-Informed Defense
AI-curated intelligence requirements remove noise and focus your teams on relevant threats.
Cyber risk quantification bridges the gap between those who assess risk and those that mitigate it.
Risk-weighted ATT&CK models show business-specific adversary paths.
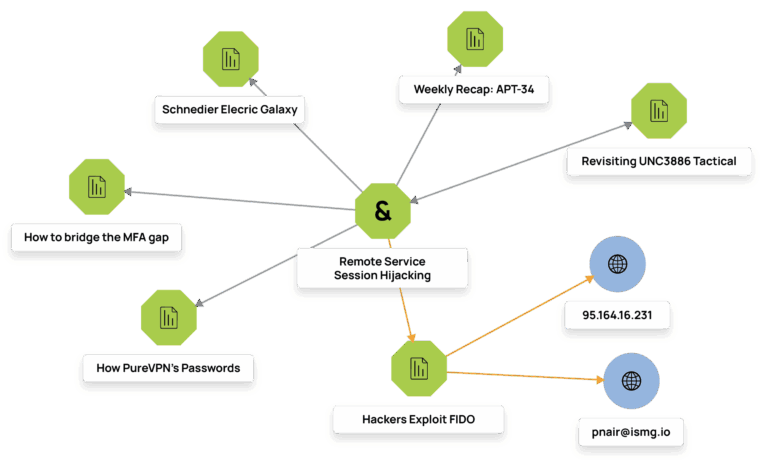
Crowdsourced enrichment delivers unique intelligence from a global analyst community.
Overlay intel into any tool for instant context.
Playbooks and low code automation streamline and accelerate defensive actions.
Agentic AI adapts workflows based on outcomes, ensuring continuous improvement.
98% of customers report ThreatConnect is critical to their operations
With the Intel Hub, response times shrink, analyst burnout drops, and your defenses evolve continuously.
Operational Effectiveness
97% report improvements in the effectiveness of operational tools like SIEMs, SOARs, and EDRs
Time Savings
90% report time savings > 50%
MTTR
67% report > 50% reduction in MTTR
False Positives
63% say that ThreatConnect reduced their false positive rates
Collaboration
79% report that ThreatConnect improves collaboration between teams
Immediate Impact, Long Term Defense
Getting Started
Start turning threat, risk, and security intel into strategic priorities:
- Connect your existing intel feeds and upload your business asset inventory.
- Map threats to MITRE ATT&CK and identify your top-risk TTPs fast.
- Push curated IoCs and intelligence into your SIEM or EDR for immediate protection.
- Deploy Polarity overlays to deliver context into the tools your analysts already use — with zero integrations.
Grow With Us
Close exposure gaps with full threat and risk-informed defense:
- Build business-specific threat models tied to revenue-generating services.
- Quantify cyber risk in financial terms for board-level reporting and budget planning.
- Automate response playbooks across detection, triage, and remediation.
- Integrate continuous feedback loops to refine intelligence and detection engineering over time.
- Empower proactive threat hunting guided by business risk insights.
Works with the Tools You Already Have
The Intel Hub integrates with:
Push vetted IOCs and TTPs into correlation and detection rules
Enrich alerts in real time with context and scoring
Reduce false positives and accelerate triage

Trigger playbooks directly from intel signals or overlays
Feed risk and threat scoring into incident workflows
Capture analyst decisions to improve automation logic

Correlate endpoint detections with adversary TTPs
Prioritize and act on alerts based on business impact
Block threats confidently with high-fidelity intel

Tie vulnerabilities to active adversary campaigns for prioritization
Highlight exposures with the highest financial impact
Map controls and assets for enterprise-wide visibility

Associate users, devices, and assets to uncover risky access paths
Quantify identity-driven threats and prioritize remediation

Ingest firewall, NDR, and data lake telemetry to model exposure
Correlate traffic patterns with adversary techniques
Provide actionable insights across workloads and cloud environments






Trusted By Leading Companies
ThreatConnect allows our organization to collect, analyze, and share intelligence with various teams in a single platform, effectively reducing the amount of time needed for an analyst to produce actionable intelligence to share with our partners and stakeholders.
ThreatConnect enabled us to quantify ROI and to define business requirements for onboarding technology. Tools need to be open to automation, scalable, and reliable
ThreatConnect is a one stop shop for me. I can get intel, risk, and deep dive into threats and source, all in one place.
ThreatConnect has a vision for security that encompasses the most critical elements – risk, threat, and response. The RQ solution strengthens their offering and increases alignment to our core strategic objectives with one platform to assess our risk and automate and orchestrate our response to it.